Requirements to save Bitlocker Recovery Key to AD using MDT
My name is Naziya Shaik and I am a Support Escalation Engineer with Windows Core team @ Microsoft. I would like to share information about enabling BitLocker while deploying operating system via MDT and the group policies that are required to be configured in AD DS.
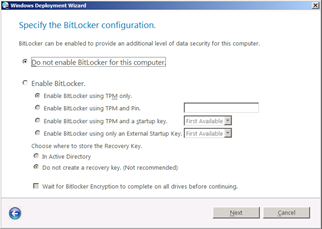
If you use Microsoft Deployment Toolkit to deploy Windows one of the prompts during Lite Touch is the prompt to enable Bitlocker Drive Encryption and you are given the option to save the bitlocker recovery key “in active directory”. See Figure 1
Figure 1. Bitlocker prompt during Lite Touch
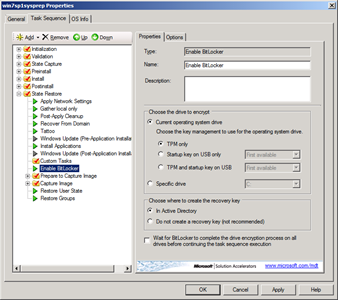
You can also enable the step manually in the task sequence. See Figure 2
Figure 2. Bitlocker step in TS
The issue we have seen is that some customers believe that this is all that is required to save the recovery key to active directory.
In order for MDT to save the recovery key to active directory you must at a minimum enable the following group policy:
Deploying Windows 7 with Windows Server 2003 or Windows Server 2008 DC
Path to GP: Computer Configuration\Administrative templates\Windows Components\Bitlocker Drive Encryption
Policy: Turn on Bitlocker backup to Active Directory Domain Services
Deploying Windows 7 with Windows Server 2008 R2 DC
Path to GP: Computer Configuration\Administrative templates\Windows Components\Bitlocker Drive Encryption\Operating System Drives
Policy: Choose how Bitlocker-protected operating system drives can be recovered
Additional configuration may be required also depending on your scenario. For more information see “Backing Up BitLocker and TPM Recovery Information to AD DS”
The following blog refers to a script to back up the recovery information to AD DS.
How to backup recovery information in AD after BitLocker is turned ON in Windows 7
Naziya Shaik
Support Escalation Engineer
Microsoft Enterprise Platforms Support