What’s New in Active Directory Domain Services in Server 2012? AD – Server 2012
Don’t we all love to know what’s new in AD DS? Here’s a quick peek
The New Stuff in AD DS Server 2012 can merely be categorized into two types “new” and “improved”. Either way both are Eye Catching.
1. Virtualization Improvements
Server 2012 is powered with great Virtualization improvements which are much needed in Day today’s domain management not only in high scale environments but also for the ease of management.
- CLONING
You can now clone your Domain Controller. Yes you heard me right “Cloning” is the new feature which allows you to deploy replicas of your single domain controller across your environment.
Process of Cloning involves creating a copy of your exiting virtual DC after authorizing the source DC to be cloned in AD DS. Then Creating a configuration file that contains detailed information (hostname, IP address, DNS servers, etc.) or you have an option to leave it blank by allowing the system to fill that for you. This process not only reduces the steps and time involved but allows you to fully deploy Additional DC’s which are authorized for cloning by Domain administrator.
- SAFE GUARDING
AD DS is not new to virtualization, however the features present in most hypervisors can sometimes just not work right with AD replication algorithms (For example logical clocks). In server 2012, a virtualized DC uses a unique identifier which is exposed by Hypervisor called the Virtual machine GenerationID. Virtual machine GenerationID changes whenever there is a change in virtual machine state (for example during boot or before completing any transaction). Virtual machine running DC will compare its Virtual machine GenerationID against the value store in Directory. Mismatch in the ID can event for a rollback and AD DS would allow DC to talk on other DC’s in the environment to give it its current state of information and prevent it from creating duplicate SID’s. This will only work if your hypervisor is Virtual machine GenerationID aware.
Visit the link for detailed information: AD DS Virtualization
Also Read: How to Cloning Virtual Domain Controller In Server 2012
2. Easy Deployments and Upgrades
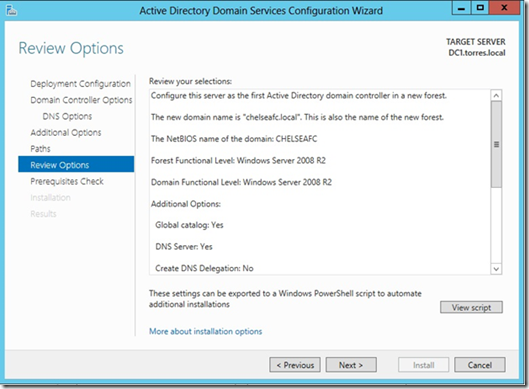
AD DS in Server 2012 brings together all the steps required to deploy a new DC into One single Graphical Interface. It can do all the good things together saving the additional task which Domain Administrators have it written in the check list. It is built on windows PowerShell in line with Server Manager to target multiple server and remotely deploy DC’s , bringing in smile on end user experience.
Few task that can be automated through the GUI - We can preparing the Domain for DC promotion as adprep.exe in included in the GUI, we can install AD DS server roles remotely, when deploying multiple DC’s across wide geographical locations. This would also correct any prerequisites which are necessary. Below is a sample of how the GUI looks like.
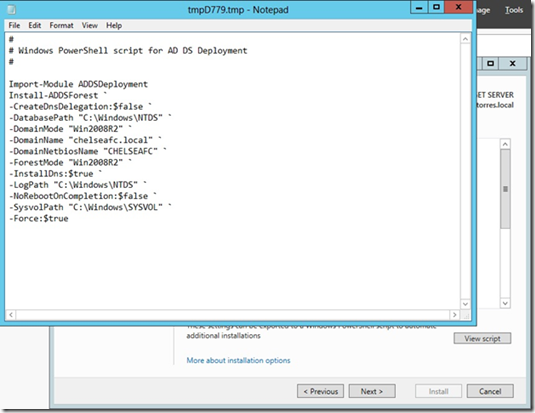
You can also view Scripts to look at the power shell commands.
3. Simplified Management
- Dynamic Access Control
DAC brings the next level of Access Control which allows Administrators more express more based on modern day challenges in regulatory and business requirements. It enhances the existing model by introducing user – claims, device -claims or User + device claims (AKA Compound identity). Authorization decisions can be made based on new central access policies (CAP) model and File-Classification.
You try accessing a file share and get an ACCESS DENIED. As a user, you’d be glad if someone explains to you why you do not have necessary permissions on the share and also gives you an opportunity to report it to the authorized controller with a dialog box.
Auditing has been made more granular and same time more flexible and simpler.
Visit the link for Scenario Overview: Dynamic Access Control
- Direct Access Offline Domain Join
DirectAccess offline domain join is a process that computers running Windows Server 2012 and Windows 8 can use to join a domain without being physically joined to the corporate network, or connected through VPN. Offline domain join for DirectAccess provides DirectAccess policies to clients to allow remote provisioning.
