Part 7 of 19 – Migration and Deployment - Upgrade Implications for Active Directory - (Windows Server 2008 to Windows Server 2012)
When we look at upgrading our existing infrastructure to the latest Windows Server edition we always have to consider the implications when upgrading Active Directory. The first thing you need to plan for is what you are wanting to accomplish in your new migration.
This post provides background information about Active Directory Domain Services in Windows Server 2012 and explains the process for upgrading domain controllers from Windows Server 2008 or Windows Server 2008 R2.
- What’s new in AD DS in Windows Server 2012?
- AD DS server role installation changes
- Deprecated features and behavior changes related to AD DS in Windows Server 2012
- Supported in-place upgrade paths
- Functional level features and requirements
The best place to start is to consider the in place-upgrade scenarios and what can be accomplished in your move.
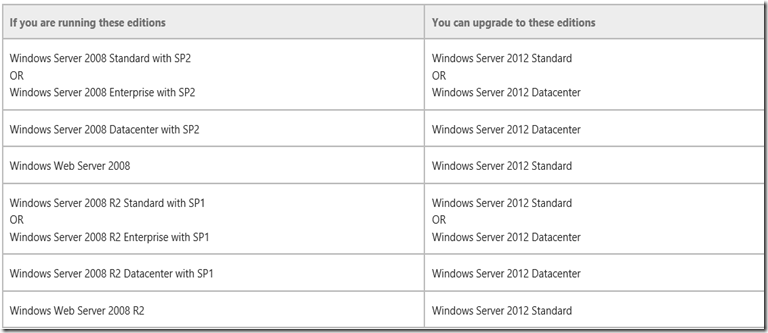
YES – You can upgrade domain controllers that run 64-bit versions of Windows Server 2008 or Windows Server 2008 R2 to Windows Server 2012.
NO - You cannot upgrade domain controllers that run Windows Server 2003 or 32-bit versions of Windows Server 2008.
To replace them, install domain controllers that run Windows Server 2012 in the domain, and then remove the domain controllers that Windows Server 2003.
If you are running these editions
You can upgrade to these editions
See Evaluation Versions and Upgrade Options for Windows Server 2012.
AD DS server role installation changes
In Windows Server 2003 through Windows Server 2008 R2, you ran the x86 or X64 version of the Adprep.exe command-line tool before running the Active Directory Installation Wizard, Dcpromo.exe, and Dcpromo.exe had optional variants to install from media or for unattended installation.
In Windows Server 2012, command-line installations are performed by using the ADDSDeployment Module in Windows PowerShell. GUI-based promotions are performed in Server Manager using a completely new AD DS Configuration Wizard.
To simplify the installation process, ADPREP has been integrated into the AD DS installation and runs automatically as needed. The Windows PowerShell–based AD DS Configuration Wizard automatically targets the schema and infrastructure master roles in the domains where Windows Server 2012 DCs are being added, then remotely runs the required ADPREP commands on the relevant domain controllers.
Prerequisite checks in the AD DS Installation Wizard identify potential errors before the installation begins. Error conditions can be corrected to eliminate concerns from a partially complete upgrade. The wizard also exports a Windows PowerShell script that contains all the options that were specified during the graphical installation.
Taken together, the AD DS installation changes in Windows Server 2012 simplify the DC role installation process and reduce the likelihood of administrative errors, especially when you are deploying multiple domain controllers across global regions and domains.
More detailed information on GUI and Windows PowerShell-based installations, including command line syntax and step-by-step wizard instructions, see Install Active Directory Domain Services. For administrators that want to control the introduction of schema changes in an Active Directory forest independent of the installation of Windows Server 2012 DCs in an existing forest, Adprep.exe commands can still be run at an elevated.
Let’s take a look at Deprecated features and behavior changes related to AD DS in Windows Server 2012
There are some changes related to AD DS:
- Deprecation of Adprep32.exe
There is only one version of Adprep.exe and it can be run as needed on 64-bit domain controllers that run Windows Server 2008 or later. It can be run remotely, and must be run remotely if that targeted operations master role is hosted on a 32-bit operating system or Windows Server 2003.
- Deprecation of Dcpromo.exe
Dcpromo is deprecated although in Windows Server 2012 only it can still be run with an answer file to give organizations time to transition existing automation to the new Windows PowerShell installation options.
- LMHash is disabled on user accounts
Secure defaults in Security templates on Windows Server 2008, Windows Server 2008 R2 and Windows Server 2012 enable the NoLMHash policy which is disabled in the security templates of Windows 2000 and Windows Server 2003 DCs. Disable the NoLMHash policy for LMHash-dependent clients as required, using the steps in KB article 946405.
You can get all the information on issues and other main areas of migrations and upgrades by going to: https://technet.microsoft.com/en-us/library/hh994618.aspx#BKMK_UpgradePaths
if you are new to the product then download the latest bits at: https://aka.ms/msproducts