Assess your System (Part 1of3) Microsoft Baseline Security Analyzer
Today I want to post about three very useful free tools from Microsoft which can assist you in automating the process of assessing your systems:
- MBSA (Microsoft Baseline Security Analyzer)
- SQL BPA (Best Practice Analyzer) for SQL 2000 and 2005
- Policy Management (automatically included in SQL 2008 and definitely more than just a tool to access your system vulnerability but I would define it as a management feature which allows to define and enforce policies for configuring and managing SQL Server across the enterprise)
Today we are starting with MBSA (latest version is 2.1 and can be downloaded from https://www.microsoft.com/downloads/details.aspx?FamilyID=F32921AF-9DBE-4DCE-889E-ECF997EB18E9&displaylang=en ).
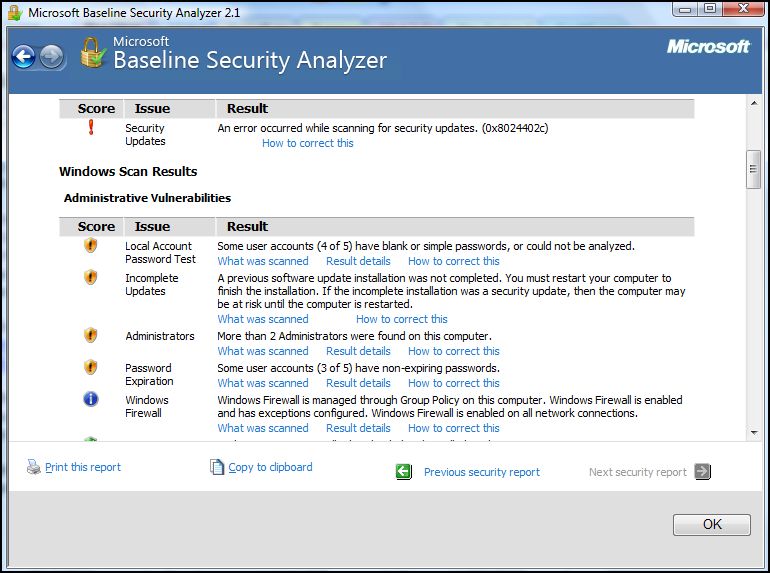
This tool gives you the ability to assess the administrative vulnerabilities present on one or multiple computers and then generates a report that contains details for each computer about the security checks that MBSA performed, the results, and recommendations for fixing any problems.
While BPA and PM are just looking at your SQL Server installation (Security+Best Practices), MBSA performs the following checks:
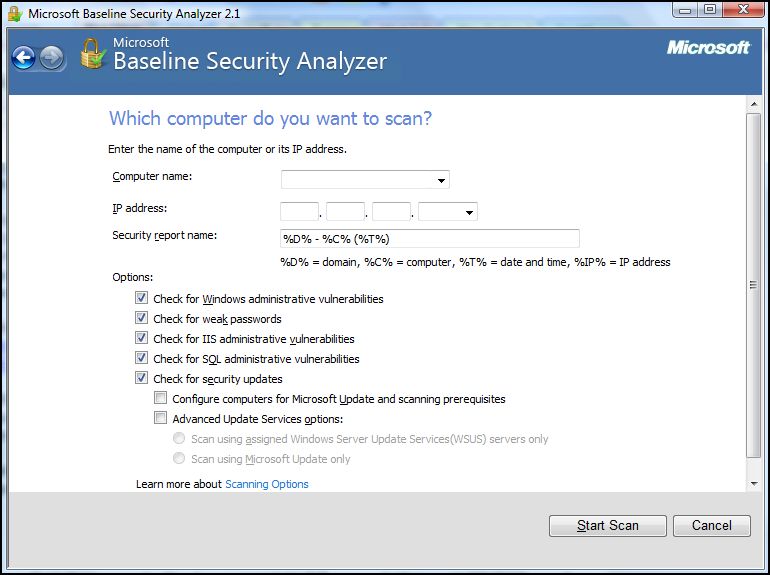
- Check for Windows administrative vulnerabilities
Scans for problems with the way that Windows is configured on the target computer.
- Check for weak passwords
Tests the passwords of local user accounts to determine whether any are blank or have other problems that might allow them to be guessed easily.
- Check for IIS administrative vulnerabilities
Checks for Internet Information Services (IIS) administrative vulnerabilities. When scanning servers running IIS, the computer running MBSA must have the Common Files installed for the highest version of IIS to be scanned.
- Check for SQL Server administrative vulnerabilities
Checks for administrative vulnerabilities on each instance of Microsoft SQL Server, Microsoft Data Engine, or Microsoft SQL Server 2000 Desktop Engine (MSDE) running on the target computer.
- Check for SQL Server administrative vulnerabilities
Checks for missing Microsoft Windows and Microsoft Office updates.
At startup, you can specify which of these options you want to check:
Results are stored on the computer on which MBSA is installed, in the SecurityScans folder of the user's profile (%userprofile%\SecurityScans) by default.
If you want to schedule MBSA scans, or have a standardised set of options to scan, there is a command line version included in the download, called mbsacli.
Running this tool on your systems, at least once every 6 months, is a recommended best practice and will help you maintain your systems secure. Personally, I would advice - prior to scan - always check if a new version has been released on the Microsoft Website.
- Beatrice Nicolini -