Authentication: Enabling Modern Auth (OAuth2)
How many times you wanted to have Outlook seamless authentication on domain joined computers while connecting to Office 365 like it would do with on premise Exchange? I don't know about you, but I always liked Outlook profile creation without prompting user for entering credentials. This is great feature while Exchange is on-premise since it using either Kerb or NTLM. With moving user mailbox to Office 365, basic authentication for Outlook was only way for authenticating user. Users needed to enter their username / password combination and click "Save credentials" and everything was fine until user was changed password and prompt would pop up again.
With introduction Modern Authentication for Office suite and Exchange 2016, Outlook seamless authentication experience is possible with Office 365 as well.
Note // This is only tested with Exchange Hybrid environment.
This post will be divided in three parts:
1. Enable modern authentication on Outlook client,
2. Set up intranet sites for STS,
3. Enable Oauth profiles feature in Office 365.
Enable modern authentication on Outlook client
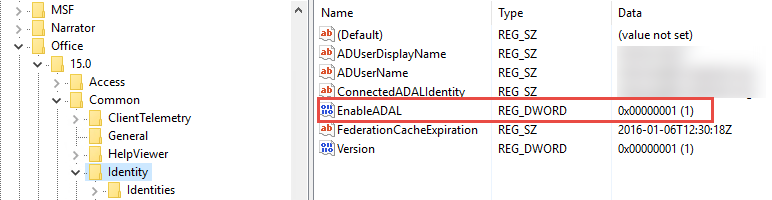
Modern authentication (ADAL) in Outlook 2016 is enabled by default and it will be first mechanism that Outlook will try to use against Office 365. On the other hand, Outlook 2013 has it turned off by default and registry key should be used for enabling it .
Navigate to HKCU:\Software\Microsoft\Office\15.0\Common\Identity and create new dword value "EnableADAL" and set it to value "1":
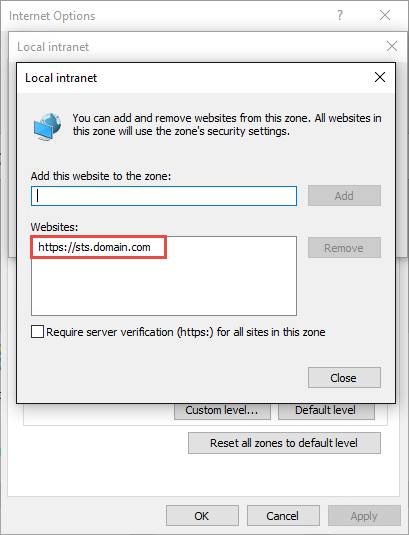
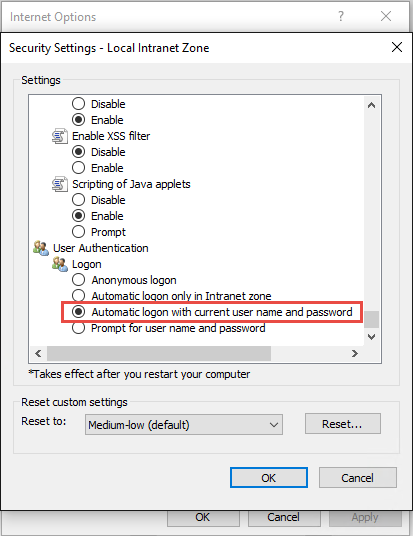
Set up intranet sites for STS
In order to get seamless experience while authenticating to STS, STS should be placed in "Local Intranet" zone and that zone should have option "Automatically login with current username and password" option set:
Enable Oauth profiles feature in Office 365
Final step in this process is to enable OAuth2 Client Profile. Open PowerShell session to Office365 tenant and execute following command:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
After that wait few minutes and you are all set.
