Alternate Data Streams in NTFS
This blog has been a long time coming. There is a bit of confusion about the subject of alternate data streams (ADS) and no small amount of suspicion. So I want to take a few minutes to set the record straight on ADS.
A couple years ago I wrote a blog on NTFS attributes.
https://blogs.technet.com/b/askcore/archive/2010/08/25/ntfs-file-attributes.aspx
You might want to review that blog before continuing. I’ll wait….
Welcome back.
One of the common questions I get is, “Robert. What is an alternate data stream?”
My reply is always the same, “It is a data stream that is alternate”.
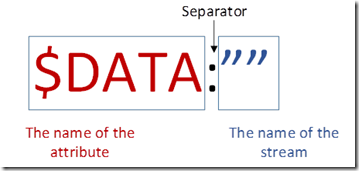
I don’t mean to be smart aleck about it…but that’s what it is. We know from my older blog that a file is divided up into ‘attributes’ and one of these attributes is $DATA or simply called the data attribute. It is the part of the file we put data into. So if I have a text file that says, “This is my text”, then if I look at the data attribute, it will contain a stream of data that reads, “This is my text”. However, this is the normal data stream, sometimes called the primary data stream, but more accurately it is called the unnamed data stream. Why? Because it is a data stream that has no name. In the jolly land of programming it is referred to as $DATA:””
The name of the stream will appear between the quotes. Since this is an unnamed data stream, there isn’t anything there.
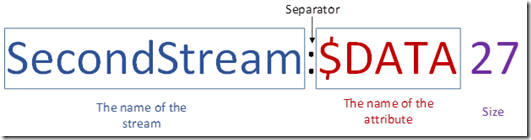
Now that we know what the unnamed data stream looks like, we can start thinking in terms of alternates. Knowing that the place we normally store data is the unnamed data stream, if a stream has a name, it is alternate. So if I had a file with an ADS named SecondStream, its full name would be, $DATA:”SecondStream”
This is all good and fine, but unlike the unnamed data stream, we can’t see the ADS. Or can we? The answer is, yes we can. But you have to use a method different than just opening the file in NotePad.
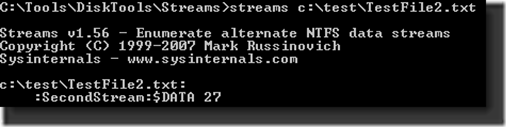
There are a number of tools out there that will allow you to view and manipulate ADS. One that Microsoft has provided for years is called STREAMS.EXE.
https://technet.microsoft.com/en-us/sysinternals/bb897440.aspx
STREAMS.EXE will display any ADS the file has.
The formatting is a little different.
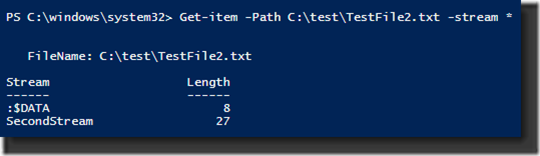
STREAMS.EXE is fine, and I’ve used it for years, but with the release of Win8/Server 2012, I’ve discovered a new way of dealing with ADS….Windows PowerShell. Using the cmdlet, Get-Item, I can get more information than I did with STREAM.EXE.
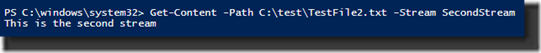
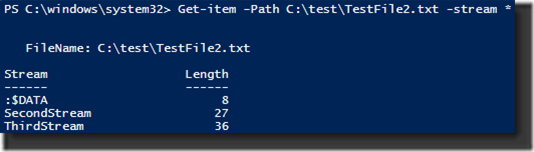
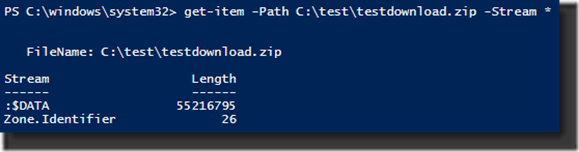
The output shows not only the name of the ADS and its size, but also the unnamed data stream and its size is also listed (shown as :$DATA). And now that I know the name of the ADS, I can use the Get-Content cmdlet to query its contents.
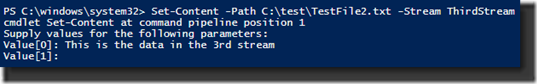
STREAM.EXE can’t display what’s actually in an ADS. Here’s another trick that STREAM.EXE can’t do….create data streams. Using Set-Content, I’ll create a second ADS in the same file and add a line of text.
And again, we can query for the streams using Get-Item.
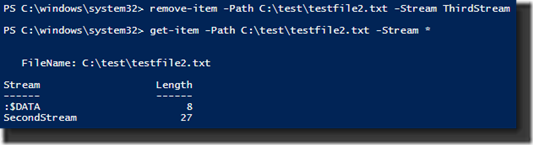
And finally, we can remove an ADS using the Remove-Item cmdlet.
Now we know what ADS is, how to query for ADS, how to create ADS, and how to delete ADS. So what is the big deal?
The big deal is that since ADS isn’t easily visible, it has become a cute way to hide data. Unfortunately it has also been used in the past to hide malicious code. This is how ADS got a bad name. In fact, a number of people that approach me about ADS already know that they have files with alternate data streams and they think they are infected with viruses.
Calm down. The mere presence of an ADS doesn’t mean that there is a problem. In fact, Microsoft uses ADS for a number of functions. I can almost guarantee that if you are reading this, you probably have some ADS on your computer. Let’s take a look at a couple examples.
Internet Explorer: Ever download an executable file from the Internet and then get warned about it when you ran it? How does that work?
When the file is downloaded, IE slaps an ADS on it. The stream will store a tag that tells Windows what zone the file was downloaded from.
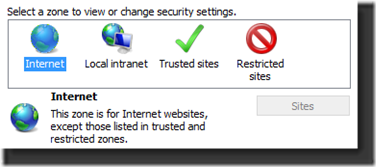
Look Familiar?
So using what I’ve learned so far, I can look at one of the files I’ve downloaded from the internet and see if there is an ADS on it.
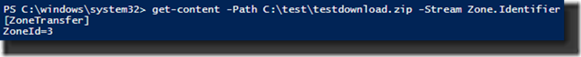
Yes, it is called ‘Zone.Identifier’. And then we can query the contents of the ‘Zone.Indentifier’ ADS.
Now we know that the file was downloaded from zone 3. Using the zone chart we can see it came from the Internet zone.
Value Setting
------------------------------
0 My Computer
1 Local Intranet Zone
2 Trusted sites Zone
3 Internet Zone
4 Restricted Sites Zone
Notice that my test download file is in a test directory. This means I moved the file here from my download directory. This is the cool thing about ADS, since it is part of the file, it moves with the file. Even if I copied it, the ADS would be on the new copy as well.
Other Internet browsers use ADS in a similar fashion.
File Classification Infrastructure: FCI is very dependent on ADS. The way that the classification works is that it puts tags on your files that allows you to keep track of what the file was classified as, no matter what happens with the file. It could be edited, copied, moved to another server, and its classification tags remain intact.
Others: Office files and Outlook Express file use ADS. And it isn’t limited to Microsoft programs. Numerous programs utilize the ADS functionality.
The point is that if you discover ADS on your system, it isn’t necessarily a bad thing. And just blindly stripping these data streams out of files can actually do a great deal of harm.
And now that you have some tools to use for querying alternate data streams, they won’t be so scary.
Thank you for your time and I hope this was educational.
Robert Mitchell
Senior Support Escalation Engineer
Microsoft Corp.