Replacing an Expired DRA Certificate
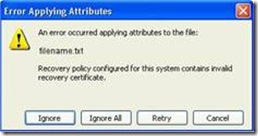
Hi, Tom here from the Directory Services team. One of the most common EFS issues we see is for an expired Domain Data Recovery Agent (DRA) certificate. It is also one of the easiest things to resolve. You may have seen the error Recovery Policy for this system contains an invalid recovery certificate or ERROR_BAD_RECOVERY_POLICY.
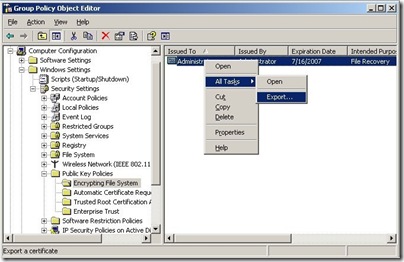
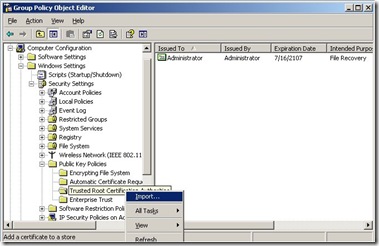
Since you can’t extend the life of a Recovery Agent certificate you will need to remove the expired ones first. You start by opening up the Default Domain Policy and navigating to Encrypting File System. On the right side you will see the expired certificate. Right click on the expired certificate and select All Tasks | Export, and export the file to a .CER format. Although this certificate has expired it can still be used to decrypt files that have already been encrypted with this Recovery Certificate specified. (The original DRA private key resides in the Administrator profile of the first domain controller in the domain. If this profile or domain controller no longer exists you may not be able to use this certificate to decrypt files.) Once this is completed you should delete this certificate from the Policy.
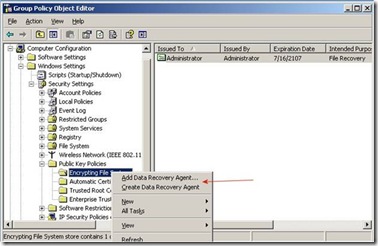
There are a couple of ways to get a new DRA certificate. If you are running an Enterprise Certificate Authority in your Domain you can choose Create Data Recovery Agent and a new certificate should be automatically installed. If you don’t have an Enterprise Certificate Authority or if you want the certificate to be good for a much longer period of time you can use the cipher command and create a self-signed certificate that will be good for 99 years.
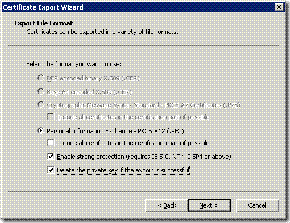
If you choose to create a Data Recovery Agent using your Enterprise Certificate Authority, please make sure to Export the newly created certificate and Export the Private key to maintain security. To do this, right-click on the new certificate, choose All Tasks and then Export. A wizard will guide you through the export process. Choose Yes, export the private key and then click next. As a best practice, the private key should be deleted from the system when a successful export is complete. Strong private key protection should also be used as an extra level of security on the private key while it exists on a file system (CD, Floppy, hard drive).
Once the *.PFX file and private key have been exported, the file should be secured on a stable media in a secure location. For example, you may want to preserve the *.PFX file on one or more CD-ROMs that are stored in a safety deposit box, vault, etc. that has strict physical access controls. If the file and associated private key are lost, it will be impossible to decrypt any existing files that have used that specific DRA certificate as the data recovery agent.
Creating a Self-Signed DRA Certificate
You may decide that even with an Enterprise Certificate Authority you want to use a Self-Signed DRA Certificate. The benefit of doing this is that you will not have to go through this process again. The downside is that there will be no Key Archival of the Private Key.
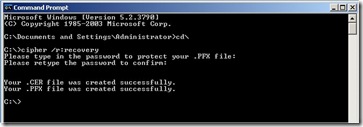
To create a new self-signed DRA certificate you need to open a command prompt on a XP/2003/Vista computer and then type cipher /r:filename where filename equals the name of the file you want to create. In my example below I used the name recovery. Use any password you want when prompted.
With the newly created DRA certificate, you go back to the Default Domain policy we were looking at above and select Add Data Recovery Agent and then choose Browse Folders select the certificate you just created. If you get a pop up box saying Windows cannot determine if this certificate has been revoked and a question about Do you want to install this certificate just click Yes.
Now you need to make sure that all of your clients will trust this newly created certificate so you need to import it into the Trusted Root Certification Authorities. Just right click and select Import and with a few more clicks you will almost done.
Getting Your Clients to Use the New Certificate
After you finish the above steps you need to refresh the Group Policy on the clients. You can do this by typing gpupdate /force at a command prompt. Once the policy has refreshed you should update the DRA information for the encrypted files by typing cipher /u at a command prompt. This will update only the files on the local machine so if you need to do this on a large number of machines you may want to put it in a login script. If you have any problems here you may need to reboot and try it again.
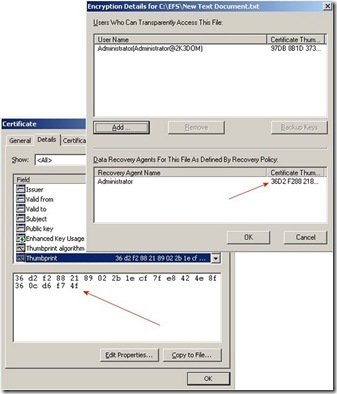
Now that you have done all of this how can you be sure that your encrypted files have been updated with the new DRA? Just check the Advanced Attributes for an encrypted file and compare the thumbprint of the DRA to the thumbprint of the certificate you just created.
You can also use the command EFSINFO /R /C in the directory where you have encrypted files and it will show you the DRA information. EFSInfo is a resource kit utility and can be downloaded at the following location:
Remember to copy the .PFX file you created earlier and put it away somewhere for safe keeping. This is the file you will need to import onto a user’s computer to decrypt a file should the need ever arise. If you created a new DRA certificate using your Certificate Authority you should export that certificate along with the private key and put it away as well.
Next time I’ll talk about some of the reasons you can get an Access Denied while trying to decrypt files.
Other Reading:
929103 Error message when you try to renew the default recovery agent certificate in Windows Server 2003, in Windows XP, or in Windows 2000: "This certificate cannot be renewed because it does not contain enough information to generate a renewal request"
https://support.microsoft.com/default.aspx?scid=kb;EN-US;929103
241201 How to back up the recovery agent Encrypting File System (EFS) private key in Windows Server 2003, in Windows 2000, and in Windows XP
https://support.microsoft.com/default.aspx?scid=kb;EN-US;241201
- Tom Ausburne