Friday Mail Sack: Dang, This Year Went Fast Edition
Hi folks, Ned here again with your questions and comments. This week we talk:
- AD Garbage Collection behavior
- Applying Group Policy based on installed roles and features
- Apple hates .local domains
- More on auto site coverage from Lurch
- Fixing the mysteriously bad CPU performance of brand new servers
- DFSN and NetApp
- Hyper-V and AD/DFSR/FRS/etc. disk performance
- Other stuff, including useful Christmas assistance
On Dasher! On Comet! On Vixen! On --- wait, why does the Royal Navy name everything after magic reindeer? You weirdoes.
Question
I am planning to increase my forest Tombstone Lifetime and I want to make sure there are no lingering object issues created by this operation. I am using doGarbageCollection to trigger garbage collection immediately, but finding with an increased Garbage Collection logging level that this does not reset the 12-hour schedule, so collection runs again sooner than I hoped. Is this expected?
Answer
Yes. The rules for garbage collection are:
- Runs 15 minutes after the DC boots up (15 minutes after the NTDS service starts, in Win2008 or later)
- Runs every 12 hours (by default) after that first time in #1
- Runs on the interval set in attribute garbageCollPeriod if you want to override the default 12 hours (minimum supported is 1 hour, no less)
- Runs when forced with doGarbageCollection
Manually running collection does not alter the schedule or “reset the timer”; only the boot/service start changes that, and only garbageCollPeriod alters the next time it will run automagically.
Therefore, if you wanted to control when it runs on all DCs and get them roughly “in sync”, restarting all the DCs or their NTDS services would do it. Just don’t do that to all DCs at precisely the same time or no one will be able to logon, mmmmkaaay?
Question
I’ve read your post on filtering group policy using WMI. The piece about Core versus Full was quite useful. Is there a way to filter based on installed roles and features though?
Answer
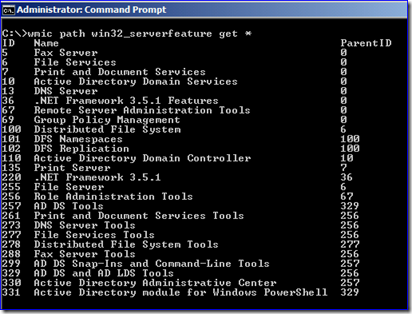
Yes, but only on Windows Server 2008 and later server SKUs, which supports a class named Win32_ServerFeature. This class returns an array of ID properties that populates only after installing roles and features. Since this is WMI, you can use the WMIC.EXE to see this before monkeying with the group policy:
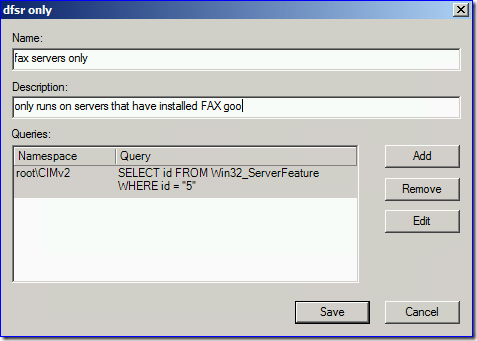
So if you wanted to use the WQL filtering of group policy to apply a policy only to Win2008 FAX servers, for example:
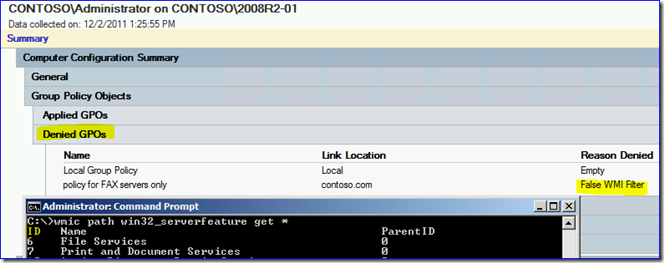
On a server missing the FAX Server role, the policy does not apply:
If you still care about FAXes though, you have bigger issues.
