Securing Privileged Access - A practical approach
Securing privileged access is a critical first step to establishing security assurances for business assets in a modern organization. The security of most or all business assets in an organization depends on the integrity of the privileged accounts that administer and manage IT systems. Cyber-attackers are targeting these accounts and other elements of privileged access to rapidly gain access to targeted data and systems using credential theft attacks like Pass-the-Hash and Pass-the-Ticket. Protecting administrative access against determined adversaries require you to take a complete and thoughtful approach to isolate these systems from risks.
With that in mind, the team worked hard in the last few months in bringing together a roadmap that is designed to maximize the use of technologies that you may have already deployed, take advantage of key current and upcoming security technologies, and integrate any 3rd party security tools you may already have deployed.
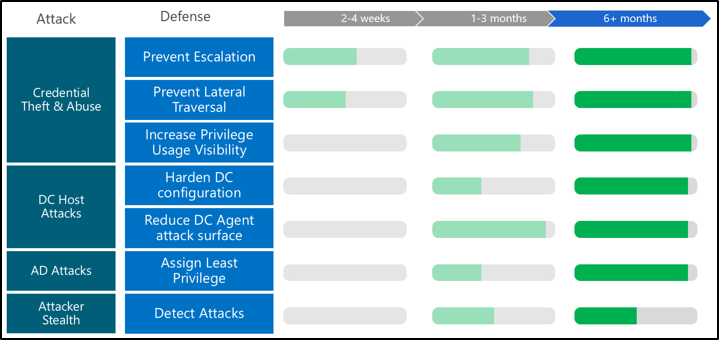
The roadmap of Microsoft recommendations is broken into 3 stages:
- Phase 1: 2-4 week plan – Quickly mitigate the most frequently used attack techniques
- Phase 2: 1-3 month plan – Build visibility and control of admin activity
- Phase 3: 6+ month plan – Continue building defenses to a more proactive security posture
To read the official article on the Roadmap to Secure Privileged Access, check out the TechNet article here.