Sending Protected Attachments to Social Identities
The Scenario:
So you have started using the fancy new Encrypt functionality to send protected emails to users on Outlook.com, Gmail, Yahoo, and other social identity providers and you start getting some complaints. It seems that users on older versions of Office (not Office 365 monthly channel) are having problems opening attachments that were sent with protected emails. So, we can just ask them to update to the latest version of Office 365 ProPlus and get on the monthly update channel, right?? Yeah...we would have a bad time if we went that route. Luckily, the Office team heard these cries and came to the rescue.
The Solution:
In a recent technical blog post, the Office team introduced a new feature for decrypting attachments on download for users that are not on Office 365. This awesome new feature helps to reduce the friction for social identity recipients of emails with attachments. In this post, I am going to shamelessly plagiarize elaborate on the steps to accomplish this task. It is not hard, but having the steps laid out on a single page does have it's merits. :-)
First, we have to connect to Exchange Online PowerShell. For those that have a dedicated prompt for this, feel free to skip these steps and go straight to the Set-IRMConfiguration command below.
- Click on the start menu and type PowerShell, then right-click on Windows PowerShell and select Run as administrator
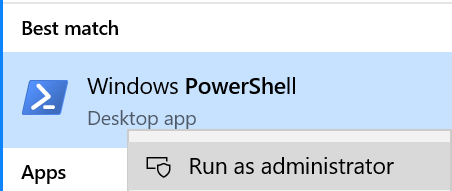
- In the admin PowerShell window run the command Set-ExecutionPolicy RemoteSigned and type y and enter if prompted.
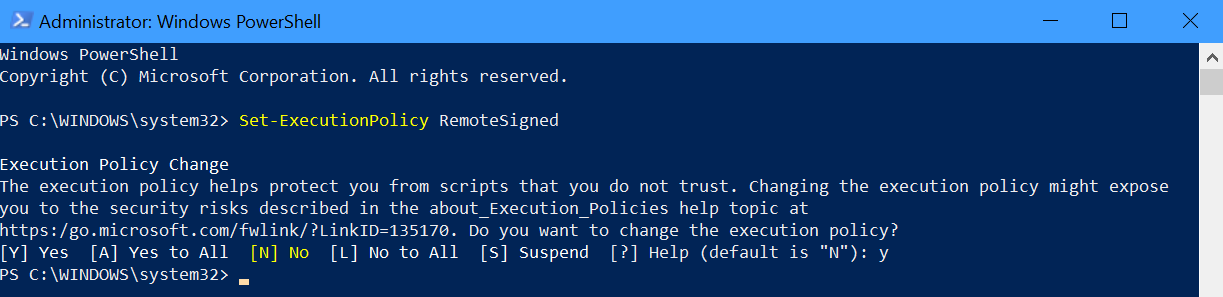
- Next, type $UserCredential = Get-Credential and provide the username of your exchange or global admin
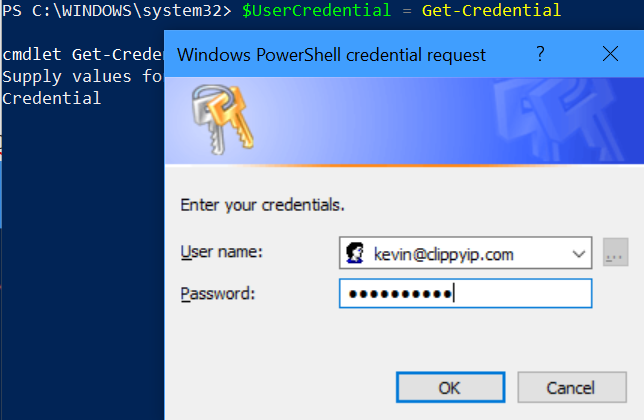
- Next, run $Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $UserCredential -Authentication Basic -AllowRedirection to create the session. If you have any errors, you may have one of the more picky tenants (Germany, 21Vianet, Proxy configurations) then you should see https://aka.ms/EXOPowerShell for additional details.
- Finally, run Import-PSSession $Session -DisableNameChecking to complete the connection to EXO PowerShell.
- Now that you are connected, you can run Set-IRMConfiguration -DecryptAttachmentFromPortal $true to enable the feature I described earlier.
That's all it takes. Now, when a recipient that is not an Office 365 user get a protected email with an attachment, that attachment will be decrypted upon download of the document. They will still be able to preview it in the OME interface, but when it is downloaded the protection will be removed so they can open it without an issue in any supported version of office. Now, if the user IS an Office 365 user, the attachment will maintain it's encrypted status upon download.
Removing the encryption of an attachment may seem at first glance like a bad idea, but keep in mind that through the email wrapper, the attachment is fully encrypted from sender to recipient and the user must authenticate before they will ever see the attachment. This is a similar experience to third party systems, but for Office 365 users you get the added value of having supported attachments be encrypted as well.
Thanks,
Kevin
More fun content at https://aka.ms/Kevin