Installing a Two Tier PKI Hierarchy in Windows Server 2012: Part V, Installing an Enterprise Subordinate Certification Authority and Web Enrollment with PowerShell
In the previous blog postings for this series I covered installing the Root Certification Authority, configuring the Root Certification Authority, and publishing the Root CA Certificate and CRL to Active Directory. In this installment I am going to cover installing an Enterprise Subordinate CA with PowerShell.
In this example I am going to install a Certification Authority with the following base configuration:
CA Type: Enterprise Subordinate CA
Common Name: FourthCoffee Issuing Certification Authority 01
Key Storage Provider: RSA#Microsoft Software Key Storage Provider
Public Key Algorithm: RSA
Hashing Algorithm: SHA1
Key Length: 2048
Validity Period: 10 years
Additional Role Services: Web Enrollment
I will be installing the ADCS Role with PowerShell. Additional documentation for these steps can found https://technet.microsoft.com/en-us/library/hh848390 and https://technet.microsoft.com/en-us/library/hh848389.
Configuring CAPolicy.inf
The CAPolicy.inf is an optional file that is read during the installation of Certificate Services. Typically for an Enterprise CA, the LoadDefaultTemplate=0 option is used to suppress the loading of the default Certificate Templates. This allows the CA to be installed with no certificate templates available, and in that way the administrator can later add just the certificate templates that are needed.
I will copy the following text to a text file named CAPolicy.inf, and then copy that file to the C:\Windows directory:
[Version]
Signature= "$Windows NT$"
[Certsrv_Server]
LoadDefaultTemplates=0
Launching PowerShell
The first step of course is to launch PowerShell. This can be accomplished by starting a command prompt and typing powershell and pressing the Enter key or by clicking on the PowerShell icon on the taskbar.
Import Server Manager Module
The first step is to import the Server Manager Module for PowerShell which will then allow you to add the ADCS feature. To import the Server Manager Module for Powershell type: Import-Module ServerManager and press Enter .
Installing ADCS Binaries
The next step is to install the ADCS binaries so that we can install ADCS. To install the ADCS binaries type: Add-WindowsFeature Adcs-Cert-Authority and press Enter.
Installing ADCS Web Enrollment Binaries
Since, I will be installing the Web Enrollment Role Services, I need to load the binaries for ADCS Web Enrollment as well. To install the ADCS Web Enrollment binaries type: Add-WindowsFeature Adcs-Web-Enrollment
Install Certification Authority Role
To install the Certification Authority Role you will need to use the Install-AdcsCertificationAuthority cmdlets. The options for the Install-AdcsCertificationAuthority cmdlets is available here: https://technet.microsoft.com/en-us/library/hh848390.aspx.
Below is the entire command that I will be using to install Active Directory Certificate Services in my environment:
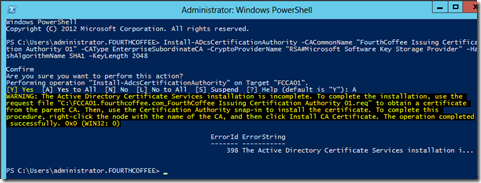
Install-ADcsCertificationAuthority -CACommonName "FourthCoffee Issuing Certification Authority 01" -CAType EnterpriseSubordinateCA -CryptoProviderName "RSA#Microsoft Software Key Storage Provider" -HashAlgorithmName SHA1 -KeyLength 2048
I am using the CACommonName option to specify a Common Name of “FourthCoffee Issuing Certification Authority 01”. Then I am specifying the CAType option to set the CA Type to a Enterprise Subordinate CA. Next I am selecting my Key Storage Provider of “RSA#Microsoft Software Key Storage Provider” with the CryptoProviderName option. I have decided to use SHA1 as the hashing algorithm and therefore am using SHA1 with the HashAlgorithmName option. Then I am setting the RSA Key Length to 2048-bit with the KeyLength option.
After you run the Install-AdcsCertificationAuthority cmdlet you will be prompted to accept the changes as seen in the screenshot below:
Also, you will notice a Warning and Error ID of 398. This is just informing me that installation of the CA is incomplete. Installation is incomplete because I have to have to submit the request to the Root CA, receive the resulting certificate, and load the certificate on the Issuing (Subordinate) CA.
Installing the Certification Authority Management Tools
To Install the Certification Authority Management Tools type the following command in PowerShell and hit enter: Install-WindowsFeature RSAT-ADCS-Mgmt.
Submitting the Request
Next you will need to submit the request to the Root CA. So, first copy the request file from the C:\ directory on the Issuing CA to a file location on the Root CA.
