Policy Chase
With the introduction of SP2 for IAG, the process of creating custom endpoint detection policies has been slightly altered, as it now supports creating separate policies for Linux and Mac computers. Today I'll details a step by step guide to creating custom policies.
Before we continue, I'd like to point out that IAG comes with a pretty extensive set of pre-configured policies. For example, the "Default Non Web Application Access" policy checks for the existence of any of the supported Anti Virus, as well as other parameters like Certified Endpoint, IAG components installed and running etc. Another useful policy is "SecureView for OWA2003 SP1", which just checks for the existence of any anti-virus product to give access. Using custom policies, you can adjust the allowed endpoints with much details. You could, for example, allow your company's officially supported Anti-Virus, but not any others.
Here are the steps for creating a custom policy.
1. In the IAG configuration console, click on the trunk you want to apply the policy to.
2. Click on "advanced Trunk Configuration"
3. Switch to the "Session" page and click "Manage Policies" on the bottom-left.
4. Click "Add Policy"
5. Give your new policy a name and a description.
6. Click on "Manage Windows Policy"
7. Click "Add Policy"
8. Give your new policy a name and a description.
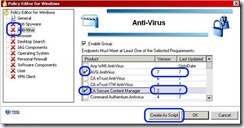
9. Click on one of the groups that is on the left, according to your desired configuration. For example, if you wish your new policy to allow access only to users running AVG Anti-Virus, click on the "Anti Virus" item.
10. Check "Enable Group"
11. Check any Anti-Virus product that you want to allow on the clients. You can select one, several, or "Any WMI Anti-Virus".
12. For any of the Anti-Virus products, you can change the minimum allowed version by double-clicking the relevant cell on the Version column, and changing the number to what suits your needs.
13. Similarly, you can change the required update period to a different number than the default 7 (1 week)
14. You can now click on another group, to add criteria for acceptance. For example, a popular requirement is to set only specific browsers or operating systems as permitted.
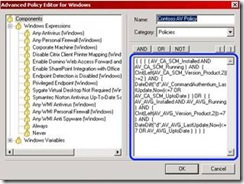
16. You may, at any point, click on "create as script", which converts the policy from a UI-based edit mode to a text-based edit mode. This could be useful for very fine-grain settings, like requiring two AV products. To do this, you need to change the syntax to requires AV1 AND AV2, rather than the regular syntax of AV1 OR AV2. Please keep in mind that this level of editing is tricky, and that once you convert the settings to script, you cannot change it back to a graphic-based editing mode.
17. Once you are done with editing the policy, click OK and click Close.
18. You are now back at the 1st policy settings page - you can now select your new policy from the drop-down selector that is under the "Select Platform-Specific policies" option.
19. If your organization hosts clients that are not running windows, use a similar procedure as outlined in steps 6-17 to create a policy for Mac OS, Linux and Other platforms. This is not mandatory - you can just set them to "Always" or "Never".
20. Click OK and Close
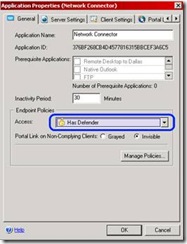
21. Now, the new policy is saved and available to be assigned. It can be assigned at the trunk level, or at the application level. For example, you could set it so that any anti-virus is allowed on the portal, but only people with Windows Defender can run the network connector: