Documenting Active Directory Infrastructure the Easy Way
Hi, Ned here. From time to time customers ask us what their options are to document their Active Directory environments – site topologies, domains and trusts, where group policies are linked and what their settings are. Until recently we didn’t have an easy way to do this and they were forced to invest a lot of manual labor in creating a map. Today we’ll talk about some free tools we can use to make this task very easy and accurate. I’m going to focus on the most common areas:
• Domain and Forest information
• OU Structures
• Sites
• Exchange
• Group Policy settings and links
To do this we’re going to use two automation utilities that you will need to download and install:
• Active Directory Topology Diagrammer
• Group Policy Management Console
For the ADTD you will also need Microsoft Office Visio 2003 or 2007 and .NET 2.0 Framework. If you’re using the GPMC that comes with Windows Vista you will need to download the GPMC scripts separately. For this example we’ll assume you’re on XP.
GPMC is a centralized management and reporting tool for administering group policy. It includes some very useful (and well-hidden) scripts. ADTD is a newly released tool that can interrogate domain controllers about configuration data and create Visio diagrams that document your environment. When combined using the techniques below, that extremely boring and time-consuming documentation project you had in front of you is only going to take hours instead of weeks, leaving you free for more important things.
So let’s get started:
1. Install Visio, ADTD, and GPMC on a Windows XP Professional workstation or Windows Server 2003 server.
2. Start ADTD (it’s called ‘Microsoft Active Directory Topology Diagrammer’ on the Start Menu)
3. Now we’ll walk through the settings tabs to configure our data collection:
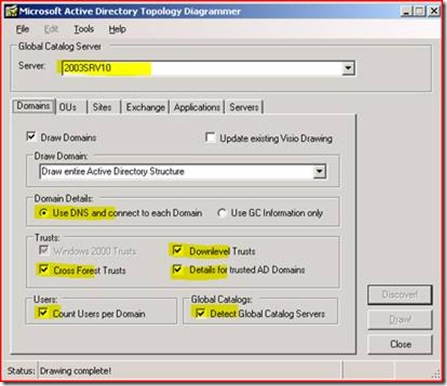
Enter in a local (to you) Global Catalog Domain Controller that you can interrogate with the tool. The actual LDAP queries to the GC only take a few seconds in most cases and should not generate any appreciable load – most of the heavy lifting in ADTD is local to your client in Visio. Add your trust settings (if you have more than one domain or multiple forests with trusts). You can also count your users per domains and identify all your GC’s. Using the default of ‘Use DNS and connect to each domain’ means that the tool will also connect to one DC in any trusting domains as well, but again, the amount of data returned will tend to be fairly small.
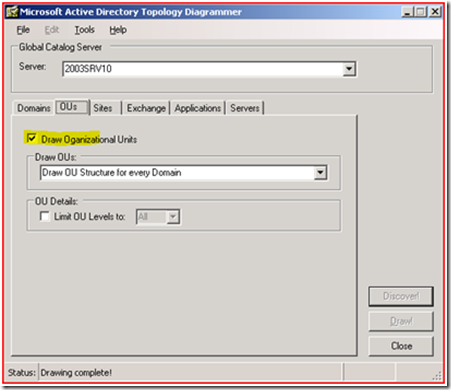
On the OU’s tab you can select to draw out all your Organizational Units. Most of the time you’ll want to avoid limiting the depth since your diagram will be incomplete.
On the Sites tab you can specify that Site Links, Replication Connections, and subnets are drawn. Avoid using the ‘suppress empty sites’ setting as it’s useful to see locations using Automatic Site Coverage.
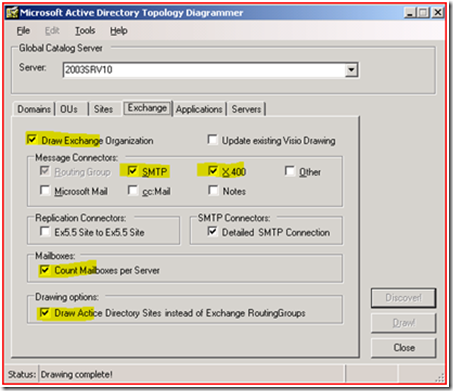
If you’re using Microsoft Exchange the Exchange tab can help diagram your Exchange Organization, where the connections are, the number of mailboxes per server, and even tie them to their logical AD sites so that you know which DC/GC combinations are servicing your messaging infrastructure.
If you're using Windows Server 2003 domain or forest-based AD-integrated DNS, you can also opt to show which DC’s are hosting those partitions.
