Friday Mail Sack: Anchors Aweigh Edition
Hiya folks, Ned here again. I finally have an editor that allows anchors on all the questions, so I am adding a quasi “table of contents” for these posts that allow easier navigation and linking. I’ll retrofit all the old mail sack articles too… eventually. This week we discuss – eh - let’s have the bullets do the talking:
- How to audit which versions of NTLM are being used
- What to do now that you have Windows Server 2008 R2 Forest Functional Level in place
- USMT security-ntlm-lmc.man XmlException error
- FRS events missing in KB 308406 for Windows Server 2003 and later
- Why you can’t have “non-admin admins” on writable domain controllers
- Does DFSR’s built-in auditing impact performance?
- Netware volumes as DFS Namespace targets
- Support for the Group Policy Best Practices tool
- More Comic-Con cosplay
Question
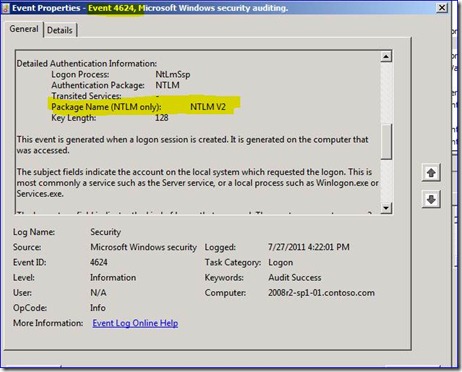
We are trying to move away from NTLM in our Active Directory environment. I read your previous post on NTLM Auditing for later blocking. However, the blog posting does not differentiate between the two versions of NTLM. What would be the best way to audit for only NTLMv1 or LM? Also, will Microsoft ever publish those two TechNet articles?
Answer
I still suggest you give up on this, unless you want to spend six months not succeeding. :) If you want to try though, add security event logging on your Win2008 R2 servers/DCs for 4624 Logon events:
977519 Description of security events in Windows 7 and in Windows Server 2008 R2
https://support.microsoft.com/default.aspx?scid=kb;EN-US;977519
Those will capture the Package Name type. For example:
Best I can tell, those two TechNet articles are never going to be published. Jonathan is trying yet again as I write this. Maybe Win8...? We'll see...
Question
I am now 100% Windows Server 2008 R2 in my domains and am ready to move my Domain and Forest Functional Levels to 2008 R2. What does that and my new schema buy me, and are there any steps I should do in special order?
Answer
Nothing has to happen in any special order. Some of your new AD-related options include:
- AD Recycle Bin ( https://blogs.technet.com/b/askds/archive/2009/07/24/active-directory-recycle-bin-in-windows-server-2008-r2.aspx )
- DFSR for SYSVOL ( https://technet.microsoft.com/en-us/library/dd640019%28WS.10%29.aspx )
- V2 DFS Namespaces (https://technet.microsoft.com/en-us/library/cc770287.aspx ) and migrate existing V1 namespaces ( https://technet.microsoft.com/en-us/library/cc753875.aspx )
- Last Interactive Logon (https://technet.microsoft.com/en-us/library/dd446680(WS.10).aspx )
- Fine Grain Password Policies – (https://technet.microsoft.com/en-us/library/2199dcf7-68fd-4315-87cc-ade35f8978ea )
- Virtual Desktops (https://technet.microsoft.com/en-us/library/dd941616(WS.10).aspx )
- Managed Service Accounts with automatic SPN management (https://technet.microsoft.com/en-us/library/dd548356(WS.10).aspx )
- Other things we recommend at the end of the upgrade ( https://technet.microsoft.com/en-us/library/cc753753(v=WS.10).aspx )
With your awesome Win2008 R2 servers, you can also:
- Use new PKI features (https://technet.microsoft.com/en-us/library/dd448537(v=WS.10).aspx )
- Use Starter GPOs and new GP Preferences and other GP stuff ( https://technet.microsoft.com/en-us/library/dd367853(v=WS.10).aspx )
- All this other craziness ( https://technet.microsoft.com/en-us/library/dd391932(v=WS.10).aspx )
Question
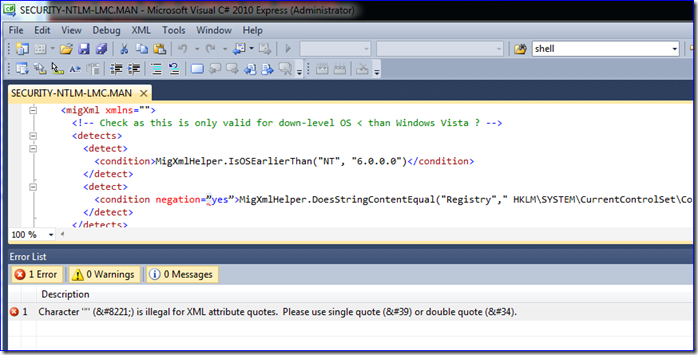
Our USMT scanstate log shows error:
Error [0x08081e] Failed to load manifest at C:\USMT\x86\dlmanifests\security-ntlm-lmc.man: XmlException: hResult = 0x0, Line = 18, Position = 31; A string literal was expected, but no opening quote character was found.
But nothing bad seems to happen and our migration has no issues we can detect. It looks like the quotation marks in the XML are incorrect. If I correct that, it runs without error, but am I making something worse and is this supported?
Answer
Right you are. Note the quotation marks – looks like some developer copied them out of a rich text editor at some point:
But no matter – you can change it or delete that MAN file, it makes no difference. That manifest file does not have a USMT scope set, so it is never used even when syntactically correct. In order for USMT to pick up a manifest file during scanstate and loadstate, it must have this set:
<migration scope="Upgrade,MigWiz,USMT">
If not present, the manifest is skipped with message “filtered out because it does not match the scope USMT”:
Roughly two thirds of the manifests included with USMT are not used at all for this very same reason.
Question
I am looking for a full list of Event IDs for FRS. KB 308406 only seems to include them for Windows 2000 – is that list accurate for later operating systems like WIndows Server 2003 or 2008 R2?
Answer
That KB article has a few issues, I’ll get that ironed out. In the meantime:
Windows Server 2003 added events:
Event ID: 13569
Severity: Error
The File Replication Service has skipped one or more files and/or directories during primary load of the following replica set. The skipped files will not replicate to other members of the replica set.
Replica set name is : "%1"
A list of all the files skipped can be found at the following location. If a directory is skipped then all files under the directory are also skipped.
Skipped file list : "%2"
Files are skipped during primary load if FRS is not able to open the file. Check if these files are open. These files will replicate the next time they are modified.
Event ID: 13570
Event Type: Error
The File Replication Service has detected that the volume hosting the path %1 is low on disk space. Files may not replicate until disk space is made available on this volume.
The available space on the volume can be found by typing
"dir /a %1".
For more information about managing space on a volume type "copy /?", "rename /?", "del /?", "rmdir /?", and "dir /?".
Event ID: 13571
Event Type: Error
The File Replication Service has detected that one or more volumes on this computer have the same Volume Serial Number. File Replication Service does not support this configuration. Files may not replicate until this conflict is resolved.
Volume Serial Number : %1
List of volumes that have this Volume Serial Number: %2
The output of "dir" command displays the Volume Serial Number before listing the contents of the folder.
Event ID: 13572
Event Type: Error
The File Replication Service was unable to create the directory "%1" to store debug log files.
If this directory does not exist then FRS will be unable to write debug logs. Missing debug logs make it difficult, if not impossible, to diagnose FRS problems.
Windows Server 2008 added no events.
Windows Server 2008 R2 added events:
Event ID: 13574
Event Type: Error
The File Replication Service has detected that this server is not a domain controller. Use of the File Replication Service for replication of non-SYSVOL content sets has been deprecated and therefore, the service has been stopped. The DFS Replication service is recommended for replication of folders, the SYSVOL share on domain controllers and DFS link targets.
