Stop listening to your remote users
If you have a mobile workforce, your most likely going to be listening to them complaining about remote access/VPN/RAS or whatever they call it. My wife is a case in point, she is running XP plus a load of third party software to lock it down to the point where it barely works and often won’t connect into the corporate VPN. All of this results in her calling the helpdesk at least once a week which isn’t good for her or good for them.
By contrast I also work at home, but the IT department (MSIT) are so proud of the solution they have come up with for remote workers they have a case study on how they do this. Their answer is a combination of DirectAccess (a built in role in Windows Server 2008 R2), and Forefront Unified Access Gateway (UAG). You can do this without UAG, but if you want down-level support XP clients / Windows Server 2003 then UAG is needed for this.
If you are using windows 7 clients, UAG adds extra security (for legacy apps etc.) and load balancing. For the IT Pro setting this up there is no client software involved and apart from a group policy update nothing to configure on the client as Windows 7 also has DirectAccess functionality built in.
But our our IT department is not stopping there, and I am now on an internal beta (we call it dogfood) which uses the Trusted Protection Module (TPM) built into many modern PCs instead of using a PIN & smartcard. You may have heard of the TPM as a prerequisite of BitLocker, the disk encryption system built into Vista and Windows 7. BitLocker is mandatory for Microsoft client machines and this latest incarnation of our DirectAccess deployment relies on that being implemented.
What does this look like for me as an end user?
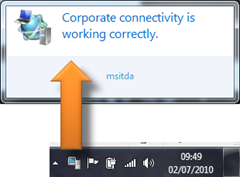
The only indication I have that I even have DirectAccess is this notification in the system tray..
which kicks into life as soon as I have any kind of internet access, without any intervention from me, so as I am typing this at home I could hit any of the many corporate web sites to book leave, download some dogfood or remote desktop into one of the machine I have left at the office.
Another annoying remote worker niggle that DirectAccess removes is that it will work over the standard ssl port where third party solutions are normally blocked, and so it works on virtually any public wi-fi networks e.g. hotels, cafes, client sites etc.
It’s also intelligent enough to route traffic efficiently - if I hit an internet site while I’m connected that goes through my ISP as normal and doesn’t get rerouted through the VPN and out onto the internet from the corporate network, so I still have the same internet access performance as I had before and I haven’t slowed down the office network either .
So if you want to stop listening to all of those users with VPN support calls then you could try this out on a few VM’s using this deployment guide to get you started. Then you can call your users to have a discussion about the feasibility of using DirectAccess in your organisation.