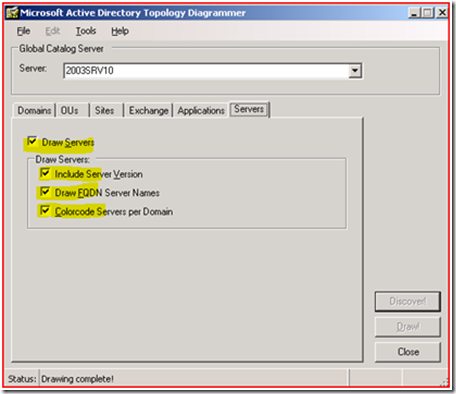
Finally, with ADTD you can get additional server information such as fully qualified domain names, operating systems and service pack, then color-code them for easier reading. This is especially useful in extremely large, complex environments where DC’s from many different domains are collocated in the same AD site within the same forest.
4. To execute your query, click Discover. After a few moments it will complete the LDAP lookups and will gray out. Click Draw, and go get a cup of coffee (or lunch, if you’re running hundreds of DC’s) – Visio will crank away creating all of the diagrams for some time. When it’s done, control will return to the ADTD application and you can close it.
So now we have some Visio diagrams that will be in your My Documents folder (by default; you can change this in ADTD's options menu). In the example below we have:
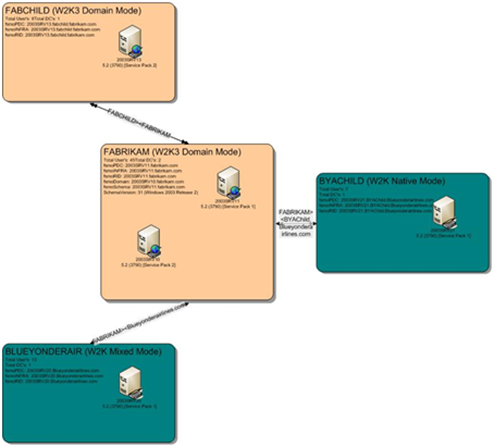
- A domain called fabrikam.com with two DC’s and an Exchange server.
- A child domain called fabchild.fabrikam.com with a single DC.
- An externally-trusted domain called blueyonderairlines.com
- An externally-trusted child domain called byachild.blueyonderairlines.com
So let’s look at what Visio gave us:
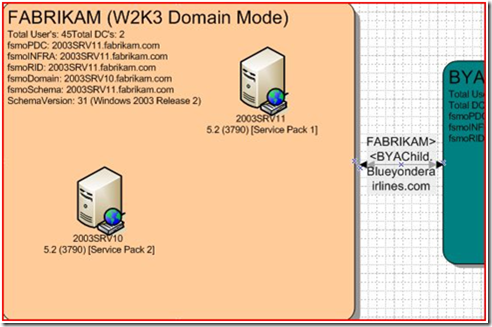
Above is the AD Domains.vsd. It shows our four domains and their trusts. Let’s zoom in on the FABRIKAM domain:
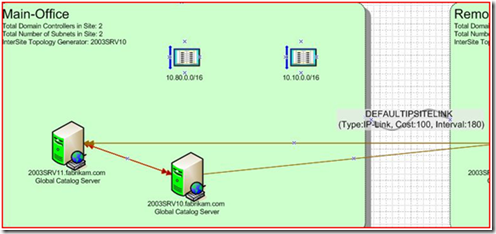
We have 45 total users on our two DC’s. All the FSMO role holders are identified, as well as the schema version and what domain functional mode we’re in. If we move on to the AD Sites.vsd:
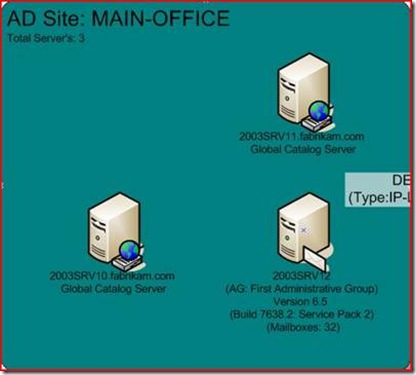
We can see that my Fabrikam.com forest has two sites, has several subnets bound to them, and there are connections between the DC’s. Let’s zoom in on that Main-Office site:
Nifty – we can see the GC’s, the subnet details, the intra and inter-site connections, the Site Link costs and schedule, and even the DC running the ISTG. If you want more detail on all these components check out the highly detailed How Active Directory Replication Topology Works.
Moving on to the AD Application Partitions.vsd, we can see that only two root domain DC’s are using 2003-style integrated DNS:
Since we have an Exchange 2003 server in this environment, Ex Organization.vsd shows us that it has affinity with the Main-Office site.
