Modern Management of Internet Clients
The release of ConfigMgr Tech Preview – 1705 introduced new cloud based client management capabilities like on-boarding Azure AD users and deploying ConfigMgr client over Internet.
Common scenarios like BYOD or Un-Managed/Workgroup devices in the field can now join Azure-AD which gets enrolled into Intune & automatically pushes the ConfigMgr agent for full management.
The coolest part is the Azure-AD joined devices won't even require a client auth. certificate for HTTPS communication.
Here's a step by step accomplishing the same –
- Configure Azure Services in ConfigMgr Console
- Prepare Azure for Device registration
- Cloud Management Gateway
- ConfigMgr Client Package
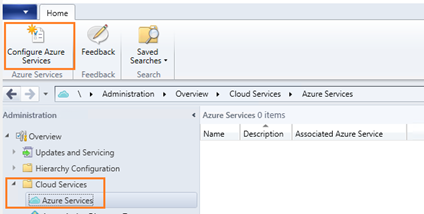
Configure Azure Services in ConfigMgr Console
The first step is to associate Azure AD with ConfigMgr & discover the AAD users. This piece is critical because the information will be cross-verified when the clients from Internet try to register.
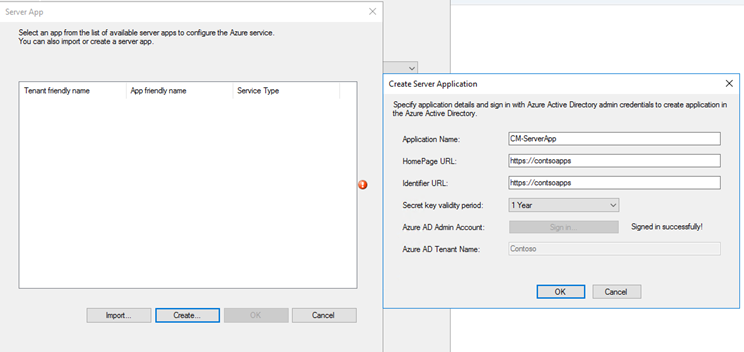
Run the wizard to create a Server App & Client App
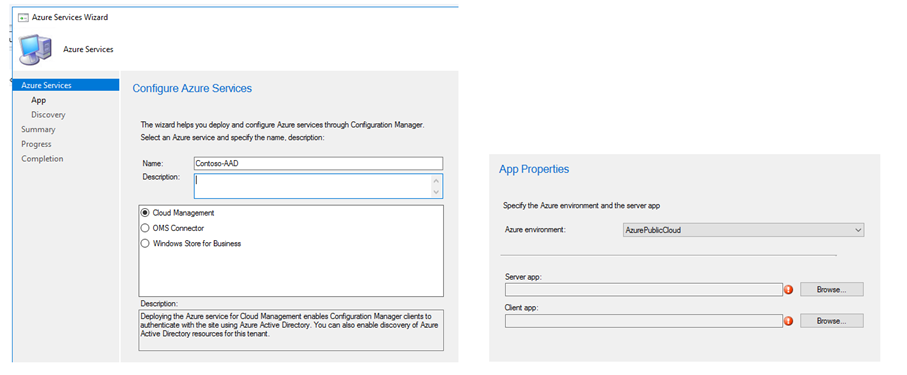
The Application Name, HomePage & Identifier URLs can be anything.
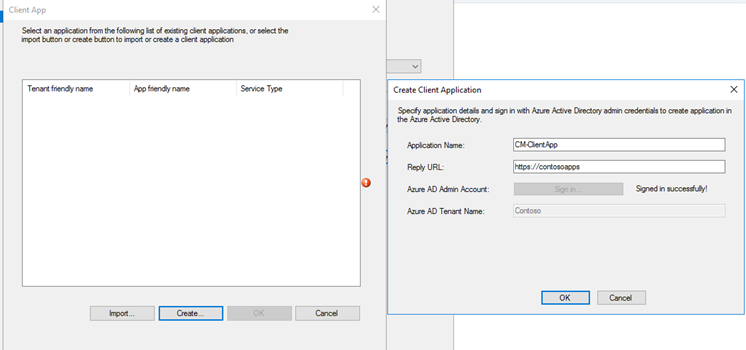
Follow the same steps to create Client Application. You can re-use the same URL used above.
