Implementing an OCSP responder: Part IV - Configuring OCSP for use with Standalone CAs
Chris here again. In part I of this series we covered the basics of how OCSP works. We also covered the underlying reasons for deploying an OCSP Responder. In Part II we covered configuring the Certificate Authorities for whom which the OCSP Responder will check revocation status for on behalf of the clients. In Part III we covered configuring and OCSP Responder to support an Enterprise CAs. You may use Standalone CAs in your environment. In this blog post, I will be covering deploying a Revocation Configuration to support a Standalone CA.
Enterprise CAs are very tightly integrated with Active Directory. As such the certificates for the Root CA and for intermediate CAs are published to Active Directory. These certificates are automatically placed in the appropriate certificate stores on the clients. If you publish the Root CA certificate that the issuing CA chains up to; in Active Directory the clients will have that Root CA certificate published to the Trusted Root Certification Authorities container in the user and machine store. If you have not, or do not plan to deploy the Root CA certificate through Active Directory and Group Policy you will need to manually publish the Root Certificates in the Trusted Root Certification Authority store.
Installing OCSP Responder Role
The first step is to install the OCSP Responder Role.
To install the OCSP Responder: Open a command prompt and type: servermanagercmd.exe –install ADCS-Online-Cert
Requesting and Installing the OCSP Responder Signing Certificate
The next step is to request the OCSP Response Signing Certificate from the Standalone CA. Since a Standalone CA does not have certificate templates we must manually request the attributes we would like in the certificate. To do this we use a utility called certreq.exe. More information for Certreq is available here: https://technet.microsoft.com/en-us/library/cc736326.aspx.
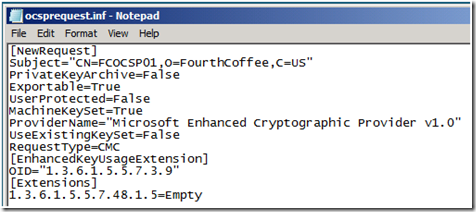
To use certreq we must first generate a configuration file. FIgure 1 shows a sample configuration file. The key items that must be included is the OCSP Signing OID, and the OCSP No Revocation Check Extension, otherwise known as the id-pkix-ocsp-nocheck extension.
Let us take a look at this configuration file.
· First we have [NewRequest] which is a required section indicating that this is for a new certificate request.
· Then we have the subject in X.500 format. You can also use the ldap format which is derived from X.500. For example: CN=FCOCSP01,DC=Fourthcoffe,DC=Com. Alternatively, you could use just the common name, such as CN=FCOCSP01.
· PrivateKeyArchive=False since we will not be archiving the private key.
· Exportable=True which gives us the option to export the private key if so desired.
· UserProtected=False which disables strong key protection.
· MachineKeySet =True which is used to indicte that the resulting certificate will be stored in the machine store.
· ProviderName=”Microsoft Enhanced Cryptographic Provider v1.0” specifies the Cryptographic Service Provider (CSP) that will be used.
· UseExistingKey Set=False indicates that this request is for a new certificate, with a new key pair.
· RequestType=CMC tells certreq to generate the request in CMC format.
· Then we specify the new section [EnhancedKeyUsageExtension] which indicates what extensions should be placed in the EKU Extension in the certificate. Under that extension we specify that this certificate can be used for OCSP Signing by specifying the OCSP Signing OID (OID=”1.3.6.1.5.5.7.3.9).
· We then start a new section called [Extensions] and specify that the id-pkix-ocsp-nocheck extension should be included in the certificate.
Below are the steps for generating the request and installing the signing certificate:
1. First we use certreq to generate the request file. We specify the configuration file and the output request file. The key pair for this certificate is generated at the same time the request file is created by Certreq.
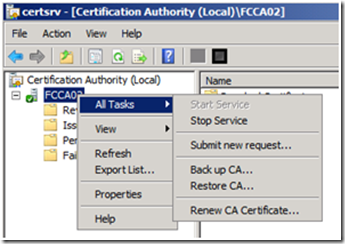
2. Next, we must submit the request to the CA. Copy the request file over to the Standalone CA. From the Certification Authority MMC, right click on the CA Name, and select All Tasks from the context menu, and then Submit New Request.
3. Browse to the request file, and select Open.
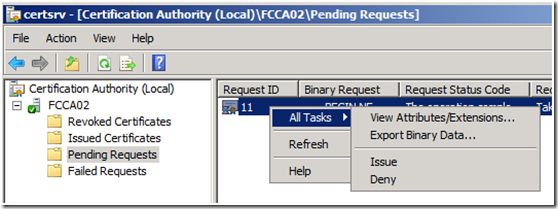
4. The request will then show up in Pending Requests. Right click on the request, and select All Tasks from the context menu, then select Issue.