By zooming in we can see that server 2003SRV12 is part of the ‘First Administrative Group’ and is running Exchange 2003 Service Pack 2. It has 32 mailboxes. Any DC/GC lookups it’s doing should be happening against the two DC’s in this site.
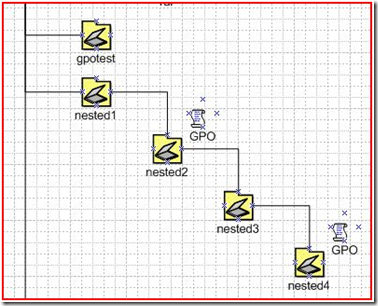
Finally for ADTD, we come to the OU diagram. The diagrammer can list out all the OU’s (below is a snippet), but other than telling us that that a Group Policy Object is linked to a given location, it doesn’t give much about the policies themselves.
So here’s where GPMC scripting kicks in:
1. We open a CMD prompt on our data gathering machine and (assuming we installed to default path) navigate to:
C:\Program Files\GPMC\Scripts
2. We type:
MD c:\GPMCReports
3. We execute (using our example domain):
Cscript ListSOMPolicyTree.wsf /domain:fabrikam.com > c:\gpmcreports\fabrikamgpotree.txt
4. This returns us the c:\gpmcreports\fabrikamgpotree.txt. If we open it we see:
=== GPO Links for domain fabrikam.com ===
DC=fabrikam
GPO=Default Domain Policy
GPO=AllCheck
OU=Domain Controllers
GPO=Default Domain Controllers Policy
OU=csc
OU=UserRepros
OU=foo
OU=rar
OU=RenamedPuters
OU=gpotest
OU=FolderRedir
OU=RedirectedTest
OU=nested1
OU=nested2
GPO=Logoff Screensaver
OU=nested3
OU=nested4
GPO=Password Screensaver
OU=wmi
OU=Admins
OU=Exchange
GPO=No Boot
=== GPO Links for sites in forest DC=fabrikam,DC=com ===
CN=Main-Office
CN=Remote-Office
5. We execute in our command prompt:
Cscript GetReportsForAllGPOs.wsf c:\gpmcreports /domain:fabrikam.com
6. This returns all of our policy settings for Fabrikam.com to the c:\gpmcreports folder:
== Found 6 GPOs in fabrikam.com
Generating XML report for GPO 'No Boot'
Generating HTML report for GPO 'No Boot'
Generating XML report for GPO 'Default Domain Policy'
Generating HTML report for GPO 'Default Domain Policy'
Generating XML report for GPO 'Logoff Screensaver'
Generating HTML report for GPO 'Logoff Screensaver'
Generating XML report for GPO 'Password Screensaver'
Generating HTML report for GPO 'Password Screensaver'
Generating XML report for GPO 'Default Domain Controllers Policy'
Generating HTML report for GPO 'Default Domain Controllers Policy'
Generating XML report for GPO 'AllCheck'
Generating HTML report for GPO 'AllCheck'
Report generation succeeded for 12 reports.
Report generation failed for 0 reports.
7. If we open one of these HTML reports, we can see everything there is to know about that policy. For example, we’ll open the ‘Password Screensaver’ GPO which is linked at OU ‘nested4’ ; there’s great stuff here…
Like settings detail above.
Or version history and status.
Or delegation.
Since all this is HTML and XML, you could simply link these live into your OU VSD’s, or get fancier and automate the importation of XML data (using Visio skills far better than mine!). Worst case you’re doing a little copying and pasting from the fabrikamgpotree.txt to update your GPO information instead of hand-crafting thousands objects and settings.
Now all you need is that $20,000 color plotter so you can print out your diagram wall-sized…
Further useful group policy information:
Group Policy Management Console Scripting Samples
Thanks for your time. If you come up with some slick Visio tricks please comment here and share them with the world!
- Ned Pyle
![clip_image002[6]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image002%5B6%5D_thumb.jpg)
![clip_image002[8]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image002%5B8%5D_thumb.jpg)
![clip_image002[10]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image002%5B10%5D_thumb.jpg)
![clip_image002[12]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image002%5B12%5D_thumb.jpg)

![clip_image002[14]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image002%5B14%5D_thumb.jpg)
![clip_image004[6]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image004%5B6%5D_thumb.jpg)
![clip_image006[5]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/askds/WindowsLiveWriter/DocumentingYourActiveDirectoryInfrastruc_9ECD/clip_image006%5B5%5D_thumb.jpg)