Lab Ops 19 – Software Defined Networking - where’s my stuff
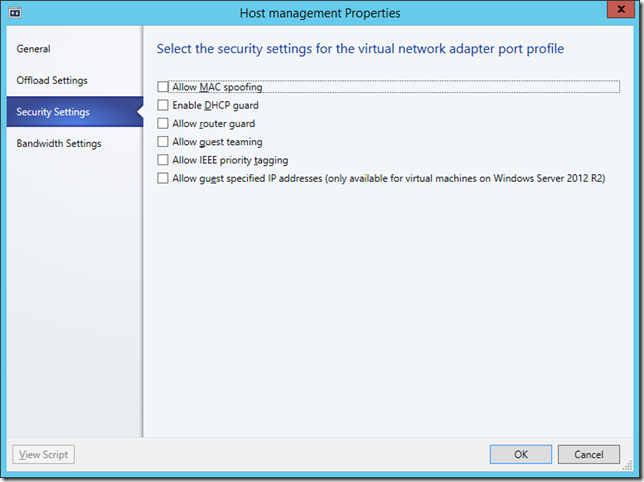
Well done if you got through my last post, I bolted a lot of stuff together and it all looks a bit confusing particularly if you are moving from Hyper-V to System Center Virtual Machine Manager 2012 (VMM). For a start where’s my network settings? When I was testing my rig I found I couldn’t swap out the network connectivity on a test VM from an internal virtual switch to my shiny new VM Network, and when I looked at the error it said I couldn’t change the MAC address of a running VM. What was going on here was that Hyper-V had assigned a static MAC address at random to my VM and by assigning it to my new VMM infrastructure it wanted to assign a new one. This got me to wondering about MAC address spoofing which can be important for legacy applications and in Hyper-V you can do this from the advanced features of the Network adapter on a VM. In VMM MAC address spoofing is part of a Virtual Port Profile which also allows us to set the other advance features of Networking in Hyper-V like bandwidth management guest NIC teaming as well as router and DHCP guard..
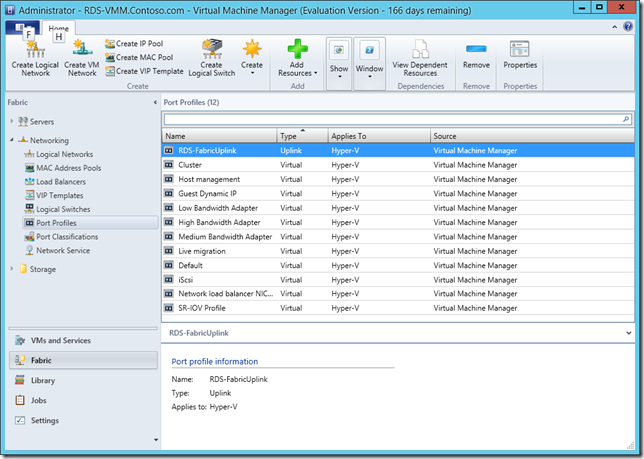
Virtual Port Profiles are just logical groupings of these things which you can assign to a logical switch and there are off the shelf ones like Guest Dynamic IP and the Host Management profile we use last time. This might seem an unnecessary extra step but now that we live in a world of NIC teaming we need to identify the different type of traffic flowing down a fat connection. We can also see Uplink Port Profiles in this list..
such as the RDS-FabricUplink I created in my last post, which allows us to connect a logical network and specify how that port gets teamed. A logical switch has one or more uplink port profiles connected to it and has virtual ports to specify one or more port classifications to describe what traffic this switch can handle. At this point we can assign the switch to as many hosts as we want and each one will inherit all these properties:
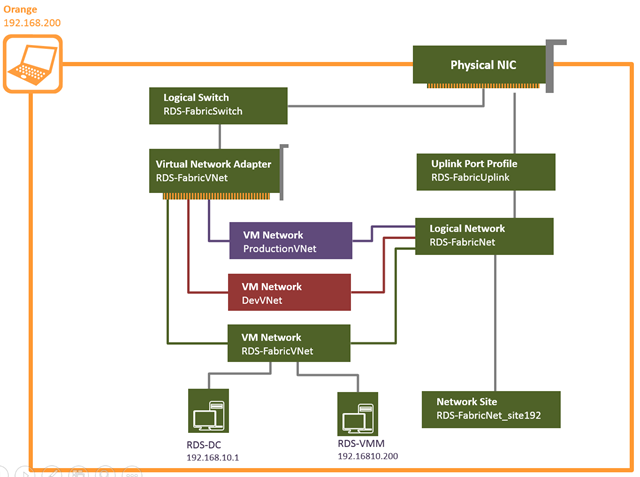
- The logical switch appears as a Virtual Switch in Hyper-V and is bound to a NIC or team on that host. When we do that we can see it’s the Uplink Port Profile that is passed to the NIC
- Underneath that we have one or more Virtual Network adapters which are associated to a VM Network and a Virtual Port Profile.