Question
We’re having issues with binding Macs (OS 10.6.8 and 10.7) to our AD domain that uses a '.LOCAL’ suffix. Apple is suggesting we create Ipv6 AAAA and PTR records for all our DCs. Is this the only solution and could it cause issues?
Answer
That’s not the first time Apple has had issues with .local domains and may not be your only problem (here, here, here, etc.). Moreover, it’s not only Apple’s issue: .local is a pseudo top-level domain suffix used by multicast DNS. As our friend Mark Parris points out, it can lead to other aches and pains. There is no good reason to use .local and the MS recommendation is to register your top level domains then create roots based off children of that: for example, Microsoft’s AD forest root domain is corp.microsoft.com, then uses geography to denote other domains, like redmond.corp.microsoft.com and emea.corp.microsoft.com; geography usually doesn’t change faster than networks. The real problem was timing: AD was in development several years before the .local RFC released. Then mDNS variations had little usage in the next decade, compared to standard DNS. AD itself doesn’t care what you do as long as you use valid DNS syntax. Heck, we even used it automatically when creating Small Business Server domains.
Enough rambling. There should be no problem adding unused, internal network Ipv6 addresses to DNS; Win2008 and later already have IPv6 ISATAP auto-assigned addresses that they are not using either. If that’s what fixes these Apple machines, that’s what you must do. You should also add matching IPv6 network “subnets” to all your AD sites as well, just to be safe.
Although if it were me, I’d push back on Apple to fix their real issue and work with this domain, as they have done previously. This is a client problem on their end that they need to handle – these domains predate them by more than a decade. All they have to do is examine the SOA record and it will be clear that this is an internal domain, then use normal DNS in that scenario.
Oh, or you could rename your forest.
BBWWWWAAAAAAAHAHAHAHAHHAHAHAHHAHAHAHHAHAHAHAHAAA.
Sorry, had to do it. ツ
Question
We were reviewing your previous site coverage blog post. If I use this registry sitecoverage item on DCs in the two different sites to cover a DC-less site, will I get some form of load balancing from clients in that site? I expect that all servers with this value set will create SRV records in DNS to cover the site, and that DNS will simply follow normal round-robin load balancing when responding to client requests. Is this correct?
Answer
[From Sean Ivey, who continues to rock even after he traitorously left us for PFE – Ned]
From a client perspective, all that matters is the response they get from DC/DNS from invoking DCLocator. So for clients in that site, I don’t care how it happens, but if DCs from other sites have DNS records registered for the DC-less site, then typical DNS round robin will happen (assuming you haven’t disabled that on the DNS server).
For me, the question is…”How do I get DCs from other sites to register DNS records for the DC-less site ?” review this:
https://technet.microsoft.com/en-us/library/cc937924.aspx
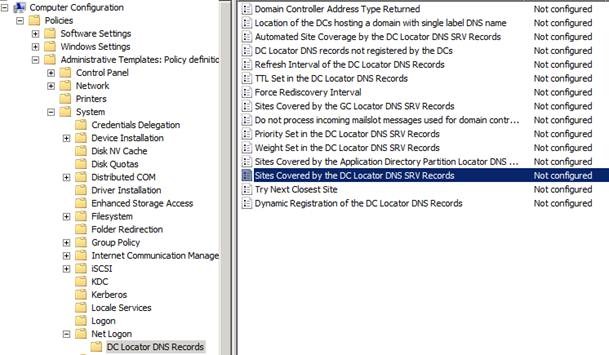
I’m partial to using group policy though. I think it’s a cleaner solution. You can find the GP setting that does the same thing here:
Simply enable the setting, enter the desired site, and make sure that it only applies to the DC’s you want it to apply to (you can do this with security filtering).
Anyway, so I set this up in my lab just to confirm everything works as expected.
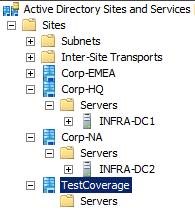
My sites:
Notice TestCoverage has no DC’s.