In short, just join the computer over the internet. (You will need DirectAccess for this)
Visit the link for detailed information: DirectAccess Offline Domain Join
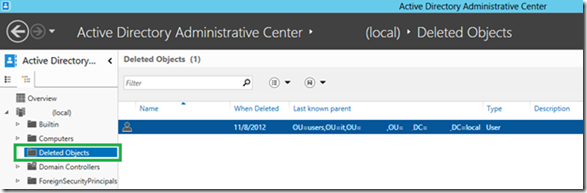
- Active Directory Recycle Bin User Interface
AD Recycle bin was introduced in 2008 R2, but was limited to PowerShell only, now you a GUI
Visit the link for Details: Active Directory Recycle Bin
- Active Directory Federation Services (AD FS)
AD FS now does not need to be installed separately and has multiple improvement. Watch out the space for an upcoming blog on AD FS
Visit the link for Details: AD FS
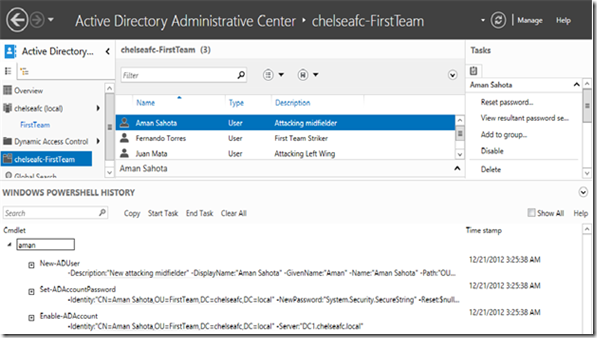
- Windows PowerShell History Viewer
Since PowerShell is the way forward we look to increase the learning experience. Every UI action can be viewed into PowerShell cmdlets.
- Active Directory Replication and Topology windows PowerShell cmdlets
When an Administrator hears about an AD Replication issue, First thing he would look for are the AD tools to view the result of the replication state such as repadmin, ntdsutil & AD sites and services.
Using PowerShell all of the tools can be incorporated in easy and powerful scripting experience. It’s consistent and compatible with other windows PowerShell cmdlets.
Visit the link for Details: AD Replication and Topology PowerShell cmdlets
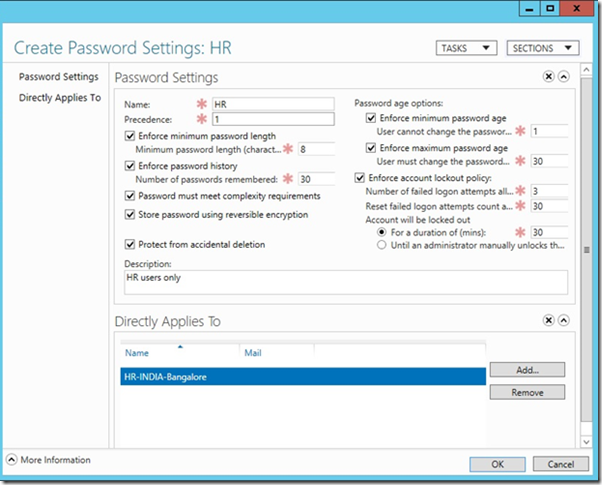
- Fine Grained Password Policy User Interface
In order to leverage on the 2008 FGPP with more precise management, UI has been introduced which allows administrators to create, edit and assign which much minimum trial and error administration.
Visit the link for Details: FGPP
- Active Directory Based Activation (AD BA)
We all know how windows activation worked in the past or even in 2008. Using the AD BA, You can activate your clients using Active Directory Infrastructure. However please be noted only windows 8 clients can leverage the feature.
Visit the link for Details: AD BA
- Group Managed Service Accounts (gMSA)
Managed Service Accounts were introduced in 2008 R2 and Win 7, these are managed domain accounts which provided password management to run a service or any related administrative task. GMSA extends the same functionality to multiple servers in the domain. This can be helpful while connecting to a service hosted on a server farm or NLB.
Visit the link for Details: gMSA
4. AD DS Platform Changes
Some of the enhancements may not be common to an administrative point but surely it’s a way forward.
- AD DS claims in AD FS
- Relative ID (RID) Improvements
- Deferred Index Creation
- Kerberos Enhancements.
There is tremendous effort put in Server 2012 AD DS platform architecture, which is enhanced to improve the Design and scalability. This altogether benefits the performance which an Administrator would love to see.
Hope you find this Informative.
Happy Reading! ![]()