When we attach VM to a VM network many of the properties are now greyed out (like those MAC address settings ).
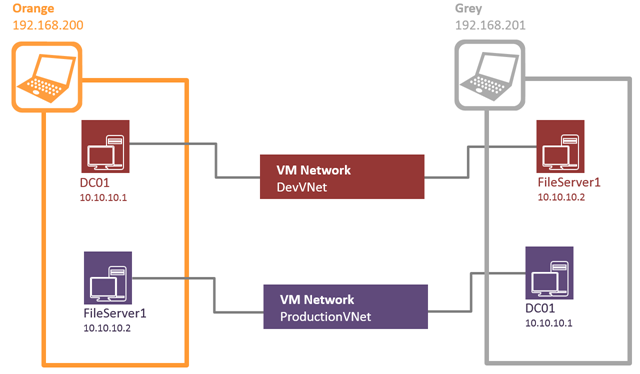
Anyway I am now ready to create a couple of VM Networks for Dev and Test on which I can put identical VMs without them seeing in each other but also allow them to span hosts ..
To do this I need to create the two VM Networks and integrate them into the networking fabric, by associating them with my logical network (RDS-FabricNet) I created in my last post, and here’s the PowerShell:
Import-Module VirtualMachineManager
$logicalNetwork = Get-SCLogicalNetwork -Name "RDS-FabricNet"
# 2 x VMNetworks each with the same subnet
$vmNetwork1 = New-SCVMNetwork -Name "DevVMNet" -LogicalNetwork $logicalNetwork -IsolationType "WindowsNetworkVirtualization" -Description "Developer Virtual Network" -CAIPAddressPoolType "IPV4" -PAIPAddressPoolType "IPV4"
$subnet1 = New-SCSubnetVLan -Subnet "10.10.10.0/24"
New-SCVMSubnet -Name "DevVMNet Subnet 10" -VMNetwork $vmNetwork1 -SubnetVLan $subnet
$vmNetwork2 = New-SCVMNetwork -Name "ProductionVMNet" -LogicalNetwork $logicalNetwork -IsolationType "WindowsNetworkVirtualization" -Description "Developer Virtual Network" -CAIPAddressPoolType "IPV4" -PAIPAddressPoolType "IPV4"
$subnet1 = New-SCSubnetVLan -Subnet "10.10.10.0/24"
New-SCVMSubnet -Name "ProductionVMNet Subnet 10" -VMNetwork $vmNetwork2 -SubnetVLan $subnet
At this point You might be wondering about what to do about DNS and AD in this situation as we would normally assign fixed ip addresses to these. The answer is to start these VMs first and then they’ll get the lowest address by default where x.x.x.1 is reserved on the subnet for the switch. This is similar to Azure except that Azure hands out x.x.x.4 as the lowest address as there are three reserved addresses on a subnet.
Anyway the other thing we’ll want to do is specify the new traffic that will be carried on our virtual switch by these VM Networks and to do that we’ll add in another port profile.
$portClassification = Get-SCPortClassification -Name "Guest Dynamic IP"
$nativeProfile = Get-SCVirtualNetworkAdapterNativePortProfile -Name "Guest Dynamic IP"
New-SCVirtualNetworkAdapterPortProfileSet -Name "Guest Dynamic IP" -PortClassification $portClassification -LogicalSwitch $logicalSwitch -RunAsynchronously -VirtualNetworkAdapterNativePortProfile $nativeProfile
Our design now looks like this..
We can then assign these VM network to new or existing VMs and it will be available on any hosts we manage in VMM provided we connect those host to our virtual switch. To do that we need a process to create VMs and to do that we need somewhere to put them so next up Storage in VMM.