7 Steps to Building Site-to-Site VPN Connections for V2 VNETs using Azure Resource Manager in the NEW Azure Portal
In a prior article, we walked through the process of scripted provisioning for V2 virtual networks and site-to-site connections using Azure Resource Manager (ARM) and Azure PowerShell together. Recently, a UI create experience was surfaced in the NEW Azure Portal to make it even easier to provision these scenarios directly from the portal.
In this article, we’ll step through building Site-to-Site VPN connections for V2 virtual networks using the NEW Azure Portal.
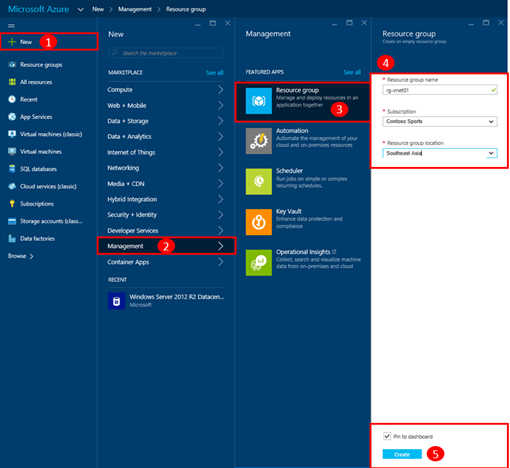
Step 1: Create or Select a Resource Group
When configuring a Site-to-Site VPN connection, you’ll be creating several Azure resources, including Virtual Network, GatewaySubnet, Virtual Network Gateway, Local Network Gateway and Connection resources. To make it easiest to manage these resources as a collection, create or select a Resource Group in which to organize these resources.
You can create a new Resource Group using the New button as shown below …
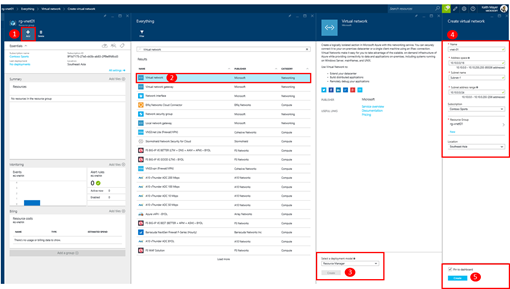
Step 2: Create or Select a Virtual Network
A Site-to-Site VPN connection is associated with routing to/from an Azure Virtual Network. Prior to setting up the Site-to-Site connection, we’ll need a Virtual Network first.
You can add a Virtual Network to your Resource Group by using the Add button as shown below …
When defining the configuration for your Virtual Network in box #4 in the screenshot above, be sure to specify an IP address space for your Virtual Network that does not overlap with any IP networks that you'll be connecting via a Site-to-Site connection.
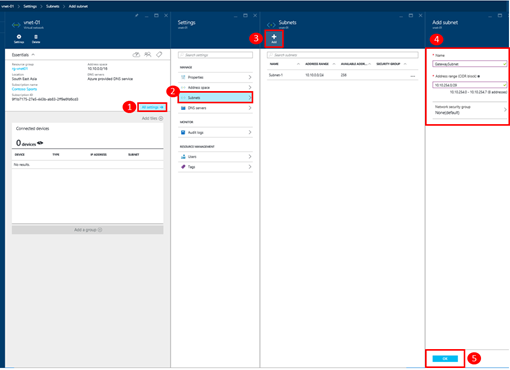
Step 3: Add a GatewaySubnet to the Virtual Network
On the selected Virtual Network, a special subnet must be added to which the Azure Virtual Network Gateway will be deployed. This subnet must be named GatewaySubnet. The defined IP address range for this subnet must be a /29 or larger CIDR block.
You can add this subnet on the All Settings blade of the selected Virtual Network as shown below …
When defining the GatewaySubnet in box #4 in the screenshot above, be sure to leave the Network security group field at its default setting of None(default) . The Azure Virtual Network Gateway that will be provisioned on this subnet is already preconfigured in a security-hardened state, and as such, a custom Network Security Group is not necessary.