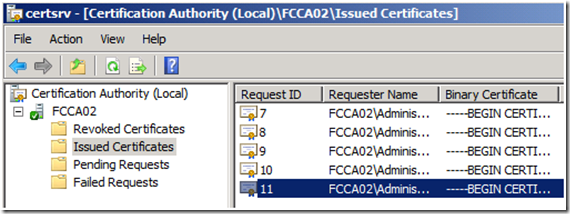
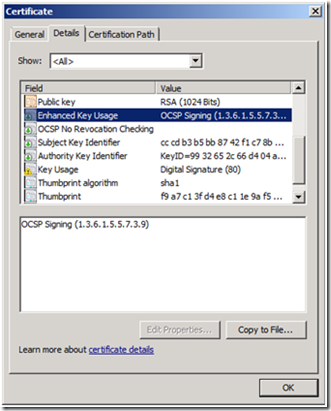
5. You will now find the requested Certificate under Issued Certificates. Double click on the certificate to view its properties.
6. Verify the certificate. Key things to look for here are the presence of the OCSP No Revocation Checking Extension. And that OCSP Signing is specified in the Enhanced Key Usage (EKU) Extension.
Exporting the Certificate from the CA
1. First select Copy to File from the Details Tab of the Certificate Properties. This will open the Certificate Export Wizard.
2. Click Next at the Welcome Screen.
3. Select DER encoded binary x.509 (.CER) , and click Next.
4. Browse to the location where you which to save the resulting certificate, and give the certificate a name, and click on Save.
5. Click Finish at the Completing the Certificate Export Wizard screen.
6. You will be prompted that The export was successful. Click OK.
Installing the OCSP Response Signing Certificate
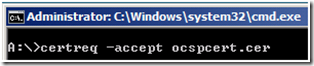
Copy the resulting certificate to the OCSP Server. Open up a command prompt. Navigate to the location where you saved the certificate file, and run certreq –accept <Certificate Name> , to complete the installation of the certificate.
Configuring Private Key Permissions
The Online Responder Service runs under the Network Service account. By default the Network Service account does not have access to private keys of certificates located in the Local Computer Personal store. To give the Network Service access, perform the following steps:
1. Open up the Certificates MMC targeted for the Local Computer.
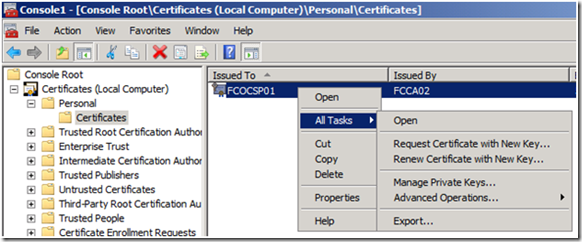
2. Right click on the certificate, then select “All Tasks” from the context menu, and then select Manage Private Keys… .
3. Click Add on the Permissions dialog box.
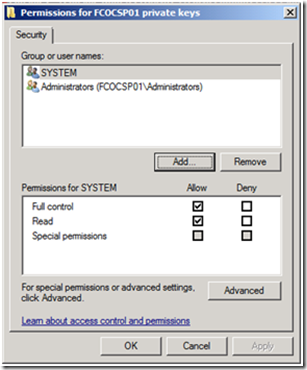
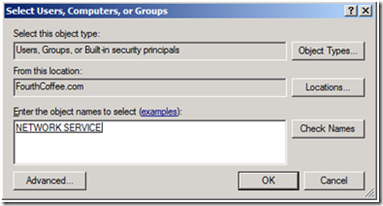
4. Type Network Service,and then click Check Names to resolve the name. Then click OK.
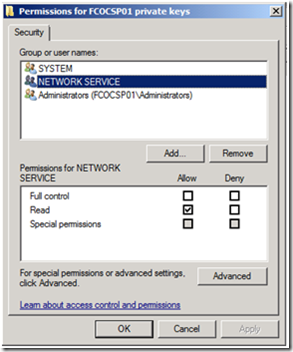
5. The Network Service only needs read permissions to the Private Key, so deselect the Allow privilege for Full Control, and verify the Allow privilege is granted for Read, and click OK.