Event ID: 13575
Event Type: Error
This domain controller has migrated to using the DFS Replication service to replicate the SYSVOL share. Use of the File Replication Service for replication of non-SYSVOL content sets has been deprecated and therefore, the service has been stopped. The DFS Replication service is recommended for replication of folders, the SYSVOL share on domain controllers and DFS link targets.
Event ID: 13576
Event Type: Error
Replication of the content set "%1" has been blocked because use of the File Replication Service for replication of non-SYSVOL content sets has been deprecated. The DFS Replication service is recommended for replication of folders, the SYSVOL share on domain controllers and DFS link targets.
All OSes included event:
Event ID: 13573
Event Type: Warning
File Replication Service has been repeatedly prevented from updating:
File Name : "%1"
File GUID : "%2"
due to consistent sharing violations encountered on the file. Sharing violations occur when another user or application holds a file open, blocking FRS from updating it. Blockage caused by sharing violations can result in out-of-date replicated content. FRS will continue to retry this update, but will be blocked until the sharing violations are eliminated. For more information on troubleshooting please refer to https://support.microsoft.com/?id=822300.
Win2008 should have had those 13574-13576 events as they are just as applicable, but $&% happens.
Question
Why isn’t it possible to grant local admin rights to a domain controller without added them to the built-in Administrators or Domain Admins groups? It can be done on RODCs, after all.
Answer
It’s with good intentions – if I am a local administrator on a DC, I own that whole domain. I can directly edit the AD database, or even replace it with my own copy. I can install a filter driver that intercepts all password communications between LSASS and the database. I can turn off all auditing and group policy. I can add a service that runs as SYSTEM and therefore, runs as the DC itself – then impersonate the DC. I can install a keyboard logger that captures the “real” domain admins as they logon. My power is almost limitless.
The reasons we added the functionality for non-domain admin administrators on RODC are:
- RODCs are not authoritative for anything and cannot originate any data out to any other DC or RODC. So the likelihood of damage or compromise is lower - although theoretically, not removed.
- RODCs are for branch offices that don’t have dedicated IT staff and which may not even be reliably network connected to the main IT location – so having a “local admin” makes sense for management.
Question
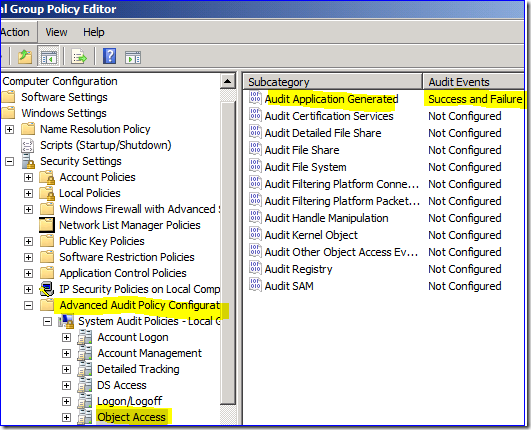
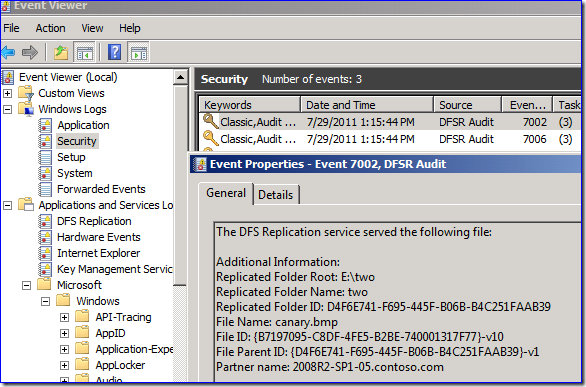
You have talked about how to track individual DFSR file replication using its built-in “enable audit” setting. Does this impact server performance?
