Block by block
A useful feature with IAG is the ability to block file uploads and downloads, which can be enforced based on various parameters, like file extension, size and more. While this seems pretty straight forward, as each application has an Upload/Download settings page, this may be confusing and some users try to set it and are not sure why their files are not being blocked.
To really understand how this works, It's important to realize that it requires the administrator to configure two things:
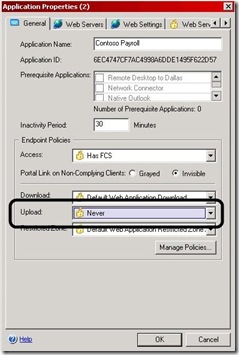
1) The application's Endpoint upload and download policy
2) The application's Download/Upload tab parameters
Many mistakenly think that setting just one of the above is enough. Here's a brief description of how this works:
1) The upload/download tab in the application properties is only used to identify the properties that will be used to determine what is considered an upload or download.
2) The selected endpoint policy is used to set what to do about the upload and download
Essentially, IAG looks at each file the user tries to upload or download with this application, and checks the upload/download policy against the properties of this file. If the file matches them, then it is classified as an upload or download, and the selected upload or download policy is applied to it. If that policy is set to TRUE, or an expression that amounts to a value of TRUE, then the Download/upload operation is allowed. If that policy is set to FALSE, or an expression that amounts to a value of FALSE, then the Download/upload operation is blocked.
Usually, an administrator wishes to block a file if the connecting user has not secured his computer, so they would choose a conditional policy like "Default Web Application Upload". This policy is set to TRUE if the user has an AntiVirus product that is installed, running and updated. If the AV is not installed, not running or not updated, the policy will fail (Be set to FALSE), and then the download will be blocked (Again, the block will only apply to a file that matches the parameters defined in the upload/download tab). By the way, this policy, even though it's named "upload", can be used to control a download as well, by selecting it as the download policy in the download policy drop-down. If the administrator just wants to block these downloads, all that needs to be done is to use the NEVER policy, which always amounts to FALSE.
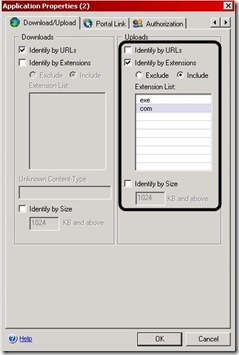
For example, the IAG administrator wants to block *.exe and *.com executables from being uploaded. The administrator needs to set the Upload Policy on the Application’s General tab to “Never”. Then set the Uploads settings on the Application’s Download/Upload tab to “Identify by Extensions” and select the "Include" radio button. In the extension list add on their own lines, exe and com (both without a dot before the extension). Make sure to uncheck Identify by URLs and Identify by Size or more potentially be blocked then you expect. This means that any other file types WILL be allowed.
Another example:
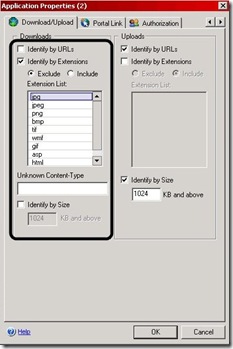
For example, the IAG administrator wants only common image files to be allowed to download. The administrator needs to set the download Policy on the Application’s General tab to “Never”. Then set the download settings on the Application’s Download/Upload tab to “Identify by Extensions” and select the "EXCLUDE" radio button. In the extension list add on their own lines the common image types (jpg, jpeg, gif, png, bmp etc), all without a dot before the extension. Also, the administrator must exclude the extension types used by the website itself, like asp, htm, html etc, otherwise, the site itself would not be allowed as the "never" policy selected will prevent these files from being accessed.
Many users need to enable this functionality in order to block OWA users from being able to download attachments, or include attachments if their endpoint does not meet a specific requirement, like an AV or Firewall. IAG Includes a settings that is very suitable for things of this nature. This setting is based on blocking a URL, rather than blocking by extension. The Download/upload tab has a setting for “identify by URL”. When this setting is checked, IAG will check the global download and upload URL settings, and use these to determine if the requested URL is indeed a download or upload, and if so, will apply the policy (to block, or allow) to it. An administrator can define anything he wants in the global Download/Upload URL settings, which are under Advanced Trunk Configuration/Global URL Settings/Download URLs and Upload URLs. Once an OWA application is created, these settings will be updated with the URLs that are used for downloads and uploads in OWA. For example, a download in OWA has this format:
/owa/attachment.ashx?attach=1&id=<something>
The download settings will include this expression:
/owa/attachment\.ashx\?(attach\=1)?(\&)?id=.*
Which will tell IAG to tag the URL with the downloaded attachment as a “download”, and if the download policy for OWA is set to FALSE, the attachment will be blocked. Similar settings can be set for other types of applications, provided you are able to correctly analyze the structure of the URL you want to block. This is not always easy, but with some careful planning, can provide with great security AND flexibility!
One last VERY important tip!
Some user define the policy correctly, but it still appears not to block anything. This usually happens because the application is set to “learn mode”. This is set in the application property, on the “Web Settings” tab. Learn mode is useful for early stages of an application implementation, but it will also cause IAG to ignore most of the security mechanisms, including the attachment blocking. Make sure it’s turned off to properly test upload/download blocking!