Azure Black IPs Intro
What is the Azure Black IPs Nuget Package.
In a previous post on our blog (https://blogs.msdn.com/b/friis/archive/2014/04/25/easily-detect-and-block-malicious-http-requests-targeting-iis-asp-net-using-blackips.aspx) we have discussed how we could go about detecting and blocking malicious input to an ASP.net website. We have taken this concept a step further with the v2.0 of the tool that is now available on Nuget.
This module was created to address a specific problem that you can encounter when running ASP.net applications in production on the Internet. The problem stems from the fact that the Internet is not always a nice and order abiding place – there are certain users and bots that will try to force your site and inject code into the input fields to see if the application can be made vulnerable to code / javascript or SQL injection.
To this effect, they will send requests to your application where they send input values like the following:
<script>
window.alert("Your site has been hacked");
</script>
This code is harmless enough, but it will trigger the request validation mechanisms built into ASP.net, and will make the Runtime raise an error. Error processing in an ASP.net application can be costly, especially if there is a high number of errors to treat in a short period of time. Hence the importance to know when such errors occur and from which IP addresses they are coming from.
Most of the time, the IP of the computers that are sending such junk requests to your site will be repetitive, and the objective for you should be to be able to locate them quickly and easily to be able to then restrict traffic to your server from those IP addresses – at least on a temporary basis.
To this end, Azure Black IPs will allow you to trap all such errors raised by your application and display them on a control panel page. You can then inspect the page even from a distance, without having to connect to your server via remote desktop (or something similar) and go through the event logs – which can be quite lengthy and time consuming.
What do you get when you install Azure Black IPs.
The Nuget package will add two .Net binaries (dlls) to your application: AzureBlackIP.dll and AzureErrorDisplay. These will contain an HttpModule that will listen for a specific type of error caused by such malicious / erroneous requests, and an HttpHandler that will display the control panel page.
A couple of configuration entries will be added to the site's web.config configuration file allowing you to configure the tracing. These entries are in the <system.web> and <system.webServer> tags of the configuration file:
<add verb="GET, POST" path="DisplayIP.err" type="Azure.BlackIPs.Handlers, ErrorDisplayHandler" />
<add name="Error Display Handler" path="DisplayIP.err" verb="*" type="Azure.BlackIPs.Handlers.ErrDisplayHandler" resourceType="Unspecified" preCondition="integratedMode" />
These two entries allow you to configure the url of the control panel page. By default, this is /Display.err at the root of your website.
The other value is:
<add key="blackIpLogging" value="true" />
This controls the tracing – enabling it if the value is set to true, and disabling it if set to false.
Using Azure Black IPs:
You can download the Nuget package from Nuget.org and install it into your application (WebForms or MVC or WebPages). Alternately, you can run the following PowerShell command from the Package manager console inside Visual Studio:
Install-Package Azure-BlackIP
Once you deploy your application, assuming that you are running with the default settings, you can just type in the following address:
<yourappsurl.com>/Display.err
to display the control panel page. This will list all the recent errors (since the application started) that were encountered.
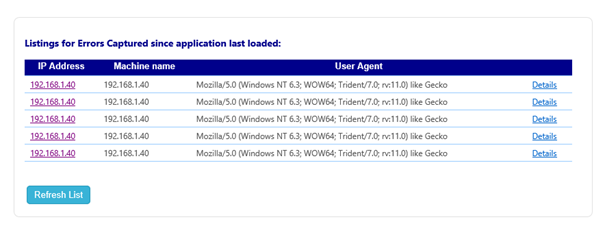
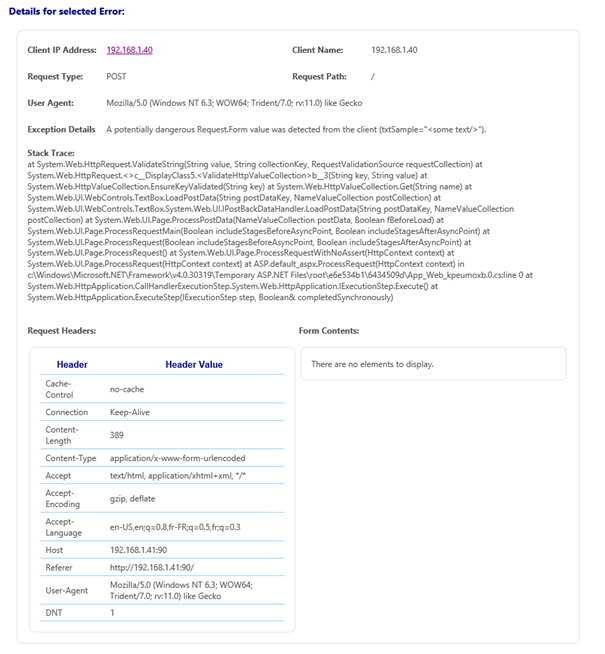
Clicking on one of the errors will display more details, like the stack trace, the user agent of the connecting client, the request headers, and most importantly the IP address of the machine that initiated the request.
Requirements:
The module requires that you are running ASP.net 4.5 or above for the application to work correctly.