Answer
Yes and no. The additional DFSR logging impact is negligibly low on any OS. The object access auditing impact ranges from medium (by default) to high (if you have added many custom SACLs). You have to enable the object access auditing to use the DFSR logging on Win2003 though, so the net result there is medium to high impact when compared to other auditing categories.
It’s worth noting that overall, auditing impact in Win2008+ is lower, as the audit system was redesigned for greater scalability and performance. You also have a much less disruptive security audit option, which is to enable only the subcategory:
That way you don’t have to enable the completely ridiculous set of Object Access auditing in order to track only DFSR file changes. And the impact is greatly lowered.
And besides, to run Win2008+, you need much faster hardware anyway. ^_^
Question
Can Netware volumes be DFSN Link Targets?
Answer
Good grief, someone still has Netware servers?
Yes, with caveats:
824729 Novell 6 CIFS pass-through authentication failures https://support.microsoft.com/default.aspx?scid=kb;EN-US;824729
Novell also created a DFS service, to act as a root instead of simply a link target like above:
Using DFS to Create Junctions https://www.novell.com/documentation/nw6p/?page=/documentation/nw6p/nss_enu/data/adqqknt.html
Generally speaking, if a target can provide SMB/CIFS shares, they can be a link target. To connect to a DFS target, your OS needs a DFS client:
Can Apple, Linux, and other non-MS operating systems connect to DFS Namespaces? https://blogs.technet.com/b/askds/archive/2011/01/18/can-apple-linux-and-other-non-ms-operating-systems-connect-to-dfs-namespaces.aspx
Bring on the Banyan Vines questions!
Question
There is no later version of the Group Policy Best Practices Analyzer tool and no updates when it starts. Is it going to be updated for Windows Server 2008 or later? The tool was even mentioned by Tim on this very blog years ago, but since then, nothing.
[This “question” came from a continued conversation about a specific aspect of the tool – Ned]
Answer
- This tool has no updates or development team and is effectively abandoned. It was not created by the Group Policy Windows developer group nor is it maintained by them – it doesn’t have a dev team at all. It probably should have released in CodePlex instead of the download center. The genie cannot be put back in the bottle now though, as people will just grab copies from elsewhere on the internet, likely packed with malware payloads.
- This tool is not supported – it’s provided as-is. When Tim talked about it, the tool had a bright future. Now it is gooey dirt.
- This tool’s results and criteria are questionable, bordering on dangerous. It gives a very false sense of security if you pass, because it checks very little. It also incorrectly flags issues that do not exist – for example, it states that the Enterprise Domain Controllers group does not have Apply GP permissions to the Default Domain Controllers policy, and this is an error. The DCs are all members of Authenticated Users though, and that’s how they get Apply permissions. And why doesn’t it raise the same flag for the default domain policy? Who knows! The developers were not correct in this design or assumptions. The tool recommends you add more RPC ports for invalid reasons, which is silly. It talks about a few security settings, ignoring hundreds of others and giving no warning that changing these can break your entire environment. Gah!
If you are looking for security-related best practice recommendations for group policy, you should be using the Security Compliance Manager tool:
Microsoft Security Compliance Manager v1 (release) https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=16776
Microsoft Security Compliance Manager v2 (beta) https://blogs.technet.com/b/secguide/archive/2011/06/27/scm-v2-beta-new-baselines-available-to-download.aspx
That tool at least has best effort support and a living dev team that is providing vetted recommendations.
More Comic-Con Cosplay
As you know, I spent last week at San Diego Comic-Con and even showed some pictures I snagged. Here is more amazing cosplay, courtesy of the rad Comicvine.com (click thumbnails to make with the bigness). And check out the eyes on Scorpion.


Comicvine.com – go there now, unless you hate awesomeness
Until next time.
Ned “I should go as a Keebler Elf next year” Pyle
![clip_image002[8] clip_image002[8]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/58/02/metablogapi/1854.clip_image0028_thumb_57DC5E21.jpg)