Enable Azure AD Discovery.
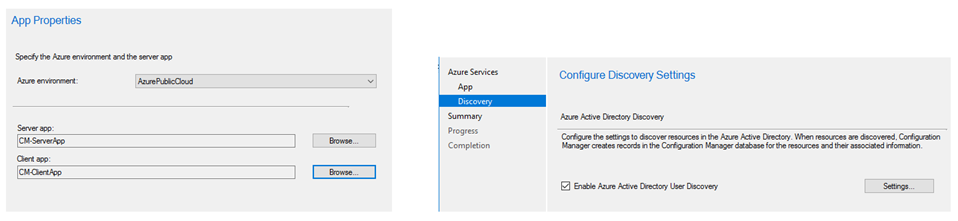
Click OK and finish the wizard.
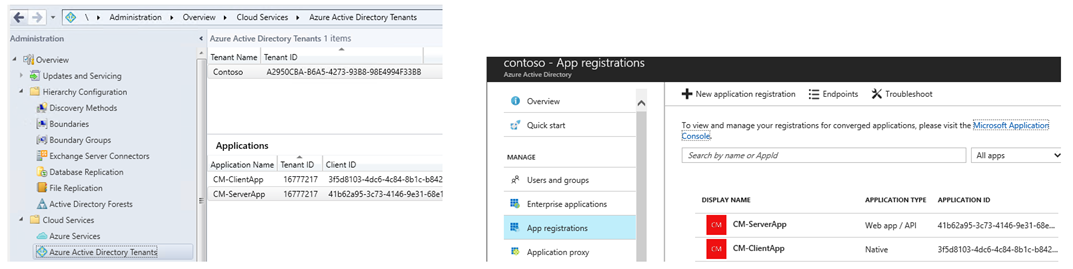
You can verify the Server and Client Apps created in Azure and listed in ConfigMgr console.
From Azure console select Server App [CM-ServerApp in my case], click Grant Permissions and click Yes. Although the app is already configured for Read Directory Data, this step is still necessary to activate.
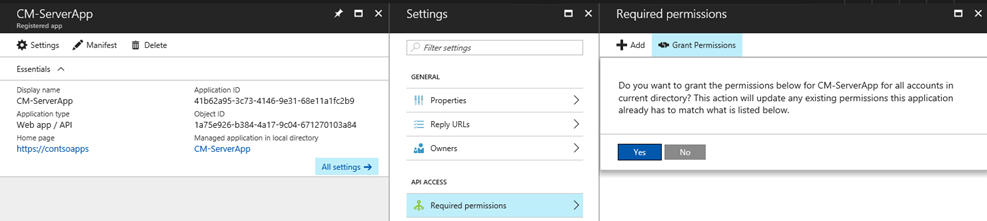
Repeat the above steps for Client App [CM-ClientApp in my case]CM-ClientApp. It's important to follow this order else the discovery will fail.
In case you are wondering where to look for this info. there is a new log file for this component named - SMS_AZUREAD_DISCOVERY_AGENT.log
ERROR: Error occurred. StatusCode = Forbidden, reason = Forbidden SMS_AZUREAD_DISCOVERY_AGENT [Failed]
Total AAD Users Found: 9. Total AAD User Record Created: 9 SMS_AZUREAD_DISCOVERY_AGENT [Success]
Full sync completed successfully at X:XX:XX SMS_AZUREAD_DISCOVERY_AGENT
Successfully published UDX for Azure Active Directory users. SMS_AZUREAD_DISCOVERY_AGENT
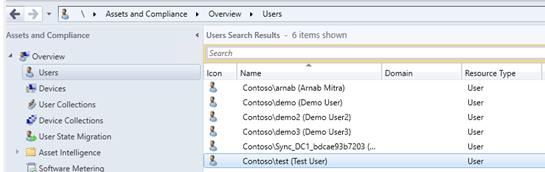
Prepare Azure for Device registration
Allow users to join their devices to Azure AD.
