DNS Server and Zone Reporting with PowerShell
Who-Is On First?
While working on DNS automation for a customer recently I needed some quick scripts to inventory Active Directory-integrated DNS server and zone configurations. All too often the way we think things are configured does not match reality. Are the forwarders consistent and correct? Is scavenging enabled where you thought it was? Do the right zones have aging enabled? Are the zones stored at the domain or forest level? Today's script is an easy way to check.
NOTE: This article references many DNS terms and concepts. If these are unfamiliar to you I would recommend reading up on DNS using the links on this page. https://aka.ms/AD101
This post covers two custom DNS report functions:
- Export-DNSServerIPConfiguration
- Export-DNSServerZoneReport
These reports are key to auditing the DNS configuration of your AD environment. You will be able to quickly spot configuration anomalies at a glance.
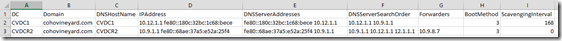
Here is a sample from the DNS server IP configuration report (click the image for a larger view):
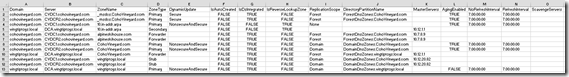
Here is a sample from the DNS zone report (click the image for a larger view):
These functions take a parameter of Domain. This can be a single domain or a string array of multiple domains. Then here is the tricky part. My customer still had Windows Server 2003 domain controllers, therefore the handy AD cmdlets were not available to get a quick list of DCs to query in each domain. Rather than install the AD Web Service I chose to fall back to the trusty NLTEST utility to get a list of DCs in each domain. We are assuming here that all DCs are running AD-integrated DNS. If not, that is OK, you will just get an error on the DCs not running DNS. The rest of the report should be fine.
NOTE: I have run into multiple customers using RiverBed devices. These may show up in the DC list. You can ignore them.
PowerShell
Here is some sample code for how to run the reports:
# Dot source to import the DNS functions
. .\DNSFunctions.ps1
Export-DNSServerIPConfiguration -Domain 'contoso.com'
Export-DNSServerIPConfiguration -Domain 'contoso.com','na.contoso.com'
Export-DNSServerZoneReport -Domain 'contoso.com'
Export-DNSServerZoneReport -Domain 'contoso.com','na.contoso.com'
These functions need to run from Windows Server 2012 or above with the DnsServer PowerShell module available. You could also run it from a Windows 8.0 or above workstation with the DNS Remote Server Administration Tools (RSAT) installed. The functions can target servers running Windows Server 2003 or above.
Download this DNS function library at the TechNet Script Center .
"If DNS ain't happy, ain't no one happy."
The secret to happy DNS is maintaining the following configuration points, especially when adding or removing domain controllers or DNS servers:
- NS records
- Delegations
- Forwarders
- IP DNS lookup servers
- Scavenging
- Aging
Scan all of the IPs in the server report to make sure they are all still valid. I commonly find IPs of old DCs that are long gone. They may be listed as forwarders or lookup servers. You will also want to manually inspect these on the NameServer tab of your zones and subzone delegations.
The zone report includes a column called Scavenging Server. In most cases this column should be empty. If there is an IP in this column, then that is the only server allowed to scavenge the zone. Maybe that is why scavenging never worked on that zone.
Armed with these reports you have the start of a great way to audit DNS health in your environment. It is a good idea to run these every time you add or remove a DC, install a new DNS server, or otherwise adjust your DNS configuration. I would run them both before and after your changes. Hey, these could even suffice for your change control validation plan!
DNS Scavenging Pro Tip
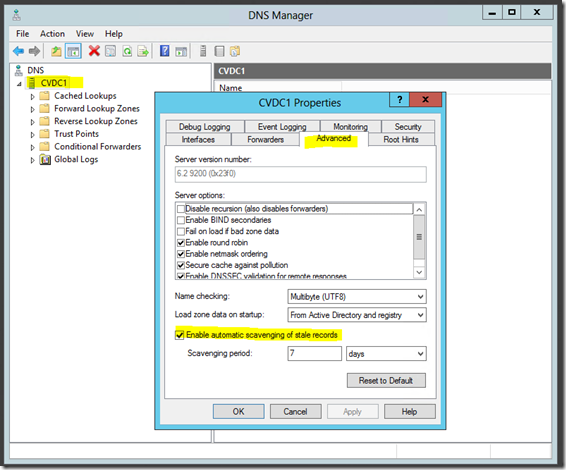
Sometimes I find DNS scavenging turned off on all domain controllers. Sometimes the customer wonders why it stopped running. Ideally it should be running on one or two DCs that also run DNS. Often the root cause is that when they replaced the last DC running scavenging they forgot to reconfigure it on the new one. Add a checkbox to your DC lifecycle checklist to re-check the box for scavenging if it was there previously (DNS Manager, server Properties, Advanced tab, Enable automatic scavenging of stale records). Don’t do this for every DC, just the ones designated for scavenging according to your design. Today’s DNS report can help you validate this. Look for the number of hours listed in the ScavengingInterval column of the DNS server IP configuration report. This tells you which DCs are running the scavenging task.
But wait, there’s more!
We have reports similar to this in our Microsoft Premier AD RAP as a Service offerings. Imagine getting this kind of detail across all domain controllers in your forest for replication, patching, AD database, sites, subnets, and more. If you like today's reports, then you will love using the AD RAP as a Service tool which has so much more to offer across all areas of Active Directory reporting and analysis.