Control Extended Protection for Authentication using Security Policy
Mike here again. Microsoft has introduced additional security measures for authentication known as Extended Protection for Authentication, also known as channel binding token (CBT). Extended protection can cause a variety of interoperability issues including but not limited to:
- Windows clients that support channel binding fail to be authenticated by a non-Windows Kerberos server
- NTLM authentication failures from Proxy servers
- NTLM authentication failures from non-Windows NTLM servers
- NTLM authentication failures when there is a time difference between the client and DC or workgroup server
Note: Read more about Extended Protection for Authentication in Microsoft Knowledge base article 968389 and MSDN.
Administrators may want to control the state of Extended Protection to multiple client computers. This can be accomplished using security policy. Security policy is the most appropriate solution to distribute the registry setting that controls Extended Protection for Authentication because the setting is stored under the LSA key in HKEY_LOCAL_MACHINE. Also, distributing the setting using security policy increases the chance of the desired settings winning all conflicts because, by default, security settings always apply during Group Policy Processing. Once the policy is applied, any user or application that changes the registry location will be reverted back to the desired configuration during the next application of security policy.
Add the policy setting to Security Policy settings
The Extended Protection for Authentication policy setting must be added to Security Policy editor to include the policy setting in Group Policy. To accomplish this:
1. Copy the following text
==== Start copy after this line ====
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SeCEdit\Reg Values\MACHINE/System/CurrentControlSet/Control/Lsa/SuppressExtendedProtection]
"ValueType"=dword:00000004
"DisplayType"=dword:00000003
"DisplayName"="Network Security: Extended Protection for Authentication"
"DisplayChoices"=hex(7):30,00,7c,00,45,00,6e,00,61,00,62,00,6c,00,65,00,64,00,\
00,00,33,00,7c,00,44,00,69,00,73,00,61,00,62,00,6c,00,65,00,64,00,00,00,00,\
00==== Stop copy before this line ====
2. Open Notepad and paste the text from step one into Notepad.
3. Click File and then Click Save As.
4. In the File name box, type secpoladd.reg.
5. In the Save as type list, click All Files. Remember the path to which the file is saved.
6. Click Save and close Notepad.
7. Locate the saved file from the path in step 5. Double-click the secpoladd.reg file. Click Yes to the Registry Editor dialog box.
It is only required to modify the security editor on the computer used to manage Group Policy. This allows the Extended Protection for Authentication policy setting to be included in a Group Policy object. Extending this security setting to other computers is not required for client computers to receive the security setting.
Include the Extended Protection for Authentication policy setting in Group Policy
With the security editor extended, you can now include the security setting within a Group Policy object. To do this:
1. Using GPMC, edit the Group Policy object that is to contain the security setting.
2. Navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options.
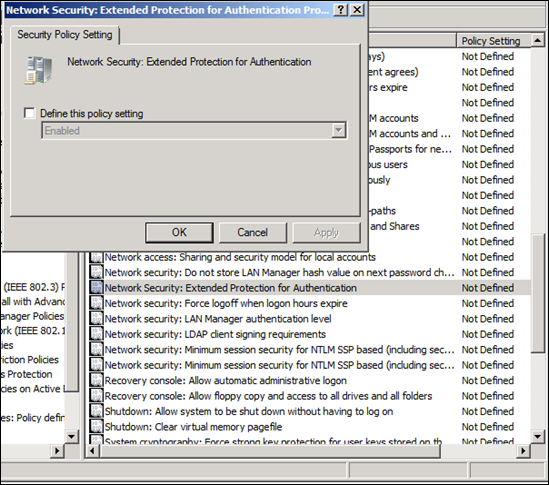
3. In the right pane of the MMC, scroll through the list of security settings to locate
Network Security: Extended Protection for Authentication. Double-click the security setting.4. Select Define this policy setting. Choose the desired configuration from the list and click OK.
5. Close the Group Policy object.
6. The Group Policy object now contains the security policy setting. Use GPMC to deploy the GPO to clients as needed.
Conclusion
Improving security always poses a risk with application compatibility. The long term solution is to determine why applications no longer work when security in heightened. A short-term solution during the investigation may be to reduce security to allow the application to work, pending the results of the investigation. Controlling this using Group Policy helps manage the setting for the enterprise.
Mike “I make tree-bicles” Stephens