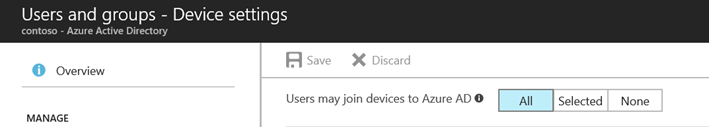
Make sure, MDM authority is set to Intune.
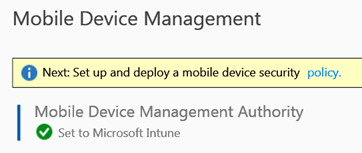
This will allow the machine to join to Azure AD and enroll to Intune.
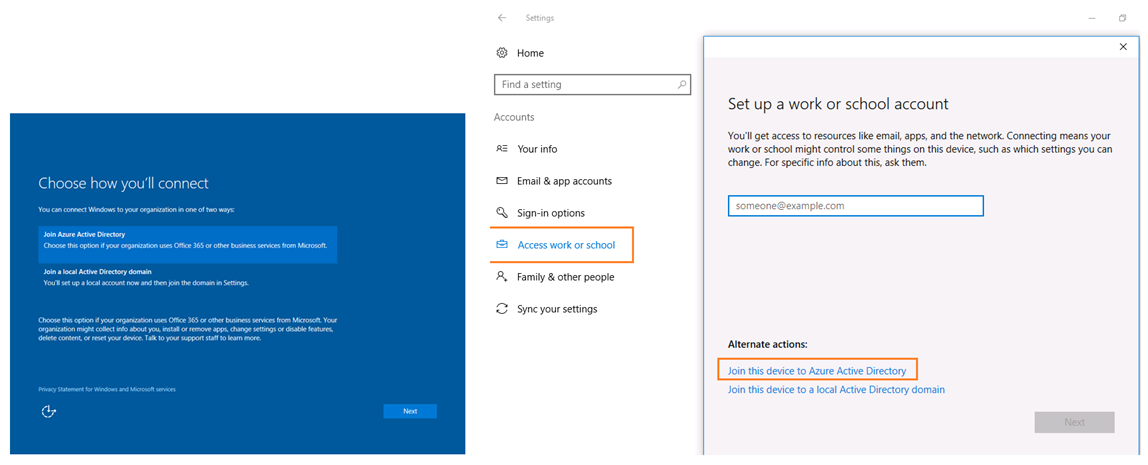
Cloud Management Gateway
In case you haven't already configured one before, follow the step by step blog post.
Since its possible to host CMG on a HTTP-MP, an important requirement in this scenario is to ensure the MP communicating with CMG is on HTTPS mode.
Additionally, install ASP.Net 4.5
ConfigMgr Client Package
Finally, it's time to deploy the client over internet. You can leverage Intune to do this job.
Intune supports deploying .msi files, we will use ccmsetup.msi with command line parameters to install the ConfigMgr agent.
From Azure console, open Intune > Mobile Apps and Add app, choose Line of business app, browse to CCMSetup.msi
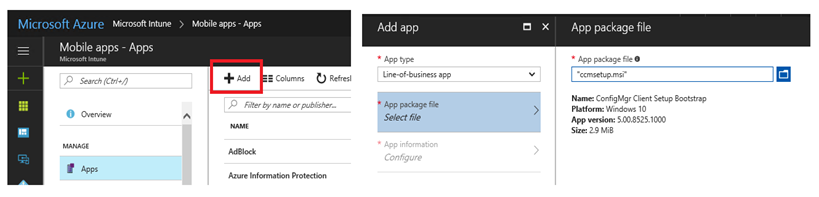
The App information has the name auto populated, you can modify and add additional information.
