Certificate Concepts
Hi, Brantley here. I would like to share some information with you about how digital certificates work. Understanding the concepts about how certificates work is important when troubleshooting PKI issues.
Let’s start by defining digital certificate: digital certificates are electronic credentials that are used to assert the online identities of individuals, computers and other entities on a network. The concept of digital certificates is much like the concept of a driver’s license. Like a drivers’ license, a certificate is issued by a central authority that has validated the identity of the person (or computer, application, services, etc) requesting the certificate. Now that we have defined digital certificates let us move on to the details.
Certificate Architecture
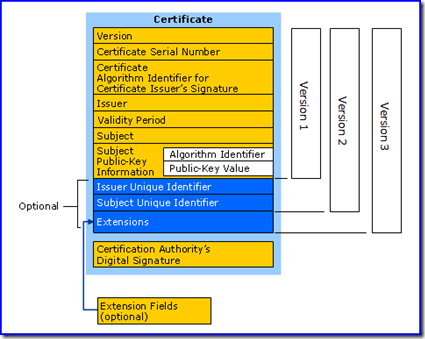
Certificates issued by Windows Server 2003 and earlier are based on standards established by the Public-Key Infrastructure X.509 Working Group of the Internet Engineering Task Force. Version 1 of the standard defines a set of fields that should exist in every X.509 digital certificate. Version 2 added two more fields in order to support X.500 directory access control. Finally, version 3 introduced the concept of a Certificate Extension. Certificate extensions are simply fields that may be specified in standards or may be defined by a registered by a vendor, individual, or community. The Windows Certificate Server included in Windows 2000 and later supports X.509 Version 3 digital certificates.
The format of a v3 digital certificate is illustrated below.
X.509 Version 3 Certificate
- Version: Identifies the version of the X.509 standard to which the certificate adheres. Certificates issued by a Windows CA certificate authority are always v3.
- Certificate Serial Number: A unique identifier for each certificate issued by a particular Certificate Authority. This number must be unique amongst all certificates issued by that CA.
- Issuer: The distinguished name of the CA that issued the certificate. This field identifies the authority responsible for verifying the identity of the Subject of the certificate.
- Subject: The name of the computer, user, network device or service to which the certificate is issued.
- Valid from: The date and time when the certificate becomes valid.
- Valid to: The date and time when the certificate expires.
- Public Key: Contains the public key of the key pair that is associated with the certificate.
- Issuer Unique Identifier: Information that can be used to uniquely identify the issuer of the digital certificate.
- Subject Unique Identifier: Information that can be used to uniquely identify the owner of the digital certificate.
- Extensions: Version 3 certificates include extensions that provide additional functionality and features to the certificates.
As can be seen, a digital certificate links a subject identity and a public/private key in a signed and therefore verifiable digital document.
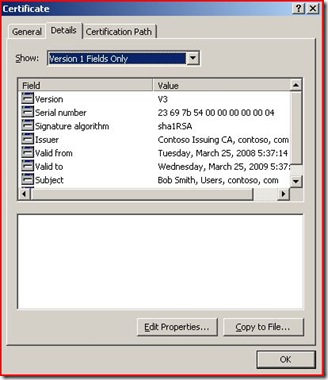
Example User Certificate
When double clicking on a certificate in Windows the Details tab displays the fields mentioned above. This is an easy way of visually verifying the Validity dates and the Subject.
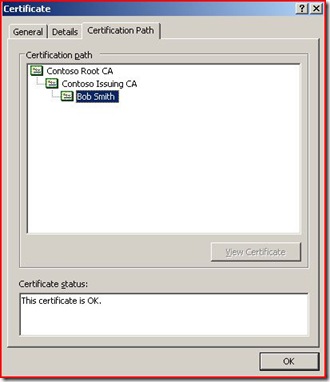
The Certification Path tab displays the certificate path from the root down to the certificate being evaluated.
Basic Certificate Validation:
For a certificate to function properly, the following items must validate correctly (at a minimum):
1. Subject name: The subject of the certificate must match the resource subject that is being used. For example, when using https the subject in the certificate being used on the web server must match the https URL that users will use to connect to the https website. Subject name is analogous to the name on a driver’s license.
2. Validity Period: The (Valid From) and (Valid To) must be within the time frame the certificate is planning on being used. This is much like the expiration of a driver’s license. Validity period is analogous to the expiration date on a driver’s license.
3. Trust: The certificate must be used by a trusted Certificate Authority. Trust is analogous to the State that issued a driver’s license. Because the State that issued the license is a member of the union that makes up the United States we trust the issuer of the license.
4. Chain Building: Chain building is the process of building a trust chain, or certification path, from the end certificate to a root CA that is trusted by the security principal. The chain-building process will validate the certification path by checking each certificate in the certification path from the end certificate to the root CA’s certificate.
5. Key Usage: To help control the usage of a certificate outside of its intended purpose, the optional Enhanced Key Usage extension can be included in the certificate by the CA. The Enhanced Key Usage extension contains a list of usages for which the certificate is valid. These usages, also known as intended purposes, are displayed on the General tab of the certificate dialog box. This is important when evaluating why a certificate may not be working correctly. Key Usage is analogous to driver’s license endorsements (types of vehicles that can be driven with this license).
6. Revocation Checking: Each certificate in the certificate chain is verified to ensure that none of the certificates are revoked. A certificate can be revoked prior to the expiration date to disavow the certificate. Revocation Checking is analogous to checking a driver’s license against a State database to verify that a driver’s license has not been revoked for a violation.
Summary:
Certificates issued by Windows Server 2003 and earlier are based on standards established by the Public-Key Infrastructure X.509 Working Group of the Internet Engineering Task Force. The Windows Certificate Server included in Windows 2000 and later supports X.509 Version 3 digital certificates. Subject Name, Validity Period, Trust, Chaining, Key Usage, and Revocation need to be validated for a certificate to function properly.
- Brantley Whitley