Endpoint policies galore
If you have a freshly installed UAG server in front of you, you might be considering which Endpoint policies to set for your applications. UAG comes with no less than 27 built-in predefined policies just for Windows computers (plus another 34 policies for Mac and Linux), but their naming doesn’t always indicate what they actually do. Technically, it’s quite easy to see it by opening each one and seeing, but I’d like to save you some of that time. Here are all the policies, and their default configuration:
Default Non Web Application Access
This policy contains the default “Any Anti Virus” policy, which requires the endpoint to have any AV product installed, updated and running. Any AV that is supported by the Windows Security Center (Action center in Windows 7) would meet that sub-policy. In addition, this policy requires that the computer meets the certified endpoint policy, or the corporate machine policy, or the privileged endpoint policy, or have the endpoint cleanup component installed and running.
Default Privileged Endpoint
This policy requires that the computer meets the policies defined as “privileged endpoint” on the trunk.
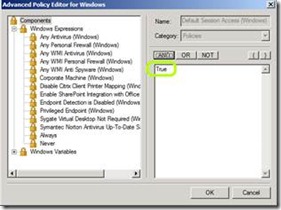
Default Session Access
This policy has no requirements
Default Web Application Access
This policy has no requirements
Default Web Application Download
This policy requires that the computer meets the certified endpoint policy, or the corporate machine policy, or the privileged endpoint policy, or have the endpoint cleanup component installed and running.
Default Web Application Restricted Zone Access
This policy has no requirements
Default Web Application Upload
This policy contains the default “Any Anti Virus” policy, which requires the endpoint to have any AV product installed, updated and running.
Microsoft CRM 4 Upload
This policy has no requirements
Microsoft CRM 4 Download
This policy has no requirements
Microsoft CRM 4 Enhanced Security
This policy has no requirements
Microsoft OWA 2010 Download
This policy has no requirements
Microsoft OWA 2010 Upload
This policy has no requirements
Microsoft Office SharePoint Portal Server 2003 Admin Zones
This policy has no requirements
Microsoft Office SharePoint Portal Server 2003 Download
This policy has no requirements
Microsoft Office SharePoint Portal Server 2003 Enhanced Security
This policy has no requirements
Microsoft Office SharePoint Portal Server 2003 Upload Checkin
This policy has no requirements
Microsoft Office SharePoint Server 2007 Download
This policy has no requirements
Microsoft Office SharePoint Server 2007 Upload CheckIn
This policy has no requirements
Microsoft Office SharePoint Server 2007 Enable Explorer View
This policy has no requirements
Microsoft SharePoint Server 2010 Download
This policy has no requirements
Microsoft SharePoint Server 2010 Upload
This policy has no requirements
OWA Private Computer
This policy requires that the computer meets the policies defined as “privileged endpoint” on the trunk.
Microsoft OWA 2007 Download
This policy has no requirements
Microsoft OWA 2007 Upload
This policy has no requirements
Always
This policy has no requirements
Never
This policy is set to block all access
As you can see, most of the default policies do not actually have any requirements. They simply include the text “true”, which means that the policy will evaluate to “pass” no matter what the endpoint parameters are:
If you’re asking yourself what is the purpose of having the many policies, with so many of them having no requirements or being identical, the answer is that the policies come in groups, and every top-level group has to have the full set. For example, the Default Web Application policy has to have the four sub policies of Access, Upload, Download and Restricted zone. Even though the Access and Restricted Zone are identical and have no requirements, we still have to have them to complete the Default Web Application policy.