Create new Outlook profile (or wait until profile is automatically switch over to OAuth2) for user that have mailbox hosted in Office 365:
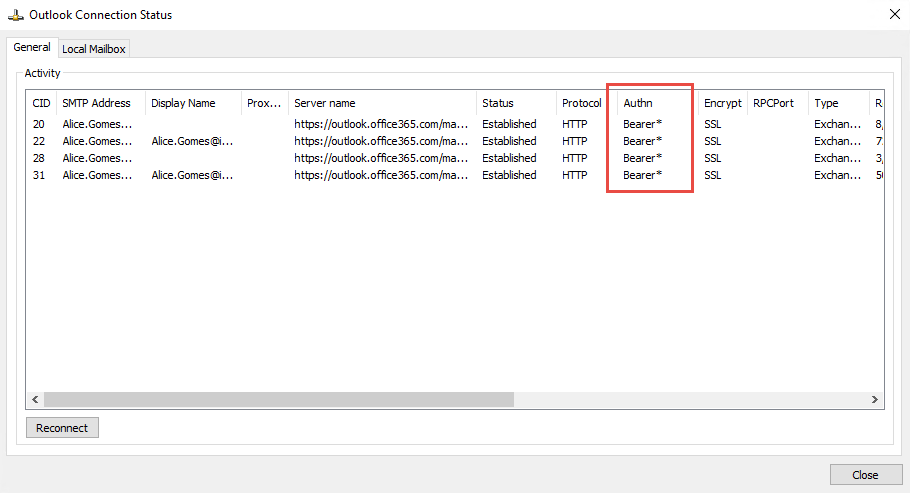
You can check in connection status that Outlook is consuming "Bearer" (fancy name for Oauth) authentication:
How it works? Lets go fiddling...
I won't cover each step Outlook performs while connecting to service (you should know it already!?), just one's that matters. Fire up Fiddler!
1. Client make HTTP POST to https://autodiscover-s.outlook.com/autodiscover/autodiscover.xml
POST https://autodiscover-s.outlook.com/autodiscover/autodiscover.xml HTTP/1.1
Cache-Control: no-cache
Connection: Keep-Alive
Pragma: no-cache
Content-Type: text/xml
Authorization: Bearer
Cookie: OutlookSession="{1CF266D3-11FB-47D7-B0CD-CA3999D8D62D}"
User-Agent: Microsoft Office/16.0 (Windows NT 10.0; MAPI 16.0.4266; Pro)
X-MS-CookieUri-Requested: t
X-FeatureVersion: 1
Client-Request-Id: {57328DA9-DBD7-4D83-80F7-38778E9B8EB3}
X-MapiHttpCapability: 1
Depth: 0
X-AnchorMailbox: AGomes@itor.mail.onmicrosoft.com
X-User-Identity: Alice.Gomes@domain.com
Content-Length: 365
Host: autodiscover-s.outlook.com
AGomes@itor.mail.onmicrosoft.comhttp://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a
Response: 401 Unauthorized with authorization link https://login.windows.net/common/oauth2/authorize
HTTP/1.1 401 Unauthorized
Cache-Control: private
Content-Type: text/html
Server: Microsoft-IIS/8.0
request-id: 41e440d8-c358-4bbe-9a94-664cfee0fc26
X-CalculatedBETarget: vi1pr08mb0832.eurprd08.prod.outlook.com
X-DiagInfo: VI1PR08MB0832
X-BEServer: VI1PR08MB0832
X-AspNet-Version: 4.0.30319
Set-Cookie: X-BackEndCookie2=AGomes@itor.mail.onmicrosoft.com=u56Lnp2ejJqBzcybyp2dxs3SzczMm9LLx8vK0p7NmZnSz8idz5ybzsrLxsqbgZaLkI3Rkp6Wk9GQkZKWnI2QjJCZi9GckJKBzc/OydLPzdLNyKvOyMXMysXPyYGaio2PjZvPx9GPjZCb0ZCKi5OQkJTRnJCSgc8=; expires=Sat, 27-Feb-2016 17:35:06 GMT; path=/autodiscover; secure; HttpOnly
Set-Cookie: X-BackEndCookie=AGomes@itor.mail.onmicrosoft.com=u56Lnp2ejJqBzcybyp2dxs3SzczMm9LLx8vK0p7NmZnSz8idz5ybzsrLxsqbgZaLkI3Rkp6Wk9GQkZKWnI2QjJCZi9GckJKBzc/OydLPzdLNyKvOyMXMysXPyYGaio2PjZvPx9GPjZCb0ZCKi5OQkJTRnJCSgc8=; expires=Sat, 27-Feb-2016 17:35:06 GMT; path=/autodiscover; secure; HttpOnly
X-Powered-By: ASP.NET
X-FEServer: AM4PR01CA0024
WWW-Authenticate: Bearer client_id="00000002-0000-0ff1-ce00-000000000000", trusted_issuers="00000001-0000-0000-c000-000000000000@*", token_types="app_asserted_user_v1 service_asserted_app_v1", authorization_uri="https://login.windows.net/common/oauth2/authorize",Basic Realm="",Basic Realm=""
Date: Thu, 28 Jan 2016 17:35:06 GMT
Content-Length: 58
You do not have permission to view this directory or page.
