Netmon's view of Kerberos communication, when accessing resources across domains in the same forest.
Domain setup:
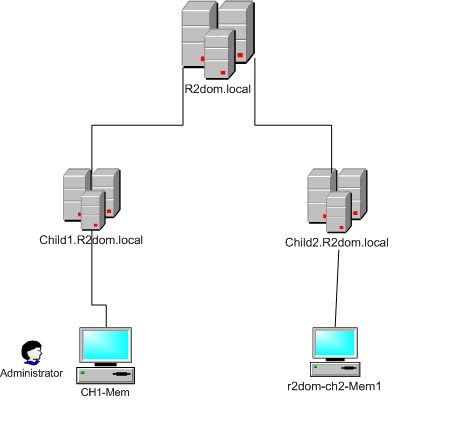
Both Child1 and Child2 are in the same forest with the same parent domain R2dom.local.
Administrator of the Child domain (CHILD1) login to a member server (CH1-Mem) in CHILD1 domain.
After login in the user tries to access \\r2dom-ch2-Mem1 . R2dom-ch2-Mem1 is a member server in Child2 domain.
--> I have used Network monitor to analyze and understand how Kerberos authentication would work, when accessing resource across domain.
Below you see that the Administrator is getting the required Kerberos tickets when accessing resources across domain.
10.2.1.2 = DC of CHILD1.R2DOM.LOCAL
10.1.1.2 = DC of R2DOM.LOCAL
10.3.1.1 = Dc of CHILD2.R2DOM.LOCAL
10.10.10.1 = CH1-Mem in CHILD1
10.10.10.1 10.2.1.2 KerberosV5:TGS Request Realm: CHILD1.R2DOM.LOCAL Sname : cifs/r2dom-ch2-Mem1
--> KrbApReq : KRB_AP_REQ (14)
Ticket: Realm: CHILD1.R2DOM.LOCAL, Sname: krbtgt/CHILD1.R2DOM.LOCAL
** Here you see a Kerberos TGS request being sent to the local domain (CHILD1.R2DOM.LOCAL) DCs for a SPN cifs/r2dom-ch2-Mem1. Local domain TGT sent in the TGS request.
10.2.1.2 10.10.10.1 KerberosV5:TGS Response Cname: Administrator
--> Ticket: Realm: CHILD1.R2DOM.LOCAL, Sname:krbtgt/R2DOM.LOCAL
** Here the local domain DC returns a TGT of the Parent domain R2DOM.LOCAL. This is like a referral being sent to the client as the local domain does not have the right to issue a Kerberos Ticket for cifs/r2dom-ch2-Mem1.
10.10.10.1 10.1.1.2 KerberosV5:TGS Request Realm: R2DOM.LOCAL Sname: krbtgt/CHILD2.R2DOM.LOCAL
--> KrbApReq : KRB_AP_REQ (14)
Ticket: Realm: CHILD1.R2DOM.LOCAL, Sname : krbtgt/R2DOM.LOCAL
** Now the client machine send a TGS request to the Parent domain R2DOM.LOCAL, requesting for a TGT of another of its Child domain where the cifs/r2dom-ch2-Mem1 resides. When sending this request to the parent domain, the client uses the TGT of the Parent domain received in the earlier referral from local DC.
10.1.1.2 10.10.10.1 KerberosV5:TGS Response Cname: Administrator
--> Ticket: Realm: R2DOM.LOCAL, Sname: krbtgt/CHILD2.R2DOM.LOCAL
**Parent domain sends the TGT of the child2 domain to the client. This can also be taken as a referral to the CHILD2 domain.
10.10.10.1 10.3.1.1 KerberosV5 :TGS Request Realm: CHILD2.R2DOM.LOCAL Sname : cifs/r2dom-ch2-Mem1
-->KrbApReq: KRB_AP_REQ (14)
Ticket: Realm: R2DOM.LOCAL, Sname: krbtgt/CHILD2.R2DOM.LOCAL
** Eventually the Child sends a TGS request for the SPN cifs/r2dom-ch2-Mem1 to the DCs in domain CHILD2.R2DOM.LOCAL who is authorized to issue a ticket for the server (r2dom-ch2-Mem1) in its domain. This time the client uses the CHILD2 domains TGT to make request.
10.3.1.1 10.10.10.1 KerberosV5:TGS Response Cname: Administrator
--> Ticket: Realm: CHILD2.R2DOM.LOCAL, Sname: cifs/r2dom-ch2-Mem1
** Finally the client gets the Kerberos Ticket for cifs/r2dom-ch2-Mem1, which will help the Administrator user access the shares on r2dom-ch2-Mem1 in domain CHILD2.R2DOM.LOCAL.
The workstation the user 'Administrator" is using to access the resource across domain, also needs a similar ticket.
Tickets for r2dom-ch2-Mem1 is requested from local domain, who returns the error KDC_ERR_S_PRINCIPAL_UNKNOWN, as the r2dom-ch2-Mem1 computer is not a part of the local domain (CHILD1.R2DOM.LOCAL)
10.10.10.1 10.2.1.2 KerberosV5 KerberosV5:TGS Request Realm: CHILD1.R2DOM.LOCAL Sname: r2dom-ch2-Mem1
10.2.1.2 10.10.10.1 KerberosV5 KerberosV5:KRB_ERROR - KDC_ERR_S_PRINCIPAL_UNKNOWN (7)
Below you see that the client computer is getting the required Kerberos tickets when accessing resources across domain.
10.10.10.1 10.2.1.2 KerberosV5 KerberosV5:TGS Request Realm: CHILD1.R2DOM.LOCAL Sname: cifs/r2dom-ch2-Mem1
10.2.1.2 10.10.10.1 KerberosV5 KerberosV5:TGS Response Cname: CH1-Mem$
10.10.10.1 10.1.1.2 KerberosV5 KerberosV5:TGS Request Realm: R2DOM.LOCAL Sname: krbtgt/CHILD2.R2DOM.LOCAL
10.1.1.2 10.10.10.1 KerberosV5 KerberosV5:TGS Response Cname: CH1-Mem$
10.10.10.1 10.3.1.1 KerberosV5 KerberosV5:TGS Request Realm: CHILD2.R2DOM.LOCAL Sname: cifs/r2dom-ch2-Mem1
10.3.1.1 10.10.10.1 KerberosV5 KerberosV5:TGS Response Cname: CH1-Mem$
- Abizer