Configure ADFS and Device Registration service in Windows 2012 R2
Installing ADFS federation server:
In the previous blogs we looked at the different new features in ADFS in Windows 2012 R2 and the installation requirements.
In this article we will look at the installation of ADFS service and enabling Device Registration service in Windows 2012 R2.
Installing ADFS federation server:
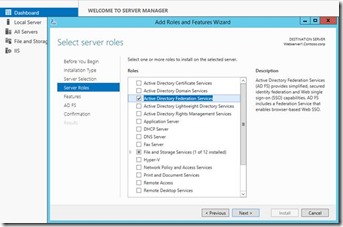
1. Install the ADFS role service from Windows Server manager. In Windows 2012 R2 you can remotely install the roles on server.
2. Click Next > Next > Next > Install to install the ADFS role.
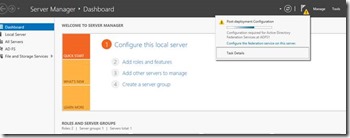
3. Go to the server manager notification and click on Configure the ADFS service
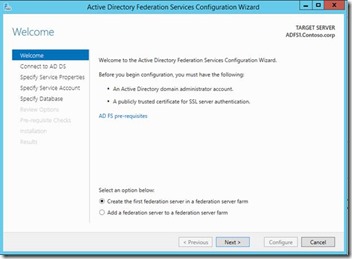
4. Make sure the requirements given in the below screenshot are met before you proceed to next step. Select whether this is the first federation server in a federation server farm or a new server in existing federation farm.
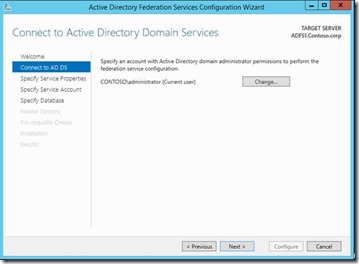
3. Provide the credentials for domain admin account to configure ADFS service as mentioned below:
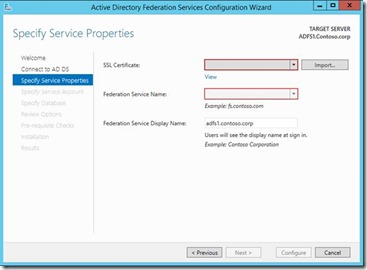
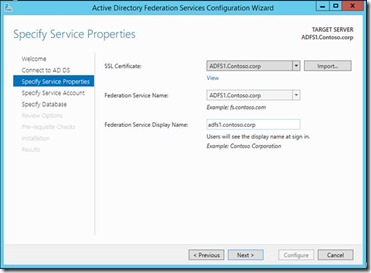
4. Select the ADFS certificate which is installed on the ADFS server. Obviously the federation service name should be same as the name used in the ADFS certificate.
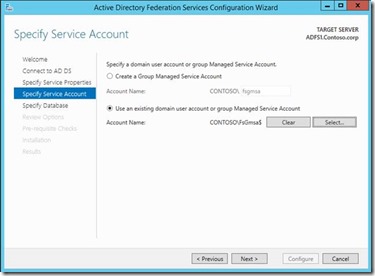
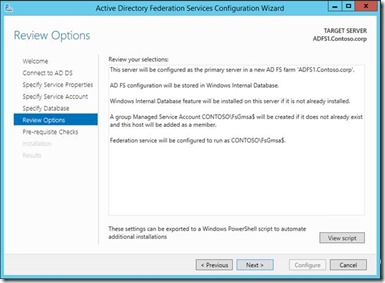
5. Here you can specify a domain user account or Group Managed Service Account. Group Managed Service Account (GMSA) is a new feature in Windows 2012, which is an improvement to the managed service account in Windows 2008 R2. GMSA are managed domain accounts that provide automatic password management and simplified SPN management, including delegation of management to other administrators. The group Managed Service Account provides the same functionality within the domain but also extends that functionality over multiple servers.
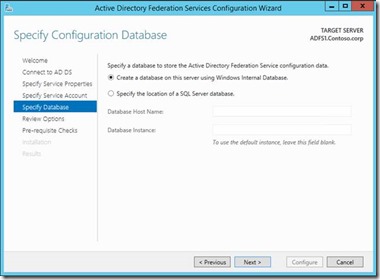
6. You can select a SQL server database or the Windows internal database to host the ADFS configuration database
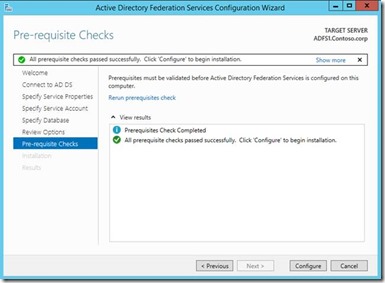
7. Click configure and that finishes the ADFS configuration.
8. There are few additional steps to enable the Device registration service:
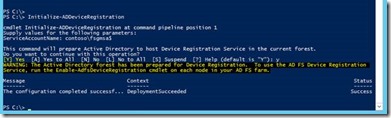
Initialize the ADDeviceRegistration service on ADFS server
Enabled the ADFS Device Registration service
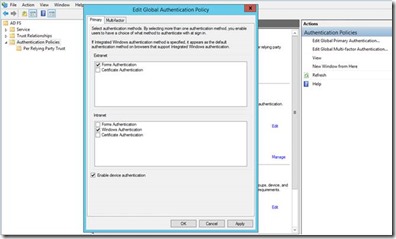
Enable device authentication in ADFS management console:
You can try the following methods to test the functionality of ADFS service:
https://adfs1.contoso.com/federationmetadata/2007-06/federationmetadata.xml - this should return the metadata xml file
https://adfs1.contoso.com/adfs/ls/idpinitiatedsignon.aspx - This should return the ADFS login page
In Next section we will look at the Web Application Proxy which has replaced the ADFS Proxy service role in Windows 2012 R2. We will also look at publishing DRS via WAP.