Rights needed for user account when precreating a Cluster Name Object (CNO) on Windows Server 2008 R2 Failover Cluster
Greetings Cluster fans, John Marlin here again. In my previous blog, Rights needed for user account to create a Cluster Name Object (CNO) on Windows Server 2008 R2 Failover Cluster, I explained what rights were needed for an account in Active Directory when allowing the Failover Cluster to create the Cluster Name Account (CNO). In this blog, I will explain the minimum rights needed when objects are being pre-created.
In many companies, Active Directory is being locked down to prevent unwanted actions from occurring. One of these is to lock down the Default Computers Organizational Unit (OU) so that users cannot create objects. The Domain Administrators would rather precreate objects to:
1. Keep naming conventions to better identify where an object resides and what its role is, i.e. TXSQLDALBE (Backend SQL Server running in Dallas, Texas)
2. Create Organizational Units based of roles, services, or locations where the objects will reside.
3. Prevent non-Domain administrators from having full control permissions
These Domain Admins are also starting to offload the creation of Clusters to a specific group of users that do not have full rights in Active Directory.
I created a simple Domain User (John Marlin) and a Creating Clusters group which he is a part of (as well as default Domain Users Group). I created an OU called Clusters and removed Everyone from the rights.
I then manually created a new computer object that will be my Cluster Name Object (CNO) called TXSQLDAL in this Clusters OU, disabled it, and created my dnsHostName entry. On the Security permissions of this object, I added the Creating Clusters Group with the following rights.
On the initial rights window, I selected:
Read
Allowed To Authenticate
Change Password
Receive As
Reset Password
Send As
Validate write To DNS Host Name
Validate Write To Service Principle Name
Read Account Restrictions
Write Account Restrictions
Read DNS Host Name Attributes
Read MS-TS-GatewayAccess
Read Personal Information
Read Public Information
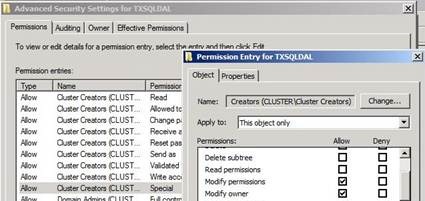
You then would need to select the Advanced button to create a couple additional Special Permissions. If you sort by accounts and edit the entry for this account that says "Special", you will need to select these permissions:
Modify Permissions
Modify Owner
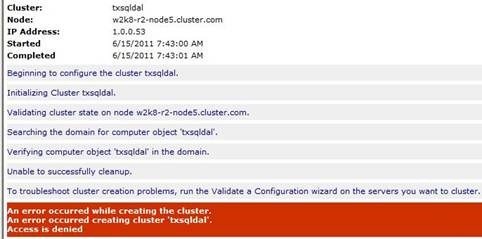
Once this was done, I can successfully create the Cluster and the Cluster Name came online. If all these rights are not in place, you can receive one of the below. The first is an Access Denied error attempting to create the Cluster
If you have enough of the rights, but not all listed or remove Authenticated Users from the OU permissions, it may create the Cluster, but the Cluster Name will fail to come online. In the System Event Log, you will receive the following:
Event ID: 1207
Source: FailoverClustering
Description: Cluster network name resource ‘Cluster Name’
Cannot be brought online. The computer object
associated with the resource could not be updated
in domain ‘X’ for the following reason:
Unable to get computer object using GUID
If you generate a Cluster Log and review it, you will see the following:
Trying to find computer account TXSQLDAL object GUID <GUID>
Search for existing computer account failed. Status 8007200A
Trying to find object <GUID> on a PDC
Unable to find object <GUID> on a PDC
So ensure you have all of the rights above are in place on both the object and the OU (at least READ).
Since you are precreating the CNO, you are also going to be precreating Virtual Computer Objects (VCO). One note about this is to ensure that the CNO and all of its VCOs are in the same OU. Since the Cluster Name Object (CNO) is the account that will need permissions, on the VCO Security tab, you need to add just on the initial window:
Read
Allowed To Authenticate
Change Password
Receive As
Reset Password
Send As
Validate write To DNS Host Name
Validate Write To Service Principle Name
Read Account Restrictions
Write Account Restrictions
Read DNS Host Name Attributes
Read MS-TS-GatewayAccess
Read Personal Information
Read Public Information
The Modify Permissions or Modify Owner on this object is not needed as the CNO is already given the rights to do what it needs. You are able to successfully bring the VCO online.
All of the documentation we have recommends Full rights on the Active Directory objects; however, if you lock things down, these are the minimum rights you will need. Please keep in mind that if you do call into support and the particular issue appears as related to these permissions, you may be asked to set them as per the recommendations to see if resolves.
Happy Clustering !!
John Marlin
Senior Support Escalation Engineer
Microsoft Enterprise Platforms Support