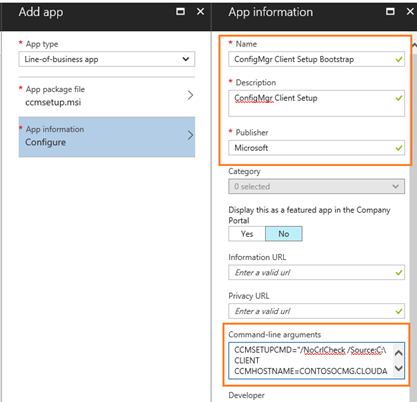
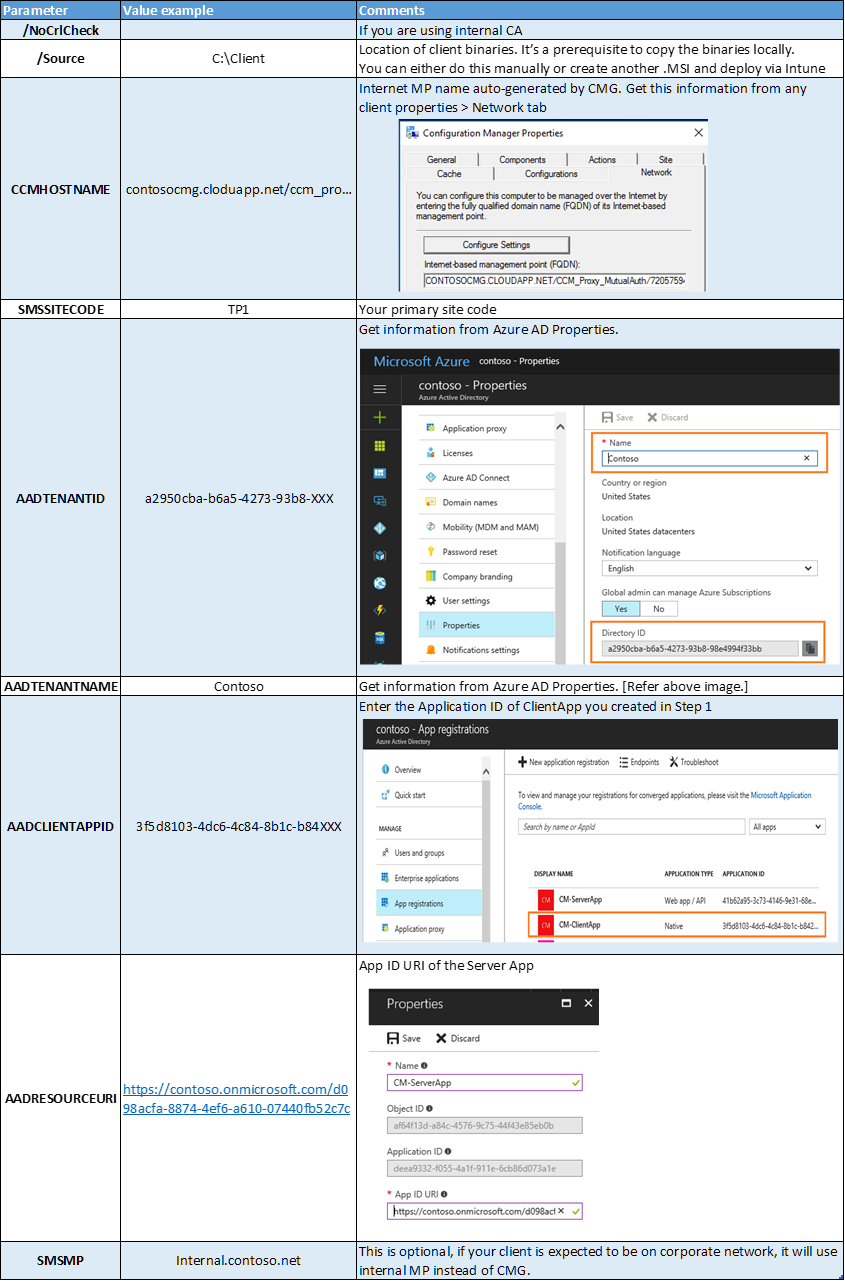
In the Command-line box enter info as the reference table below = CCMSETUPCMD="/NoCrlCheck /Source:C:\CLIENT CCMHOSTNAME=CONTOSOCMG.CLOUDAPP.NET/CCM_Proxy_MutualAuth/720575XXXX SMSSiteCode=TP1 AADTENANTID=a2950cba-b6a5-4273-93b8-98e4994f33bb AADCLIENTAPPID=3f5d8103-4dc6-4c84-8b1c-b842XXX AADRESOURCEURI=
https://contoso.onmicrosoft.com/d098acfa-8874-4ef6-a610-07440fb52c7c AADTENANTNAME=Contoso"
Table reference for the command line switches –
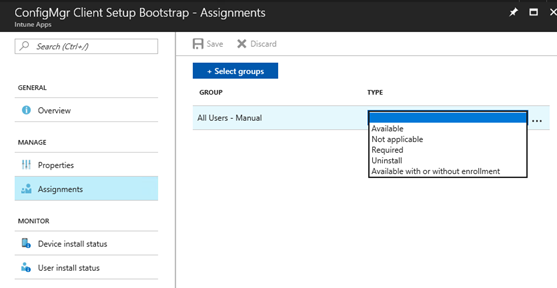
Once the app is ready, go to Assignments tab to deploy against a group. The app can be Available/Required
Testing & Validation
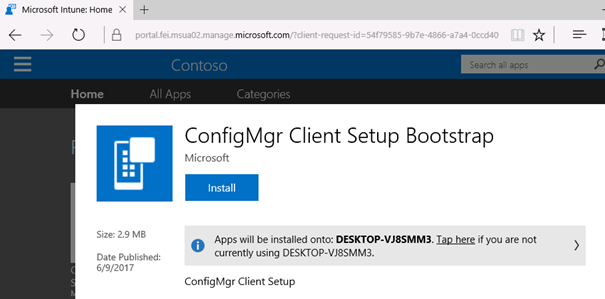
Login to an Azure-AD joined device with your Azure AD credentials. Based on the above configuration, the ConfigMgr client will either install automatically or will be available.