2. Client submits HTTP GET against login.microsoft.com and request contains user email address:
Request:
GET https://login.microsoftonline.com/common/oauth2/authorize?response_type=code&client_id=d3590ed6-52b3-4102-aeff-aad2292ab01c&redirect_uri=urn%3aietf%3awg%3aoauth%3a2.0%3aoob&resource=https%3a%2f%2fautodiscover-s.outlook.com%2f&nux=1&login_hint=AGomes%40domain.com HTTP/1.1
Accept: */*
client-request-id: 75FE0558-9C26-46D5-AED6-E831CC28E4F8
return-client-request-id: false
x-client-BSSO: on
x-ms-PKeyAuth: 1.0
x-client-SKU: Win32
x-client-Ver: v1.0.2016.0
x-client-OS: 10.0.10586
Accept-Language: hr-HR
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; Trident/7.0; .NET4.0C; .NET4.0E)
Host: login.microsoftonline.com
Connection: Keep-Alive
Response (redirect to OnPrem STS):
HTTP/1.1 200 OK
Cache-Control: no-cache, no-store
Pragma: no-cache
Content-Type: text/html; charset=utf-8
Expires: -1
Vary: Accept-Encoding
Server: Microsoft-IIS/8.5
x-ms-request-id: c3a5cbf0-2a91-48bd-aa16-8f3da5ddc34a
client-request-id: 75fe0558-9c26-46d5-aed6-e831cc28e4f8
x-ms-gateway-service-instanceid: ESTSFE_IN_152
X-Content-Type-Options: nosniff
Strict-Transport-Security: max-age=31536000; includeSubDomains
P3P: CP="DSP CUR OTPi IND OTRi ONL FIN"
Set-Cookie: flight-uxoptin=true; path=/; secure; HttpOnly
Set-Cookie: x-ms-gateway-slice=productionb; path=/; secure; HttpOnly
Set-Cookie: stsservicecookie=ests; path=/; secure; HttpOnly
X-Powered-By: ASP.NET
Date: Thu, 28 Jan 2016 17:35:08 GMT
Content-Length: 5503
setTimeout(function () { window.location.replace('https://sts.domain.com:443/adfs/ls/?login_hint=AGomes%40domain.com\u0026username=AGomes%40domain.com\u0026wa=wsignin1.0\u0026wtrealm=urn%3afederation%3aMicrosoftOnline\u0026wctx=estsredirect%3d2%26estsrequest%3drQIIAXWPP0vDQByGuaQK1qHiIDhbRIS73J-kMTfZRUdX18vlkgZNfpJcKvgxOvsJOnRwkn4GhyyKOIpDP0InMXUVl-eFB94X3v7ulBFKOGUjQk9dRpgcJiKIqElGOOCxwD6jHCuTpliphPOIq5gyXe339663vpvjx9eLxduKvZx8refosKlKmRubyvtMgmrsRHJCJUD8jFCL0AqhmXMwvoTC1Oe5xabM8tKYikCVtQ76cAZX467EN4AqfzCff8zMHfwOc7KhhsTM3aOJtXe19LxOQZLXGqamwjWBxt4C3BANhffkbndRQLl0hzGlZzTWPk5EqLGvUoEjxRj2Q6G50iII_ejdRW0PrXtoufP_qx81'); }, 0);
3. STS authenticate client and return it back to login.microsoft.com:
HTTP/1.1 200 OK
Cache-Control: no-cache,no-store
Pragma: no-cache
Content-Length: 6244
Content-Type: text/html; charset=utf-8
Expires: -1
Server: Microsoft-HTTPAPI/2.0
X-XSS-Protection: 0