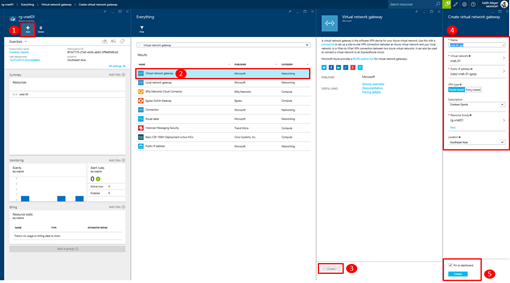
Step 4: Create a Virtual Network Gateway
The Azure Virtual Network Gateway is a virtual appliance that can be provisioned on your Virtual Network to establish a secure Site-to-Site tunnel to your Virtual Network for routing network traffic from an on-premises location.
You can add a Virtual Network Gateway to your Resource Group by using the Add button on the Resource Group blade as shown below …
When defining the configuration for your Virtual Network Gateway in box #4 in the screenshot above, be sure to specify the appropriate type of Virtual Network Gateway that is required for your connection: Route-based (aka. Dynamic Gateway) or Policy-based (aka. Static Gateway). You can determine the appropriate type of Gateway required for connecting to a variety of on-premises VPN Gateway devices on the Azure VPN Gateway Compatibility List.
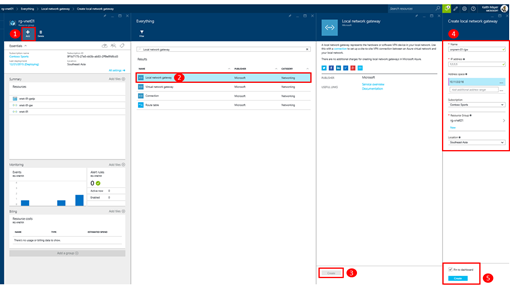
Step 5: Create a Local Network Gateway
The Local Network Gateway is used to define the Public IP Address on your on-premises VPN Gateway device and the local IP network address spaces that are permitted to route to/from the Azure Virtual Network over a Site-to-Site connection.
You can add a Virtual Network Gateway to your Resource Group by using the Add button on the Resource Group blade as shown below …
When defining the configuring for your Local Network Gateway in box #4 in the screenshot above, be sure to specify the Public IP Address of your on-premises VPN Gateway device in the IP Address field, and also specify your on-premises IP networks in the Address Spaces list.
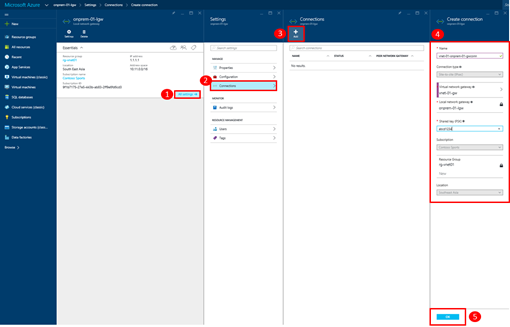
Step 6: Define a Site-to-Site Connection
After the Virtual Networks and Gateways have finished provisioning in the prior steps, you’re ready to define a Site-to-Site Connection that defines the tunnel parameters between your Virtual Network Gateway and on-premises Local Network Gateway.
You can add a Site-to-Site Connection by using the All Settings blade for the Local Network Gateway as shown below …
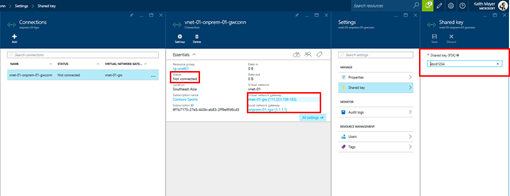
After the Site-to-Site Connection has completed the initial provisioning process, the properties of this Connection should show a status of Not Connected.
In addition, you should also see the IP Address information for the Virtual Network Gateway, Local Network Gateway and Shared Key. Be sure to note these values, because they’ll be needed when configuring your on-premises VPN Gateway device in the next step.
Step 7: Configure the On-Premises VPN Gateway Device
After you’ve completed provisioning of the above resources in your Azure Resource Group, the final step involves configuring your on-premises VPN Gateway device with the necessary configuration to reflect this new Site-to-Site tunnel connection.
Several VPN device manufacturers have included sample setup scripts on the Azure VPN Devices page to help accelerate the process of finishing this configuration work.
If your VPN device manufacturer has not yet supplied a setup script for Azure, please confirm the configuration with your VPN device manufacturer. Configuration requirements for on-premises VPN Gateway devices are noted at Azure VPN IPsec Parameters.