New Microsoft 365 Business Capabilities – Microsoft Intune Enhancements
This post is a little different to the previous ones in this series, because it's focused on the additional capabilities that are now licensed with the included Microsoft Intune. The main technical difference is now you are also licensed for iOS and Android Mobile Device Management (MDM), rather than only having Mobile Application Management (MAM) on those platforms. You also get MacOS MDM support, important for those managing mixed environments. The other big benefit for those that already know Intune or the Azure portal is that you don't have to think about whether or not you are using Microsoft 365 Business within the boundaries of its Intune licensing which was originally the case. Let's take a look at the iOS and Android enhancements first.
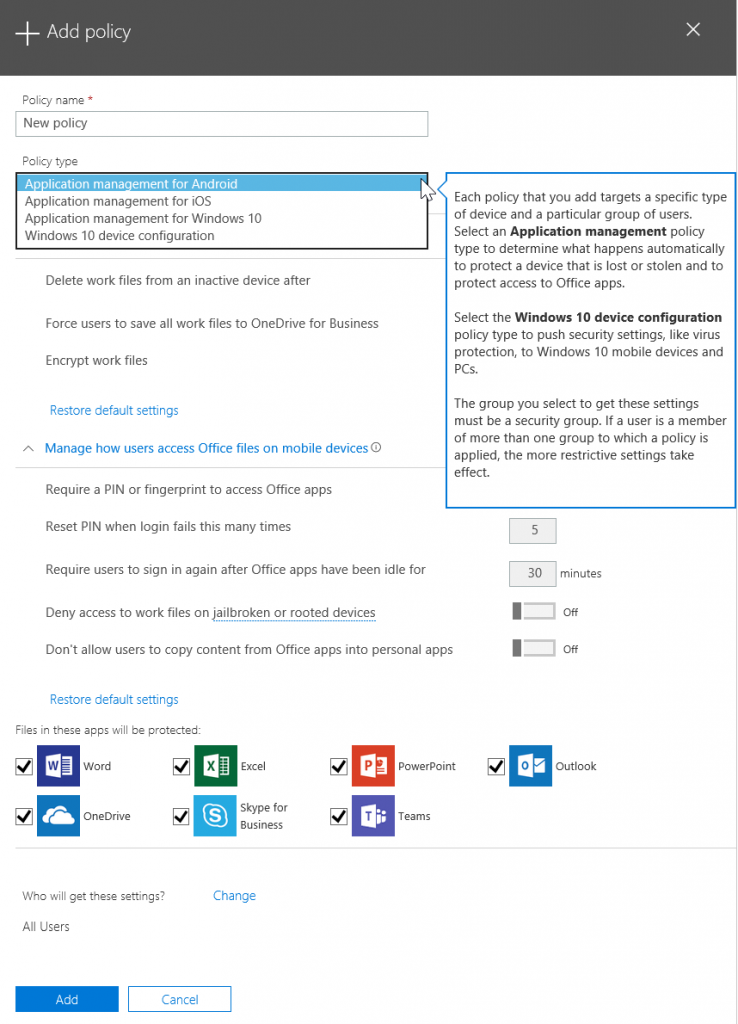
Up until this update for Microsoft 365 Business, iOS and Android devices could not be managed directly, but Azure Active Directory based identity and Microsoft Intune's MAM capability allowed the management of Office mobile apps through the Admin Center. For BYOD scenarios, this is a great solution, as it means your device isn't being managed by your employer, instead they only have management capabilities of the work profile within the supported mobile apps. This means that you don't have to be concerned about an admin doing a remote device wipe, and you losing any personal data that hasn't been backed up or synchronised. What can be remotely removed from the device are work email profiles and work related documents, for example.
Figure 1: Existing Android MAM policy settings in the Microsoft 365 admin center.
Now that MDM capabilities are included, it means that corporate owned iOS and Android devices can be managed at the device level. This means that a large range of MDM policies can be applied to the device to make it meet the corporate requirements. For organisations that supply users with work devices, this degree of control is often required, regardless of the size of the organisation. Right now you won't see anything in the drop down for creating Android or iOS MDM policies, instead you will have to use Intune in the Azure portal.
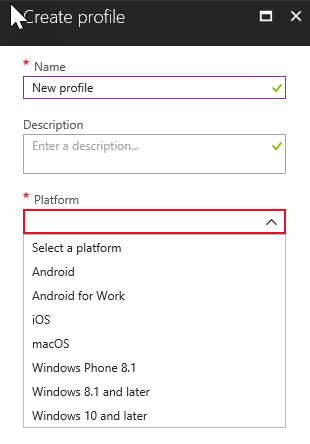 Figure 2: Intune's OS platform selection list in the Azure portal.
Figure 2: Intune's OS platform selection list in the Azure portal.