In my case I left it as available and logged on to https://portal.manage.microsoft.com to install.
You can review the CCMSetup.log for troubleshooting. If you don't see any log and wondering if Intune even kicked off the install, you can review the MDM Event logs - Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin
Here's a screenshot post a successful client registration. The device will be listed in ConfigMgr console
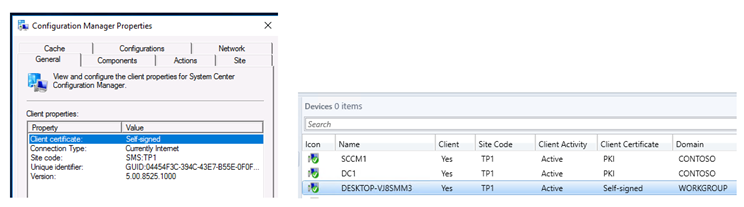
Troubleshooting Tips –
- Ensure you are logged in with AAD User ID
- Check ADALOperationProvider.log – To validate successful association of the existing AAD User with ConfigMgr onboarded in Step1.
- Check CCMMessaging.log – To validate successful connection to gateway.
- If you didn't use public CA for CMG, you need to ensure the Client Root Cert is added to the Trusted Root CA on client machine.
With the installed client, possibilities are endless with more improvements coming in future releases.
Thanks,
Arnab Mitra