Set-Cookie: MSISAuth=AAEAACaKnyhiKMDsU02wKcnNYfD7tWo1KRGJ/fD7i4WRP18D+TF1YT5vIn7pkaqDR5ehab8dRaFQXCwo5/A6PWthIczezmUYedt7p0367VF7tMercBr3fJlN36lMUcuDRSCdxeFdXRvwLJCfg2zlfg+TRZ6LAfW0s4zEGToviA79Mm0FfLi7AKCcY0nKwKDYh2FCcywEThmcX1910GzPSb4Pof3wscCDEV5D4EjR/oN4qKGylX0mBKz8DQY/nPQqwyt4HqPY6mKvh9prY70gZHkz42bY4h3UKtxpQXfKiFYMU/3lnv06CMr9PvXKqRwZj+EFe4/L0Men3LPvF6/sl8zO0n2Klxvk4THVNMzJR6xO67E5sir2ljdWjrjDgkb6VZ/YmgABAAAu/gCwAMgev4k2w/CmwaBO6vLb/RgrZvrDMWfmoVd7WMdyFJqczkhg4iSAFCzDMTLvwfdqeuHlUObcPby1RHOHVDaksSEAiPQMZwWe8cs0qZwRvwr283X4qsXofArV09L26HdHTE72jgu+zNA57mgU9VXxFKyg1V+PkK31qGgRKupqtaXVT3OlKyZCwBMKAFDa9jOSMFUn8nzFyEnZVRXI/V6SE36V0ienkFaVjzdj5VYZlqls7cYAFo/1AJYh6m9Z9jQu1FzCGeeb5I9zgshR+QbcqxpkG+5h1ZysUqZzz+3BlzBiku5fZfEHIDeqmadGfdZEuzZsquwv0Vyq5KeukAIAACEFAAJ3Fz4gsVzt4MV5Z16vGPD0Dfizus1wJ/f0QGMfvHTL65imWk15I8VjyfmnrBM07y+ndm1GT2IXOX7htJbRShmdfN3ep9BocEisluqTuIBD5j0JgAqGPtlNeaX9vzjVjcaIq8aOhxGCb7XdTR5HsccQOcBo9VrWpspShxGsI1wj/AhxcrYckOdz9grDz3fXUGnsCdx8kXk2eCKP88Ol8JrprDGt2Fbrtp371uC4Y/gVOInIjiDQDHy2WUGMtkomHQ054WbIF2qevoARdb8oEFRA4cZIazgNz0pTd6zESGxsdVsk2lsVmuLI6qWbAyef5vKfkheo+M64UtKXQbh1RaiAqmuxN8drxQhPgs85mFopM2pg14v5/gcJhkKBqS3JscUOOAwejj5AbevVw8xVQpHpBh6XY448C/CBpJFKdo/LEcp+o8pf9ku3pAoELya9gnESBhZVSnsLPrmrUIGjULRvaR73UhP/Yjp6VI6xU4AIbfEo0avGhEU2H+ABPIm4nBpxQMlB9wZXadgPI/L0mckljPxQAnde3Bx7mZ1ypukFPbUd6TE32TBuq5PuXkpIAhoaAAY2P04vVuN56NqJpZzb1/Fvw4ZlVplswqwurcTAXkk7nwX36DWZhCmbmu/5nWETJ2ZlGQJVl/i9EsR7jRzfDxjRRGX6gerJ6zqXLBjfTRRE1izw0Xk7FroPAOrW29tbCjecSW54SjUiMbHfwSfMB+nUXoMGYJDPgFQXKwHVmOjzlYkVkzbOf/Q7HRyZSbkCADqkR7WHv2Kew4WVXYsPzMb4sF4OCsszrumdHqpWXQvmjwiv8AHMI8KcPbLkBrUQOlK/PUDHXpi1OhTg99Yjk33GcCJYA9BSAi0f; path=/adfs; HttpOnly; Secure
Set-Cookie: MSISSignOut=c2lnbm91dENsZWFudXA7dXJuJTNhZmVkZXJhdGlvbiUzYU1pY3Jvc29mdE9ubGluZSZNaWNyb3NvZnQrT2ZmaWNlKzM2NStJZGVudGl0eStQbGF0Zm9ybSZodHRwcyUzYSUyZiUyZmxvZ2luLm1pY3Jvc29mdG9ubGluZS5jb20lMmZsb2dpbi5zcmYmaHR0cHMlM2ElMmYlMmZsb2dpbi5taWNyb3NvZnRvbmxpbmUuY29tJTJmbG9naW4uc3JmXA==; path=/adfs; HttpOnly; Secure
Set-Cookie: MSISAuthenticated=MjguMS4yMDE2LiAxNzozNTowNQ==; path=/adfs; HttpOnly; Secure
Set-Cookie: MSISLoopDetectionCookie=MjAxNi0wMS0yODoxNzozNTowNVpcMQ==; path=/adfs; HttpOnly; Secure
WWW-Authenticate: oYG2MIGzoAMKAQChCwYJKoZIgvcSAQICooGeBIGbYIGYBgkqhkiG9xIBAgICAG+BiDCBhaADAgEFoQMCAQ+ieTB3oAMCARKicARu03ZIshvo2zaqdk/XmgkDMwqT3eyknJWhyB2OkCyulZ52eQEz5c3tLa0Fzf5eY9DO16MBvkV5e008JdyJU9PMy2NfHKlqr0ri1OLAZauuJWNsSFdF4Eh91IzPBH5kyU/eRrQrJC4O5d4HY27vTcY=
Date: Thu, 28 Jan 2016 17:35:04 GMT