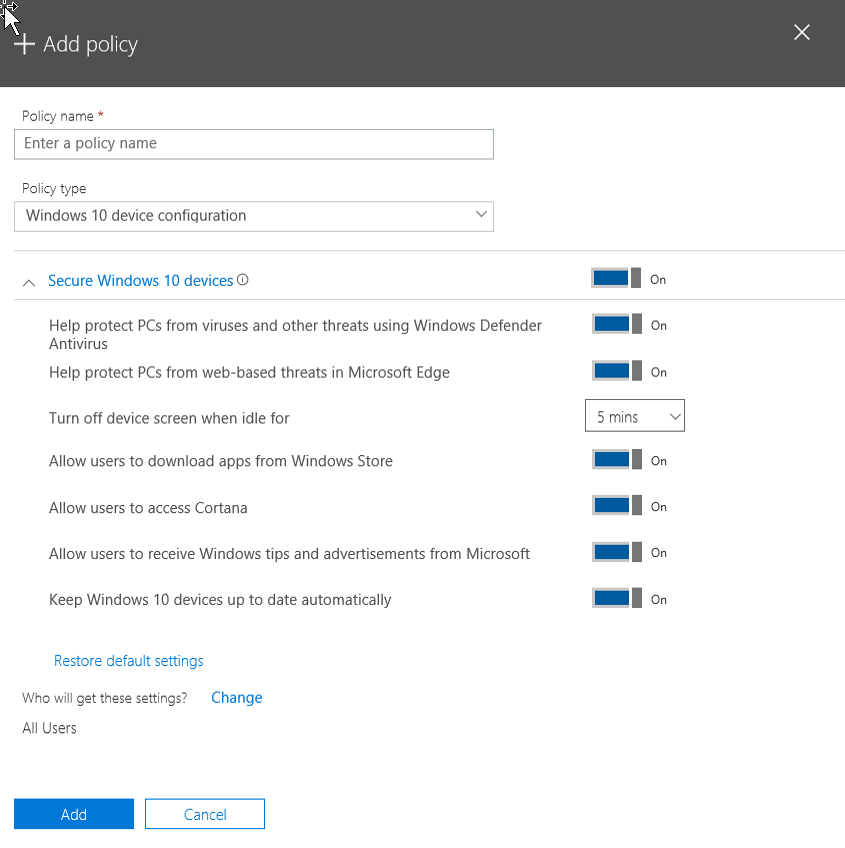
Moving on to Windows 10 management enhancements, you will see some additional options in the Windows 10 device configuration policy,
Figure 3: Original Windows 10 device configuration policy options
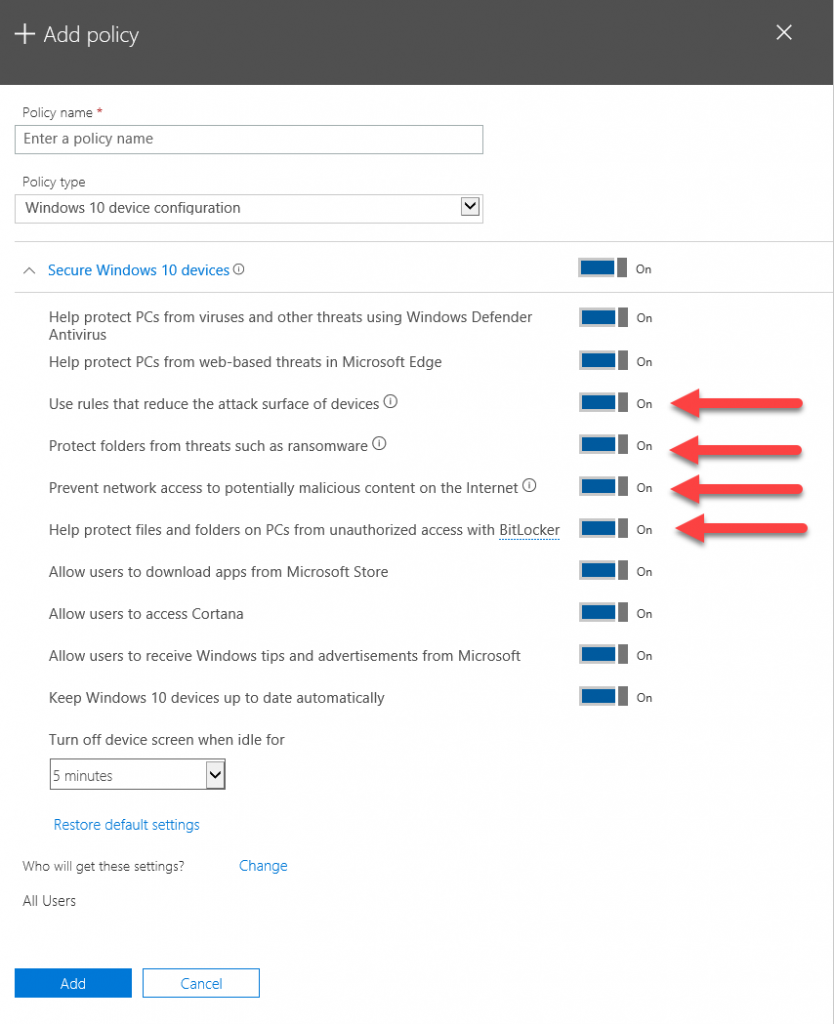
Below I've highlighted the new options, which are as follows.
Use rules that reduce the attack surface of devices
When turned On, attack surface reduction helps block actions and apps typically used by malware to infect devices. This setting is only available if Windows Defender Antivirus is set to On.Protect folders from threats such as ransomware
This setting uses controlled folder access to protect company data from modification by suspicious or malicious apps, such as ransomware. These types of apps are blocked from making changes in protected folders. This setting is only available if Windows Defender Antivirus is set to On.Prevent network access to potentially malicious content on the Internet
Use this setting to block outbound user connections to low-reputation Internet locations that may host phishing scams, exploits or other malicious content. This setting is only available if Windows Defender Antivirus is set to On.Help protect files and folders on PCs from unauthorized access with BitLocker
BitLocker is a data protection feature that encrypts the hard drives on computers to protect against data theft or exposure if a computer is lost or stolen
However, now that usage of Intune in the Azure portal is officially endorsed, this means that you can really start exploring additional settings that make sense in your Windows 10 deployments. In my own environment where I demonstrate AutoPilot, I have enhanced this by enabling Enterprise State Roaming in AAD to give a customised desktop experience, and using Intune policies to push down Start Menu layout settings, push printer and mapped drive settings to the client and installing additional apps from the Microsoft Store, including the Intune company portal. This is really just the starting point of what you can do, and how you approach it will depend on your organisational requirements.