My site links:
Corp-HQ is my hub so auto site coverage should determine the DC’s in Corp-HQ are closest and should therefore cover site TestCoverage.
DNS:
Whaddya know, Infra-DC1 is covering site TestCoverage as expected.
Next I enable the GPO I pointed out and apply it only to Infra-DC2 and voila! Infra-DC2 (which is in the Corp-NA site) is now also covering the TestCoverage site:
You have a slightly more complicated scenario because auto site coverage has to go one step farther (using the alphabet to decide who wins) but in the end, the result is the same.
Question
We’re seeing very high CPU usage in DFSR and comparably poor performance. These are brand new servers - just unboxed from the factory - with excellent modern hardware. Are there any known issues that could cause this?
Answer
[Not mine, but instead paraphrased from an internal conversation with MS hardware experts; this resolved the issue – Ned]
Set the hardware C-State to maximize performance and not save power/lower noise. You must do this through the BIOS menu; it’s not a Microsoft software setting. We’ve also seen this issue with SQL and other I/O-intensive applications running on servers.
Question
Can NetApp devices host DFS Namespace folder targets?
Answer
This NetApp community article suggests that it works. Microsoft has no way to validate if this is true or not but sounds ok. In general, any OS that can present a Windows SMB/CIFS share should work, but it’s good to ask.
Question
How much disk performance reduction should we expect with DFSR, DFSN, FRS, Directory Services database, and other Active Directory “stuff” on Hyper-V servers, compared to physical machines?
Answer
We published a Virtual Hard Disk Performance whitepaper without much fanfare last year. While it does not go into specific details around any of those AD technologies, it provides tons of useful data for other enterprise systems like Exchange and SQL. Those apps are very “worst case” case as they tend to write much more than any of ours. It also thoroughly examines pure file IO performance, which makes for easy comparison with components like DFSR and FRS. It shows the metrics for physical disks, fixed VHD, dynamic VHD, and differencing VHD, plus it compares physical versus virtual loads (spoiler alert: physical is faster, but not as much as you might guess).
It’s an interesting read and not too long; I highly recommend it.
Other Stuff
Joseph Conway (in black) was nearly beaten in his last marathon by a Pekinese:
Weirdest Thanksgiving greeting I received last month? “Have a great Turkey experience.”
Autumn is over and Fail Blog is there (video SFW, site is often… not):
A couple excellent “lost” interviews from Star Wars. Mark Hamill before the UK release of the first film and the much of the cast just after Empire.
New York City has outdone its hipster’itude again, with some new signage designed to prevent you from horrible mangling. For example:
IO9 has their annual Christmas mega super future gift guide out and there are some especially awesome suggestions this year. Some of my favorites:
- NerdKits
- Physics of the Future
- The Guardian from Big Trouble Little China (that one’s for you, Mark)
- Chumbuddy Plushy
- Robot tea infuser
- I have the Power(point) t-shirt
Make also has a great DIY gift guide. Woo, mozzarella cheese kit!
Still can’t find the right gift for the girls in your life? I recommend Zombie Attack Barbie.
On a related topic, Microsoft has an internal distribution alias for these types of contingencies:
“A group whose goal is to formulate best practices in order to ensure the safety of Microsoft employees, physical assets, and IP in the event of a Zombie Apocalypse.”
Finally
This is the last mail sack before 2012, as I am a lazy swine going on extended vacation December 16th. Mark and Joji have some posts in the pipeline to keep you occupied. Next year is going to be HUGE for AskDS, as Windows 8 info should start flooding out and we have all sorts of awesome plans. Stay tuned.
Merry Christmas and happy New Year to you all.
- Ned “oink” Pyle
![clip_image002[5] clip_image002[5]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/58/02/metablogapi/2161.clip_image0025_thumb_6CEDFF26.jpg)
![clip_image002[7] clip_image002[7]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/58/02/metablogapi/6765.clip_image0027_thumb_24739A48.jpg)
![clip_image002[9] clip_image002[9]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/58/02/metablogapi/0511.clip_image0029_thumb_2A8AC116.jpg)