Now that we have installed the OCSP Response Signing certificate, and configured Private Key permissions, we must now configure the Revocation Configuration for the CA, on the OCSP Responder. Open the OCSP Management Console. Follow the following steps to configure the Revocation Configuration:
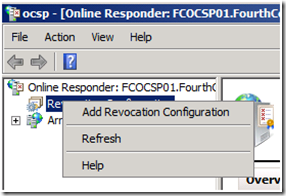
1. Right click on Revocation Configuration, and select Add Revocation Configuration from the context menu.
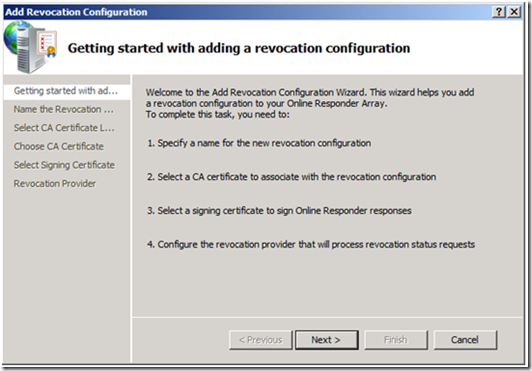
2. This will start the Add Revocation Configuration wizard. Click Next, when presented with the Getting started with adding a revocation configuration screen.
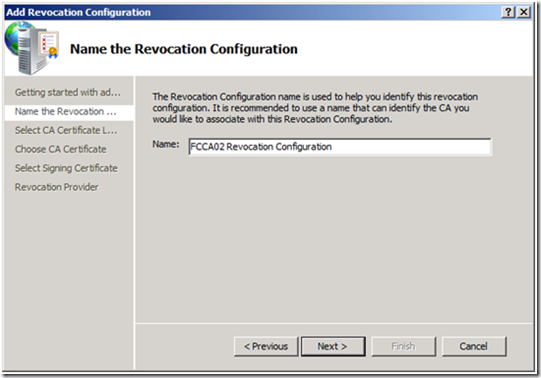
3. On the Name the Revocation Configuration screen, give a name to the configuration, and click Next. Note: It is a good idea to name the configuration for the CA server, in case this Responder will be used for multiple CAs.
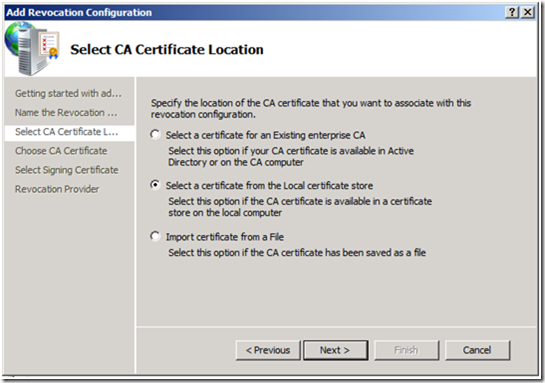
4. On the Select CA Certificate Location screen, Select a certificate from the Local certificate store, and click Next.
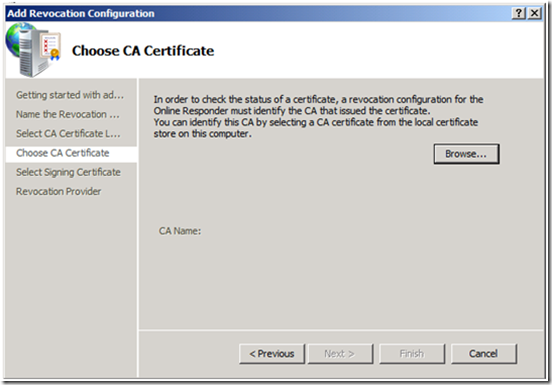
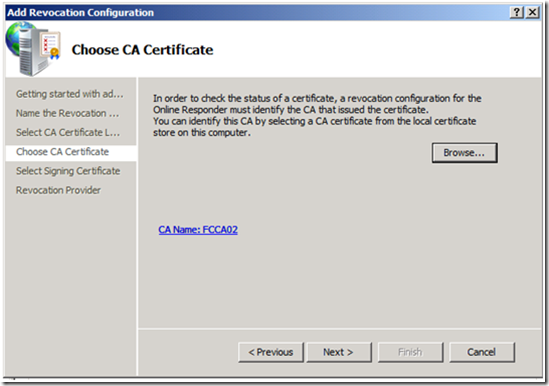
5. On the Choose CA Certificate screen, click Browse.
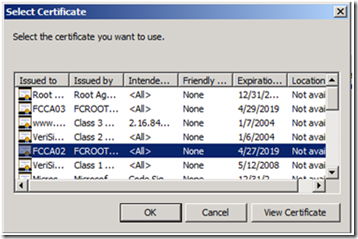
6. Select the CA certificate, for the CA you are configuring on the OCSP Responder, and click OK.
7. You will then be returned to the Choose CA Certificate screen. The CA that you selected will be displayed. Click Next to continue.
