How to make your existing Bitlocker encrypted environment FIPS complaint
Hello, my name is Mayank Sharma and I am a Technical Advisor here at Microsoft. In this blog, I will discuss FIPS compliance with Bitlocker. Microsoft's solution for completely encrypting data inside laptops, desktops and removable drives. So let’s get started...
FIPS stands for Federal Information Processing Standard and is United States Government standards that provide a benchmark for implementing cryptographic software. It basically means that if a software is approved by one of the labs that do the testing for FIPS compliance, the software meets the government standard for cryptography. Thus can be commonly used by US Federal government and organizations around the world. There is a lot that can be written about FIPS. Better I route you to the following link:
FIPS Compliance
https://technet.microsoft.com/en-us/library/cc180745.aspx
To enable FIPS on a computer, i.e. tell it you have to be complaint with the government policies, we need to alter the following group policy
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
The name of the policy is following:
System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing
Now that we know what FIPS is and what it does, let’s focus our attention back on Bitlocker, Microsoft’s security solution for protecting data across laptops and desktops. Bitlocker uses multifactor authentication to ensure Bitlocker encrypted drive(s) will always remain in good hands. To accomplish this task, it uses multiple protectors to protect a volume. While some are ‘primary’ protectors which will be used most of the times, namely TPM, TPM and PIN, Password etc., some will be used when Bitlocker senses something has changed and goes in a lockdown mode. During a lockdown mode, it will ask user to prove that user is genuine. Examples of protectors include recovery password, recovery key, Data recovery agent, etc.
Now here comes the tricky part. Whether or not Bitlocker is FIPS complaint is decided by if one of the cryptographic keys that protector is using is indeed FIPS compliant. Password protectors for the operating system drive/fixed data drive are not complaint with FIPS specification, so does the recovery password until Windows 8. The below article discusses this in more detail:
The recovery password for Windows BitLocker is not available when FIPS
compliant policy is set in Windows Vista, Windows Server 2008, Windows 7
and Windows Server 2008 R2
https://support.microsoft.com/kb/947249
Let’s say there is a ‘happy go lucky’ organization that uses TPM+PIN protectors to authenticate the OS drive of user’s laptop running Windows 7 and storing recovery passwords in MBAM database. If a user gets locked out, Helpdesk will provide the information of recovery password to the user to unlock the machine. This is the happy ending of the story until one day FIPS were to be mandatorily implemented.
a. Will this happy go lucky Organization be FIPS complaint? No, as it is using recovery password as a protector which is not FIPS complaint.
b. Does this means while infrastructure needs to be rebuilt from scratch? Of course not!
Steps to make this environment FIPS complaint;
Step 1:
We need to get rid of the recovery password which is making the infrastructure non FIPS complaint. First thing would be to delete the associated recovery password with this Windows 7 machine. Run the following from an elevated command prompt:
manage-bde -protectors -get c:
This lists all the protectors
Volume C: [OSDisk]
All Key ProtectorsTPM And PIN:
ID: {161941A3-8CB3-439C-8FC6-1642D0C97C8D}
PCR Validation Profile:
0, 2, 4, 11Numerical Password:
ID: {C6DF1E74-467F-4BE8-9C59-C9A9F345B9A0}
Password:
017666-710820-610731-029986-330385-020009-303017-612733
Note the ID of the Numerical password protector and to delete it run the following command:
manage-bde -protectors -delete c: -id {C6DF1E74-467F-4BE8-9C59-C9A9F345B9A0}
This will delete the recovery password protector.
Step 2:
Now, imagine if the user forgot the PIN or because of any other reasons gets locked out. We should need to have a way to break back into machine. So we need to add some protectors that will help us in lockdown situations. Fortunately, we still have a choice to make here. We can add any of the two protectors which are FIPS compliant.
a. Data recovery agent
How to use Bitlocker Data Recovery Agent to unlock Bitlocker Protected Drives
https://blogs.technet.com/b/askcore/archive/2010/10/11/how-to-use-bitlocker-data-recovery-agent-to-unlock-bitlocker-protected-drives.aspx
b. Add a recovery key to the volume, this is as simple as running the command where e: is the destination drive where you want to store the .BEK file.
manage-bde -protectors -add c: -rk e:
Just save this file in a safe place. If a machine gets locks out, copy it over to a USB drive. More information can be found here:
What is a BitLocker recovery key?
https://Windows.microsoft.com/en-in/Windows7/what-is-a-bitlocker-recovery-key
Step 3:
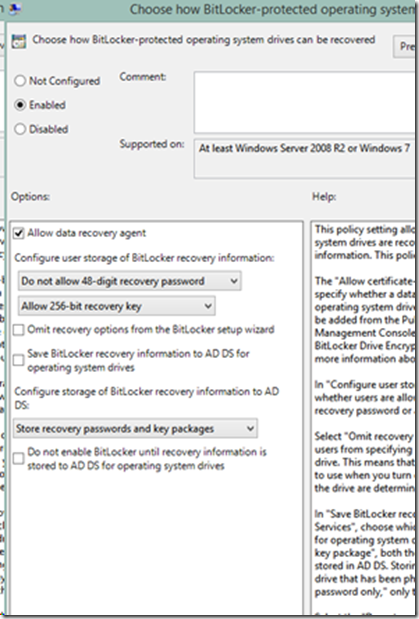
Though not mandatory, once we will enable the group policy for FIPS, it will not allow creation of FIPS. We can additionally disable the creation of any more recovery passwords. Just disable the policy like I did below under Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption.
As "Password" is not a FIPS complaint protectors, you cannot use it with fixed data drive either. We can either use a smart card protector or a DRA… And happy go lucky should be happy again!
As stated above, this is specifically meant for Windows 7/Vista and Windows Server 2008/2008R2. Had the company been proactive in moving along to a newer version of Windows (i.e. Windows 8/8.1, Windows Server 2012/2012R2), it would not have any effect on them. The recovery password is FIPS compliant for Windows 8 and above operating systems.
So this is pretty much it. Keep your machines encrypted until next time.
I thank Himanshu Singh for taking time out to go through this blog.
Mayank Sharma
Technical Advisor
Windows Deployment Services