Kerberos Error KDC_ERR_POLICY while trying to access a resource in the Trusted forest (Forest Trust)
Symptoms
Forest1 = 2003dom.local
Forest2 = 2008dom.local
2-way Forest Trust created between them, with forest level authentication.
**User from Forest2 access a server in Trusted Forest1 i.e. [\\2003-dc1.2003dom.local](file:///\\2003-dc1.2003dom.local\)
Here is what I see in the network capture on the source machine in Forest2
2008-dc1.2008dom.local 2003-dc1.2003dom.local KerberosV5:TGS Request Realm: 2003DOM.LOCAL Sname: cifs/2003-dc1.2003dom.local 2003-dc1.2003dom.local 2008-dc1.2008dom.local KerberosV5 KerberosV5:KRB_ERROR - KDC_ERR_POLICY (12)
After this Kerberos error, we fallback to NTLM. User gets prompted for credentials and when the credential for a user in Forest2 is provided, that fails too.
**From Forest1 when accessing a server on Forest2 we see Kerberos error below. Here instead of the user getting a referral TGT for the trusted forest krbtgt/2008dom.local, we just see the local domain DC replying with error stating it could not find the service principal name. It never feels the need to go outside its forest.
2003-MEM1 2003-dc1.2003dom.local KerberosV5 KerberosV5:TGS Request Realm: 2003DOM.LOCAL Sname: cifs/2008-dc1.2008dom.local 2003-dc1.2003dom.local 2003-MEM1 KerberosV5 KerberosV5:KRB_ERROR - KDC_ERR_S_PRINCIPAL_UNKNOWN (7)
Fallback to NTLM works:
2003-MEM1 2008-dc1.2008dom.local SMB SMB:C; Session Setup Andx, NTLM NEGOTIATE MESSAGE
2008-dc1.2008dom.local 2003-MEM1 SMB SMB:R; Session Setup Andx, NTLM CHALLENGE MESSAGE - NT Status: System - Error, Code = (22) STATUS_MORE_PROCESSING_REQUIRED 2003-MEM1 2008-dc1.2008dom.local SMB SMB:C; Session Setup Andx, NTLM AUTHENTICATE MESSAGE, Domain: 2003DOM, User: AdministratoR, Workstation: 2003-MEM1 2008-dc1.2008dom.local 2003-MEM1 SMB SMB:R; Session Setup Andx 2003-MEM1 2008-dc1.2008dom.local SMB SMB:C; Tree Connect Andx, Path = \\2008-DC1.2008DOM.LOCAL\IPC$, Service = ????? 2008-dc1.2008dom.local 2003-MEM1 SMB SMB:R; Tree Connect Andx, Service = IPC
Cause
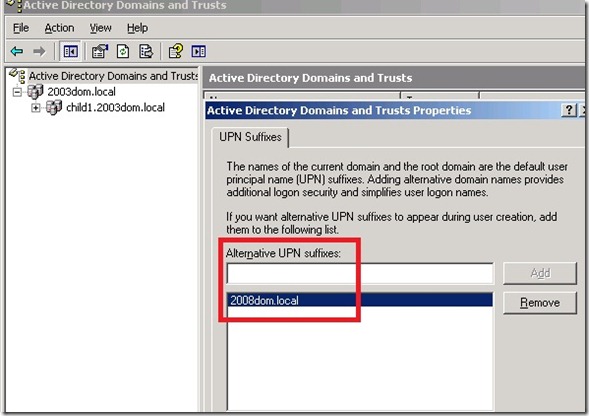
We found that Forest1 had domain suffix for the trusted forest (in this case 2008dom.local) added to the Alternate UPN suffix list for the forest.
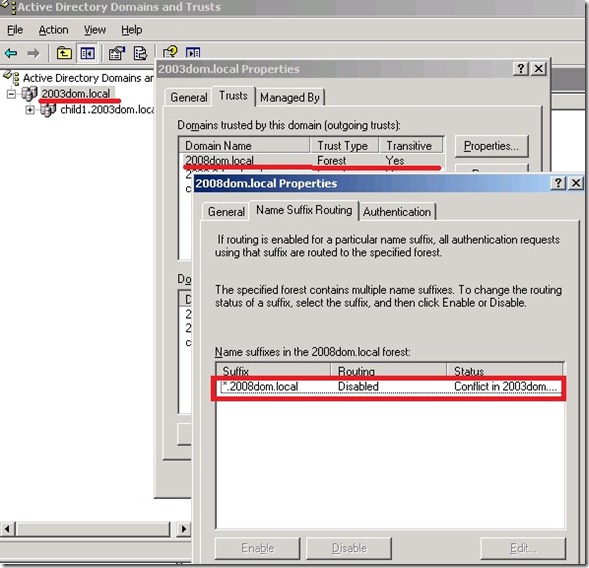
This had caused the name suffix for *.2008dom.local in the forest trust in the Forest1 (2003dom.local) go into a DISABLED state showing a conflict.
This also explains why the forest1 (2003dom.local) was throwing the Kerberos error KDC_ERR_POLICY, when issuing tickets across forest.
Resolution
- Remove Alternate UPN suffix from the Forest1, which is similar to the name suffix used in the Trusted domain/forest.
- After this change, we need to validate the trust (both incoming and outgoing) to update the UPN removal to the trust objects in both forest.
- Lastly, we need to Enable the Name suffix for the trusted domain using Trust properties > Name Suffix Routing tab, in Forest1.
Change the routing status of a name suffix
https://technet.microsoft.com/en-us/library/cc781019(WS.10).aspx
Routing name suffixes across forests
https://technet.microsoft.com/en-us/library/cc784334(WS.10).aspx