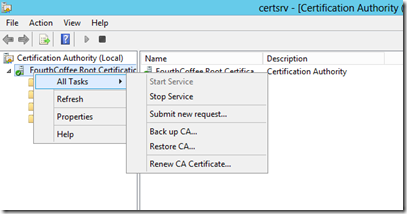
On the Root CA, start the Certification Authority MMC (Certsrv.msc). Right click on the CA Name node, select All Tasks, then Submit new request…
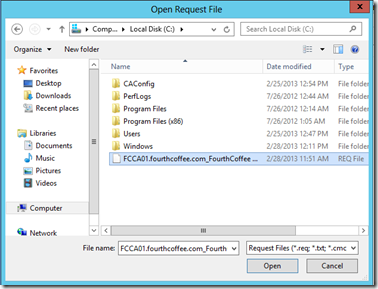
Next, select the Request File that you copied from the Subordinate CA and click Open
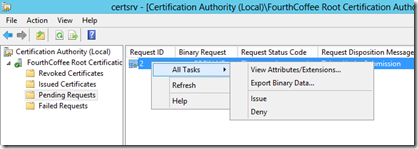
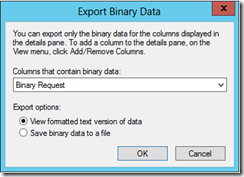
If you would like to review the request before approving the request, go to the Pending Requests container. Then right-click on the request, select View Attributes/Extensions…
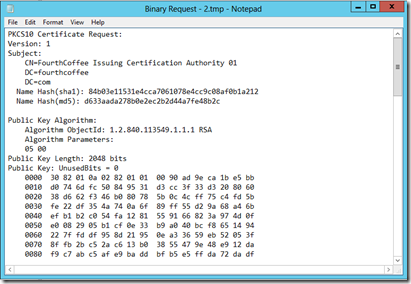
You will then be prompted for the type of binary data, select Binary Request, make sure View formatted text version of data is selected, and click OK
You can then review the request file.
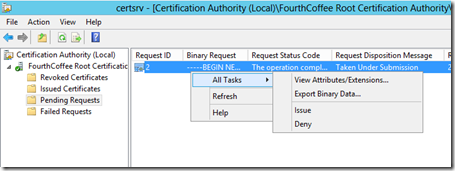
To approve the request, right-click on the request, select All Tasks, then Issue
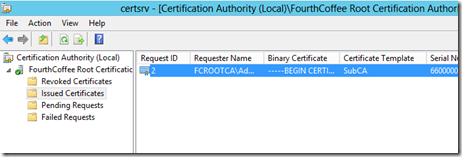
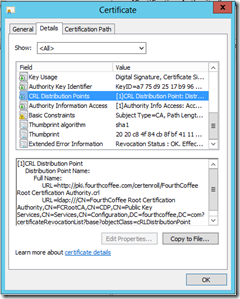
You can then review the resulting certificate, by going to the Issued Certificates view, and double-clicking on the certificate
You can then review the certificate to ensure it is configured as desired. I usually at least spot check the CRL Distribution Points and Authority Information Access extensions.
You then need to copy the certificate to a file. So, on the Details tab, click on Copy to File… This will open the Certificate Export Wizard. On the Export File Format page of the wizard, you can select any format, I chose P7B. After selecting the file format, click Next. Now, on the File to Export page of the wizard you will need to click Browse…, select a location, typed the desired name of the file (I chose “CACert”), and then click the Save button. To complete the File to Export task, click on the Next button. Finally, click the Finish button on the Completing the Certificate Export Wizard page of the wizard, click OK when prompted that The export was successful.
Completing Installation of Certificate Services
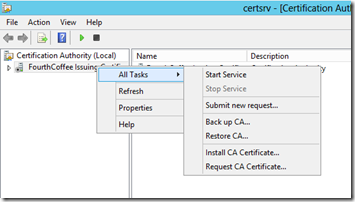
First copy the Certificate that was issued from the Root CA to the Subordinate CA. To complete the installation of Certificate Services, open the Certification Authority MMC (certsrv.msc). Then right-click on the CA Name, select All Tasks, and then Start Service.
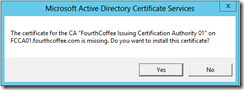
You will then be prompted to install the certificate, select Yes.
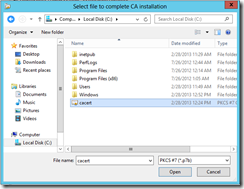
Browse to the certificate file
The CA Service will no start.
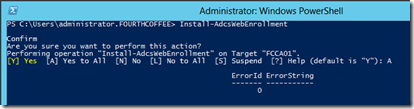
Installing Web Enrollment
To install Web Enrollment, run the following powershell command: Install-AdcsWebEnrollment. An error ID of 0 indicates that the Role Service was installed successfully.
Conclusion
During this blog posting, I installed my Subordinate CA and installed Web Enrollment. I have not configured the Subordinate CA. So, stay tuned, in an upcoming blog posting, I will cover the steps necessary to configure the Subordinate CA.