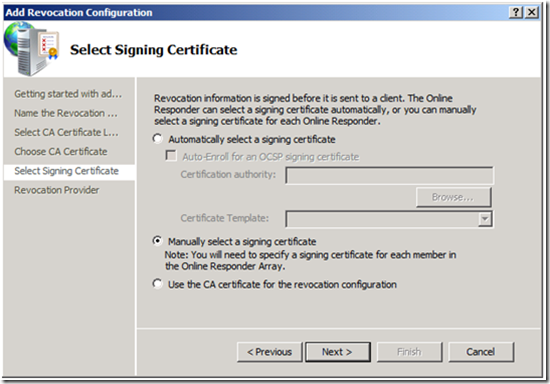
8. You will now need to select a signing certificate, on the Select Signing Certificate screen. Select Manually select a signing certificate, and click Next.
9. You will then be returned to the Revocation Provider screen, click Finish to complete the wizard.
Assigning the Signing Certificate
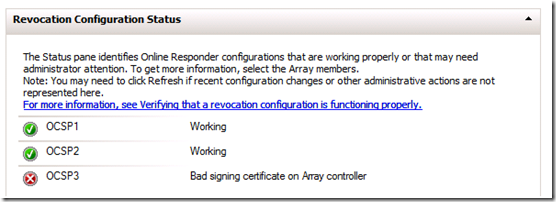
After completing the Wizard, you will notice under the “Revocation Configuration Status” portion of the “Online Responder Configuration” page that the OCSP Configuration that you just added has an error indicating “Bad Signing certificate on Array controller. No need to panic at this point. This error is generated because we have not assigned the OCSP Response Signing certificate yet.
Now let us go ahead and assign the Signing certificate.
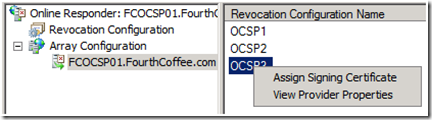
1. In the OCSP MMC, expand Array Configuration, and click on the name of the OCSP Server. Then in the center pane of the console, select the appropriate Revocation Configuration, then right click on that revocation configuration, and elect Assign Signing Certificate from the context menu.
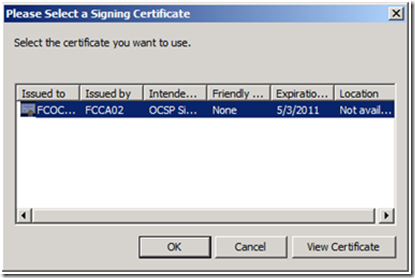
2. You will then be prompted select the Signing certificate. Select the appropriate Signing certificate, and click OK.
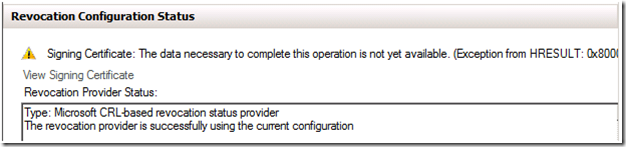
At this point you will now see some warnings. If you look under the Revocation Configuration Status for the Revocation Configuration you are configuring, you will notice this error:
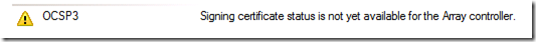
Also, on the Online Responder Configuration page you will notice this error:
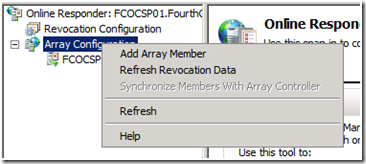
This is due to the fact that the Revocation Provider has not yet been verified. To verify the Revocation Provider, right click on Array Configuration, and select Refresh Revocation Data.
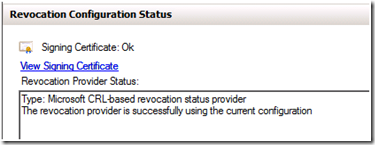
Once the Revocation Provider has been verified, you should see this under Revocation Configuration Status for the Revocation Configuration you are configuring.
And that OCSP Signing is specified in the Enhanced Key Usage (EKU) Extension.
Verify OCSP Configuration
To verify your ocsp configuration please follow the Verify OCSP Configuration section in Part III of this series.
Conclusion
This concludes Part IV of this Series. I hope you enjoyed the first four parts of the series and find them useful. I plan to cover other PKI topics in the near future.
Implementing an OCSP responder: Part I Introducing OCSP
Implementing an OCSP responder: Part II Preparing Certificate Authorities
Implementing an OCSP responder: Part III Configuring OCSP for use with Enterprise CAs
Implementing an OCSP responder: Part IV Configuring OCSP for use with Standalone CAs
Implementing an OCSP Responder: Part V High Availability
Implementing an OCSP Responder: Part VI Configuring Custom OCSP URIs via Group Policy
- Chris Delay